- Home
- Security, Compliance, and Identity
- Microsoft Defender for Endpoint
- Re: Microsoft Defender for Endpoint Device group question
Microsoft Defender for Endpoint Device group question
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 07 2021 06:15 PM - edited Aug 07 2021 06:28 PM
I know Defender in general is extra user friendly but for the Defender for endpoint to work properly, do I need to put all devices in a machine group and set a remediation level? All the training videos I have watched tells me I have to put the devices in a Device group in settings and set a remediation level. I didn't set it up and it still seems to quarantine unwanted software or malicious software. Can someone why the device group and remediation level are necessary?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 08 2021 12:18 AM
In our scenario we started with Desktops & Server groups with full auto remediation on Desktops and only partial on Servers. Then due to deleted devices being stuck in Defender for at least 30 days we created a Deleted Tag and Group so I could filter them out of our security score and vulnerability exposure score.
Over time we ended up splitting the server groups into two so Critical Services and Non-Critical services had different remediation options. This was just done as a precaution as we wanted to removed the risk of an automatic remediation causing any issues (critical servers are set as "Semi - Require approval for core folders")
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 08 2021 12:29 AM
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 08 2021 12:52 AM
If you decide to create Groups its up to you to define a filter and set the automation response (e.g. none, 2x semi option or full).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 08 2021 02:25 PM
Hey thanks again for responding and I appreciate the help. The device group "1" in the screenshot below is the device group I made and I added most devices in there. The group below that got created after i created "1".
The screenshot below is a different environment with different devices. I did not create any device group there. I do not see a default "undefined" group though. Is it supposed to be like this and the devices are in the undefined group by default without automated response turned on?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 08 2021 05:44 PM
I do recall the reason I started using groups was detections went into a pending action state and I needed selected devices to automatically action threats.
As per my first post I believe you should at minimum define desktops and servers. We used a "Deleted" tag to add removed devices into a separate group so when looking at the security score or threat management dashboard we can filter out deleted devices. In short using tags is an easy way to add devices to custom device groups but please note these group rules need to be above groups that are defined by OS/bud etc only.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 09 2021 06:39 PM
Thanks for confirming that and also the tip. For the customer that isn't using groups, are things working properly for their Defender..? Like alerts coming in, Defender handling alerts, etc.
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 09 2021 07:47 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 10 2021 10:15 AM
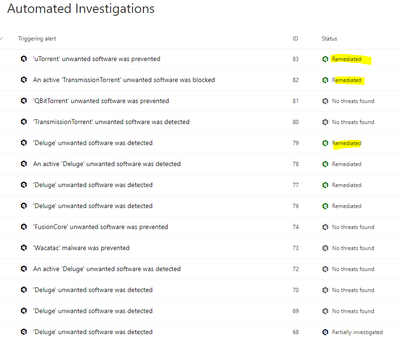
Yeah that makes sense and I was expecting that to happen. The screenshot below is another environment that does not have device group set up. There is not device group or remediation level set up. Do you know why Defender might be remediating them automatically? Could it be because of a PUA policy? I didn't set that up btw.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 15 2021 05:40 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 15 2021 06:00 AM
Turn on automated investigation and remediation
1. As a global administrator or security administrator, go to the Microsoft Defender Security Center (https://securitycenter.windows.com) and sign in.
2. In the navigation pane, choose Settings.
3. In the General section, select Advanced features.
4. Turn on both Automated Investigation and Automatically resolve alerts.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 19 2022 01:33 PM
I know this post is a bit old but thought I would add that the link below does confirm that after August 2020 all new tenants were set to Full Automation by default even without device groups with AIR levels set.
https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/automation-levels?view=o36...