- Home
- Security, Compliance, and Identity
- Microsoft Defender for Endpoint
- Microsoft Defender Signature Update Fallback order for Co-managed Devices
Microsoft Defender Signature Update Fallback order for Co-managed Devices
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 04 2022 02:14 AM
We have a Hybrid Infrastructure and have Windows 10 co-managed devices. AS per consideration we don't allow windows 10 devices to go directly to internet for Signature update as a first fall back. We wanted to do with the SCCM / WSUS server for the first fallback order for definition update. Need assistance on below point.
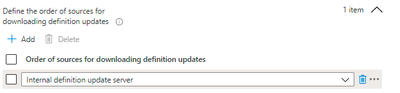
1. how can we define the fallback order as a Internal Definition Server in MS Defender policy from Intune. It showing only Internal definition update server not option to specify the server.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 04 2022 11:06 AM - edited Mar 04 2022 11:10 AM
Internal definition update server setting will use your on-prem WSUS as update source
https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/manage-protection-updates-...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 08 2022 12:37 AM