- Home
- Security, Compliance, and Identity
- Microsoft Defender Vulnerability Management Blog
- Introducing a risk-based approach to threat and vulnerability management
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
We’re delighted to announce Threat and Vulnerability Management, a new built-in capability that uses a risk-based approach to the discovery, prioritization, and remediation of endpoint vulnerabilities and misconfigurations. This capability is coming to Microsoft Defender Advanced Threat Protection (ATP), our industry-leading unified endpoint security platform with an updated name that reflects the newly announced expanded coverage.
Effectively identifying, assessing, and remediating endpoint weaknesses is pivotal in running a healthy security program and reducing organizational risk. Threat & Vulnerability Management serves as an infrastructure for reducing organizational exposure, hardening endpoint surface area, and increasing organizational resilience. Furthermore, it bridges security stakeholders—security administrators, security operations, and IT administrators—by allowing them to collaborate and seamlessly remediate threats.
Threat & Vulnerability Management is a new component of Microsoft Defender ATP, and provides both security administrators and security operations teams with unique value, including:
- Real-time endpoint detection and response (EDR) insights correlated with endpoint vulnerabilities
- Invaluable machine vulnerability context during incident investigations
- Built-in remediation processes through Microsoft Intune and Microsoft System Center Configuration Manager
How this new Threat & Vulnerability Management changes the game
With Threat & Vulnerability Management in Microsoft Defender ATP, we are introducing a new set of advanced, agentless, cloud-powered capabilities that provide continuous, real-time, risk-based vulnerability management.
Real-time discovery
To discover endpoint vulnerabilities and misconfiguration, Threat & Vulnerability Management uses the same agentless built-in Microsoft Defender ATP sensors to reduce cumbersome network scans and IT overhead, and provides:
- Real-time device inventory. Devices onboarded to Microsoft Defender ATP automatically report and push vulnerability and security configuration data to the dashboard.
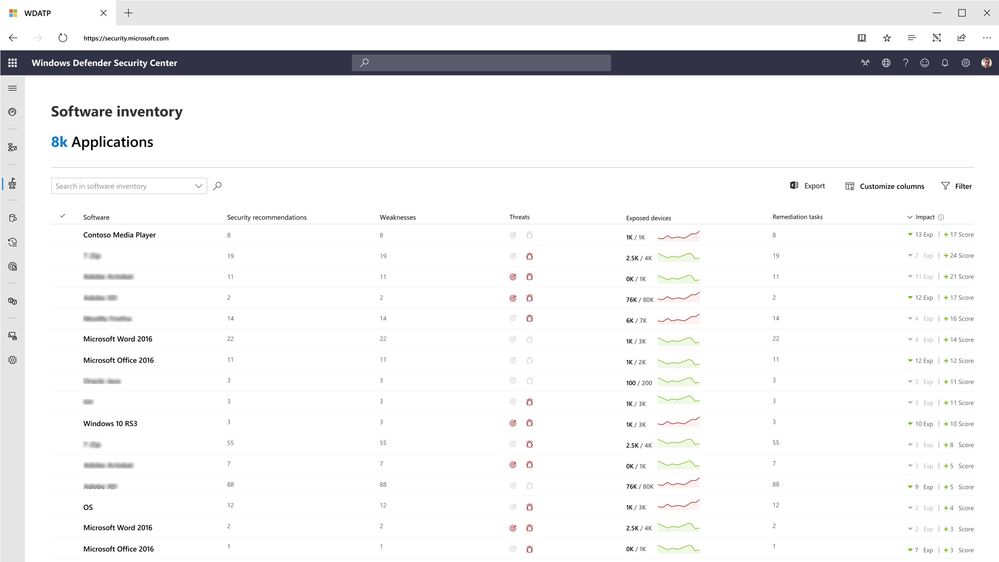
- Visibility into software and vulnerabilities. Optics into the organization’s software inventory, as well as software changes like installations, uninstallations, and patches. Newly discovered vulnerabilities are reported with actionable mitigation recommendations for 1st and 3rd party applications.
