- Home
- Security, Compliance, and Identity
- Microsoft Defender for Endpoint Blog
- Introducing the new alert suppression experience
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
As a security operations center (SOC) analyst, one of the top issues is triaging the sheer number of alerts that are triggered daily. For lower priority alerts, an analyst is still required to triage and resolve the alert which tends to be a manual process. A SOC analyst’s time is valuable, wanting to focus only on high severity and high priority alerts.
We are excited to share the new and advanced alert suppression experience is now Generally Available. The new experience provides tighter granularity and control, allowing users to tune Microsoft Defender for Endpoint alerts.
Alert suppression provides the ability to tune and manage alerts in advance. This streamlines the alert queue and saves triage time by hiding or resolving alerts automatically, each time a certain expected organizational behavior occurs, and rule conditions are met.
You can create rule conditions based on ‘evidence types’ such as files, processes, scheduled tasks and many other ‘evidence’ types that trigger the alert. After creating the rule, a user can apply the rule on the selected alert or any alert type that meets the rule conditions to suppress the alert.
How to create rule conditions to suppress alerts:
- Select Create suppression rule in the summary details section of the alert page.
- In the Create suppression rule pane, select Only this alert type to apply the rule on the selected alert.
However, to apply the rule on any alert type that meets rule conditions select Any alert type based on IOC conditions.
Note:
You cannot suppress an alert triggered by 'custom detection' source. You cannot create a suppression rule for this alert.
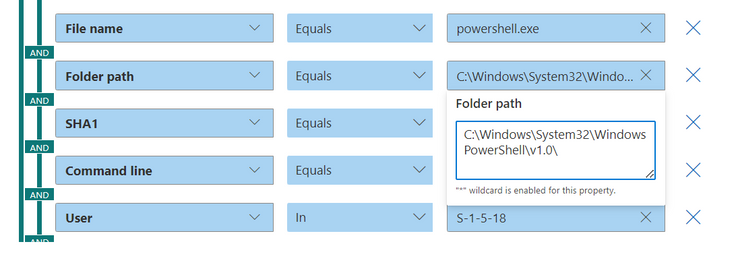
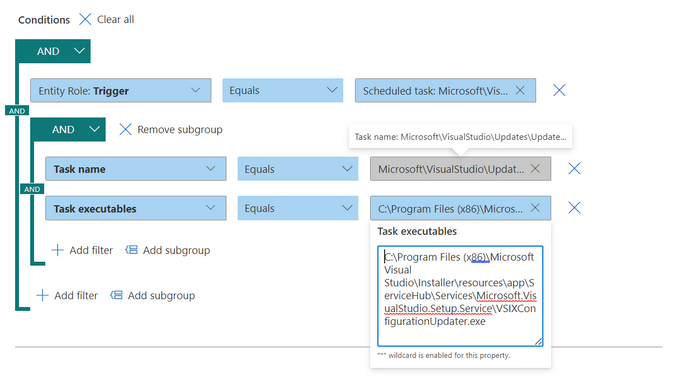
- In the IOCs section, set multiple rule conditions, by selecting Choose IOCs. Use AND, OR and grouping options to build relationship between these multiple evidence types that cause the alert.
- For example, in the Conditions section, select the triggering evidence Entity Role: Triggering, Equals and select the ‘evidence type’ from the drop-down list.
- All the properties of this ‘evidence type’ will auto populate as a new subgroup in the respective fields below.
- You can edit and/or delete properties of this ‘evidence’ as per your requirement (using wildcards, when supported).
- Supporting new additional evidence types:
-
AMSI script, WMI event, and scheduled tasks are some of the new ‘evidence types’ that you can select from the ‘evidence identifier’ drop-down list.
- Click Add filter to add another IOC.
4. Alternatively, you can select Auto fill rule by alert structure in the IOC section to add all alert related ‘evidence’ and their properties at once.
