- Home
- Security, Compliance, and Identity
- Microsoft Defender for Endpoint Blog
- Microsoft Defender ATP supports custom IOCs for URLs, IP addresses, and domains
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Microsoft Defender Advanced Threat Protection (ATP) provides a variety of tools to protect you from phishing or malicious sites. There’s Microsoft Defender SmartScreen for Microsoft Edge, and Microsoft Defender ATP network protection for other browsers and HTTP or HTTPS calls outside of the browser. Even with this high-quality protection, Microsoft recognizes that security operations teams need to tailor web and internet protection based on the needs of the organization. You can now do so straight from the Microsoft Defender Security Center console.
This new feature, now in public preview, leverages network protection in block mode and the latest version of the antimalware platform. We recommend that organizations enable network protection in audit mode first, and then move to block mode. Your organization may be using different methods to update the antimalware platform, which may cause some of your client machines to be on different versions of the platform. We recommend that you update all your machines to use this functionality.
Now that we have the prerequisites out of the way, let’s talk about why an organization may need to do this. First, malicious actors use highly tuned social engineering techniques, where a phishing URL or IP address may only be served to a very small set of enterprise users. As a result, hunters in a security operations groups may find malicious URLs before Microsoft and thus need fast tools for shutting them down in their organization. Second, organizations would often buy threat intelligence feeds with malicious URLs and want to use them to augment Microsoft’s threat intelligence. Last, there are times when Microsoft’s intelligence and machine learning may make a malicious verdict for an internet indicator that can impact the productivity of a small set within the organization, such as a security research team. Security operations groups will then want to allow these indicators, so their users can access them.
Getting Started
