- Home
- Security, Compliance, and Identity
- Microsoft Defender for Endpoint
- Missing Azure Defender GPO Policies missing
Missing Azure Defender GPO Policies missing
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 08 2021 05:52 AM - last edited on Nov 02 2021 03:41 PM by Allen
Hi Community,
I have a problem that I need your help with. I have deployed Azure Defender on Windows Server 2019 servers, running on Microsoft Azure. Azure Security Center is enabled on subscription as also on the Log Analytics Workspace. After the installation, some GPO policies for the configuration of Attack Surface Reduction are missing from the Group Policy Management Editor, I'm missing these policies:
- Windows Defender Antivirus
- Windows Defender Application Guard
- Windows Defender Exploitation Guard
- Windows Defender Smartscreen
Situation
Normally the deployment goes automatically from the Azure Security Center, after setting the status from the option Log Analytics agent for Azure VMs to On from the Auto provisioning blade in the Azure Security Center. But, this implementation is slightly different because there are two virtual servers in this subscription that absolutely should not have Azure Defender installed on them. I have installed Azure Defender by using the 'Using the Local Script' from the deployment method in Microsoft Defender on my Domain Controller. I have checked if Azure Defender is running and the alerts are showing up in my Microsoft Defender Portal.
- Azure Defender Plan is Enabled on subscription level.
- Azure Defender for Servers is Enabled on the subscription level.
- Azure Defender Plan is Enabled on the Log Analytics Workspace.
- Azure Defender for Servers is Enabled on the Log Analytics Workspace.
- The Microsoft.Azure.AzureDefenderForServers.MDE.Windows extension is added to the Virtual Machines.
- The Microsoft.EnterpriseCloud.Monitoring.MicrosoftMonitoringAgent extension is added to the Virtual Machines.
- The integration with Microsoft Defender for Endpoint and Cloud App Security is Enabled.
- In the Inventory blad in the Azure Security Center, I can see that the Virtual Machines are in the Monitored state and that Azure Defender is showing as On.
Do you know why I'm missing those policies? I want to configure Attack Surface Reduction rules in my Windows Server 2018 environment but I'm not able to configure ASR due to the missing GPO policies.
Thanks in advance for your help!
- Labels:
-
Microsoft Defender for Cloud
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 08 2021 06:43 AM
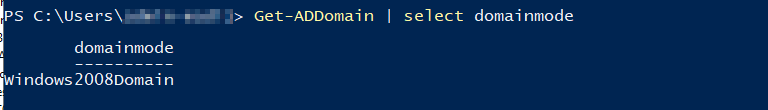
As I continue to troubleshoot, I notice that my ForesMode is running on Windows2008Forest and that the Domain Functional Level is running on Windows Server 2008.
ForestMode
Domain Functional Level
I think that this is maybe part of the problem because the missing policies are part of Windows 10 (and therefore Windows Server 2019). Hence, the Central Store from the Group Policy is missing the Windows Server 2019 templates, could that be the cause of my problem?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 08 2021 10:47 AM
Someone an idea?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 21 2021 07:59 AM
SolutionHi Community!
Meanwhile, I managed to fix this problem. For some reason, the proper admx/adml files were not placed in the SYSVOL\Policies\PolicyDefenitions folder. Maybe it's because of the template we have chosen from the Azure Marketplace or because the Domain- and Forest functional level is still on Windows Server 2008?
My solution
I have fixed this problem by downloadding the Administrative Templates (.admx) for Windows 10 1809 (since 1809 is for Windows Server 2019) and placed the following files in the Central Store (SYSVOL\Policies\PolicyDefenitions):
- WindowsDefender.admx
- WindowsSecurityCenter.admx
- SmartScreen.admx
- AppHVSI.admx
I have of course placed the language (.adml) files in the SYSVOL\Policies\PolicyDefenitions\en-US folder. After reopening the GPMC I've got the right policies in place.
If you are running into this problem, you now know a possible fix.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 21 2021 07:59 AM
SolutionHi Community!
Meanwhile, I managed to fix this problem. For some reason, the proper admx/adml files were not placed in the SYSVOL\Policies\PolicyDefenitions folder. Maybe it's because of the template we have chosen from the Azure Marketplace or because the Domain- and Forest functional level is still on Windows Server 2008?
My solution
I have fixed this problem by downloadding the Administrative Templates (.admx) for Windows 10 1809 (since 1809 is for Windows Server 2019) and placed the following files in the Central Store (SYSVOL\Policies\PolicyDefenitions):
- WindowsDefender.admx
- WindowsSecurityCenter.admx
- SmartScreen.admx
- AppHVSI.admx
I have of course placed the language (.adml) files in the SYSVOL\Policies\PolicyDefenitions\en-US folder. After reopening the GPMC I've got the right policies in place.
If you are running into this problem, you now know a possible fix.