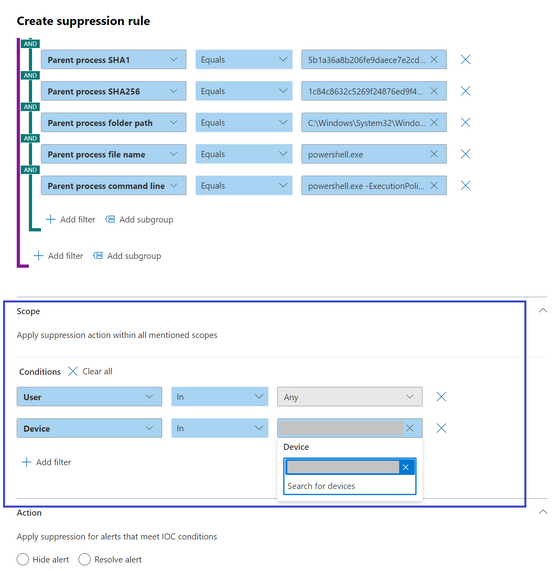
5. In the Scope section, set the Scope by selecting specific device, multiple devices, device groups, the entire organization or by user.
6. In the Action section, take the appropriate action of either Hide alert or Resolve alert. Enter Name, Comment, and click Save.
7. Prevent the IOCs from being blocked in the future:
Once you save the suppression rule, in the Successful suppression rule creation page that appears, you can add the selected IOCs as indicators to the “allow list” and prevent them from being blocked in the future.
8. The new suppression alert functionality is available by default.
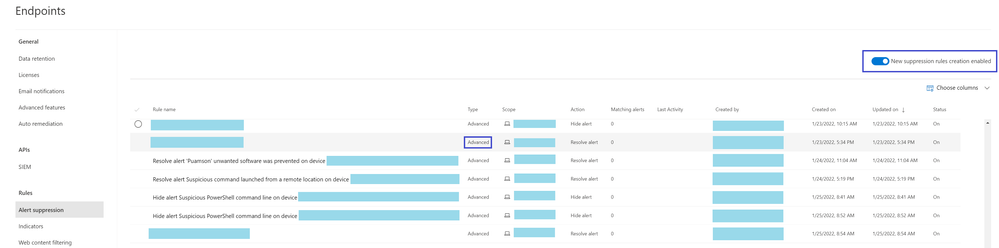
However, you can switch back to the previous experience in Microsoft 365 Defender portal by navigating to Settings > Endpoints > Alert suppression, then switch off the new suppression rules creation enabled toggle.
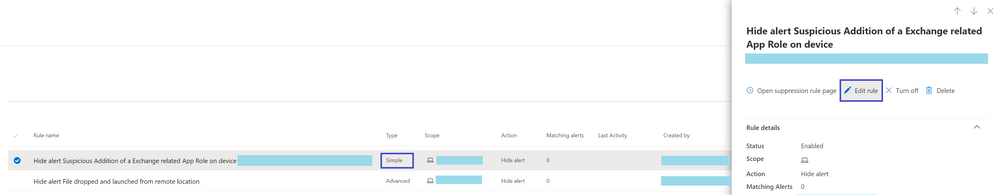
9. Edit existing rules:
You can always add or change rule conditions and scope of new or existing rules in Microsoft Defender portal, by selecting the relevant rule and clicking Edit rule.
To edit existing rules, ensure that the new suppression rules creation enabled toggle is enabled.
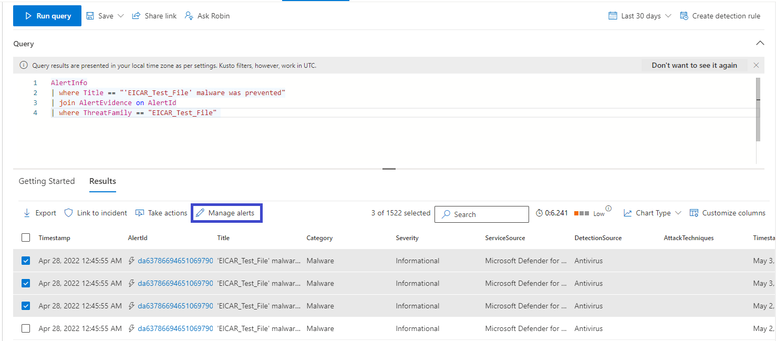
10. Manage alerts retroactively:
Suppression rules apply only on new alerts generated after the rule is created.
To manage existing alerts in bulk, use Advanced hunting query to find the relevant alerts and click Manage alerts to resolve, classify, or assign all of them at once.
We want to hear from you! Let us know what you think of Microsoft Defender for Endpoint’s latest alert suppression experience.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.