Let’s get started. To review the URLs, IP addresses, and domains in the allow or block list, follow these steps:
1. Sign into Microsoft Defender Security Center and go to Settings > Rules > Indicators
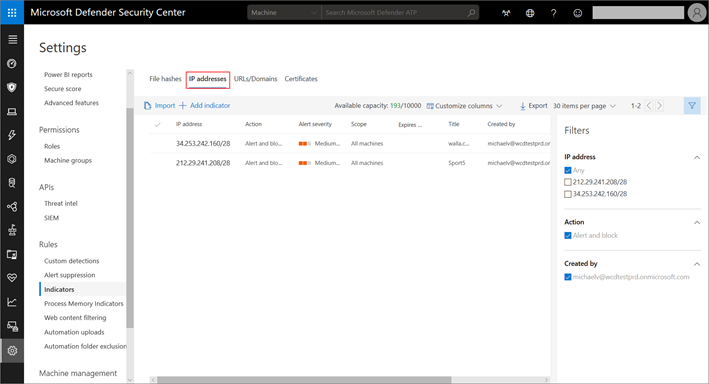
2. Select the IP addresses tab to view a list of IPs
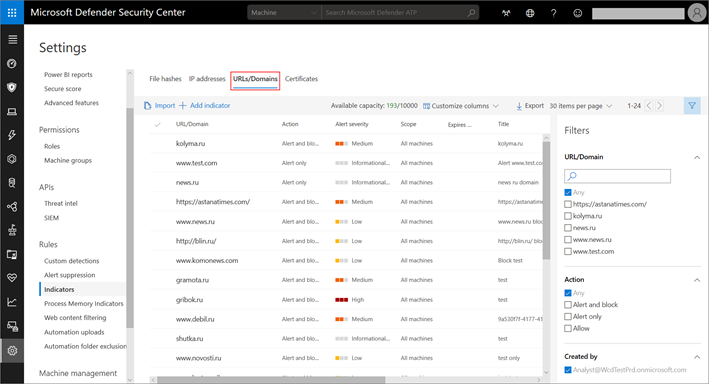
3. Select URLs/Domains to view the list of URLs and domains
To add a URL, IP address, or domain to the block or allow list, follow these steps:
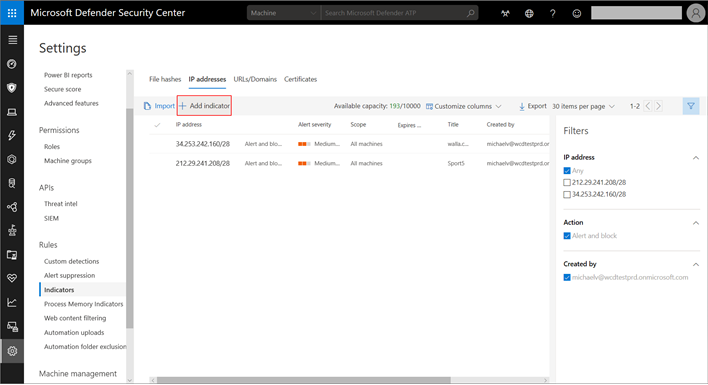
1. From the Indicators setting, navigate to either the IP Addresses or URLs/Domains tab
2. Select Add Indicator from the action bar
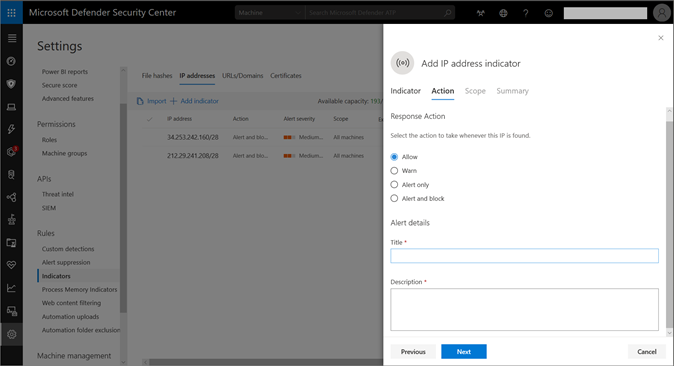
3. Enter the URL or IP address, and select Next
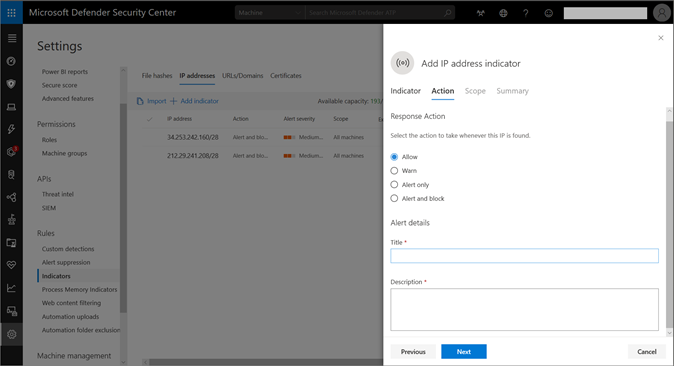
4. Choose from the following actions, enter a title and description for the indicator, and select Next:
- Allow –Allow the URL or IP in the organization, regardless of Microsoft determination
- Alert only – Allow users to access the indicator, but raise an alert
- Alert and block – Block users or processes from accessing the URL or IP address, and raise an alert; show block notification to user with message to contact IT department
- Warn – Notify users when they’re accessing an untrusted URL or UP address, but allow users to dismiss the warning
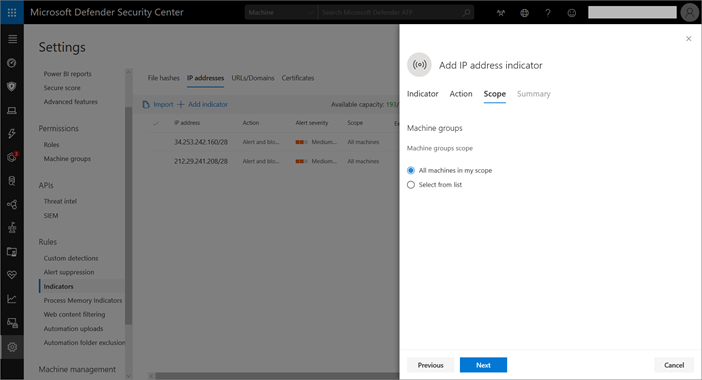
5. Select either All machines in scope or Select from list, which allows you to target a specific machine group, and select Next
6. Select Save
To remove a URL or IP from the block or allow list
1. From either the IP Addresses or URLs/Domains tab, select the indicator you want to delete
2. Select Delete
Microsoft views this capability as a good way to tune your current web protection capabilities. It’s also worth emphasizing that these settings are communicated between the client and Microsoft’s cloud, so it will be in place wherever the device travels – in distributed offices, at airports, or at the local coffee shop. We will continue to iterate here to bring Security Operations more customization of indicators to protect their organizations. We welcome and appreciate your feedback.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.