- Application runtime context. Constant visibility into application usage patterns for better prioritization and decision-making. Critical dependencies, such as vulnerable runtime libraries being loaded by other applications, are made visible.
- Configuration posture. Visibility into organizational security configuration, surfacing issues like disabled antivirus, enabled SMBv1, or misconfigurations that could allow escalation of privileges. Issues are reported in the dashboard with actionable security recommendations.
Intelligence-driven prioritization
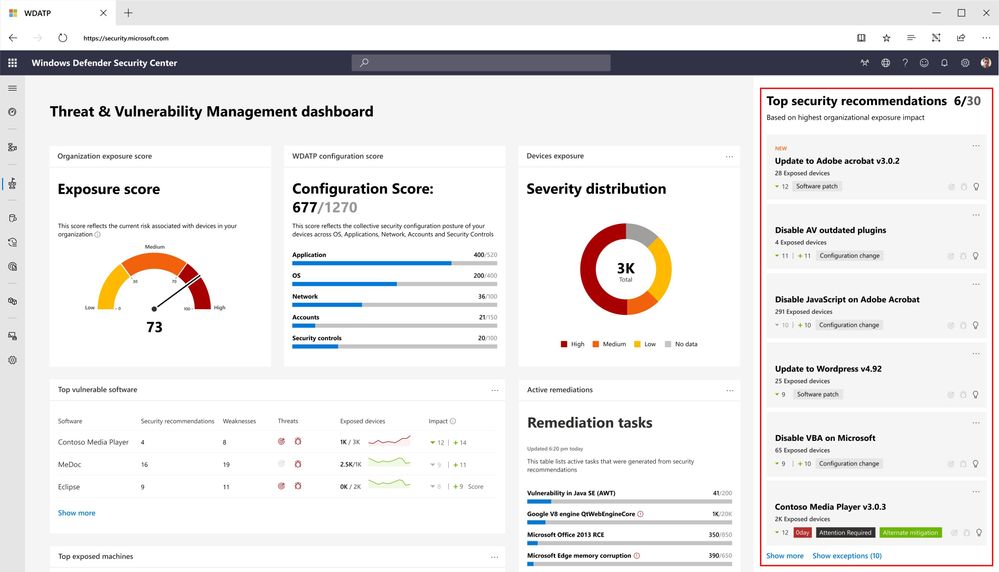
Threat & Vulnerability Management helps customers prioritize and focus on those weaknesses that pose the most urgent and the highest risk to the organization. Rather than using static prioritization by severity scores, Threat & Vulnerability Management in Microsoft Defender ATP highlights the most critical weaknesses that need attention by fusing its security recommendations with dynamic threat and business context:
- Exposing emerging attacks in the wild. Through its advanced cyber data and threat analytics platform, Threat & Vulnerability Management dynamically aligns the prioritization of its security recommendations to focus on vulnerabilities that are currently being exploited in the wild and emerging threats that pose the highest risk.
- Pinpointing active breaches. Microsoft Defender ATP correlates Threat & Vulnerability Management and EDR insights to provide the unique ability to prioritize vulnerabilities that are currently being exploited in an active breach within the organization.
- Protecting high-value assets. Microsoft Defender ATP’s integration with Azure Information Protection allows Threat & Vulnerability Management to call attention to exposed machines with business-critical applications, confidential data, or high-value users.
Seamless remediation
Microsoft Defender ATP’s Threat & Vulnerability Management allows security administrators and IT administrators to collaborate seamlessly to remediate issues.
- One-click remediation requests to IT. Through Microsoft Defender ATP’s integration with Microsoft Intune and System Center Configuration Manager (SCCM), security administrators can create a remediation task in Microsoft Intune with one click. We plan to expand this capability to other IT security management platforms.
- Alternate mitigations. Threat & Vulnerability Management provides insights on additional mitigations, such as configuration changes that can reduce risk associated with software vulnerabilities.
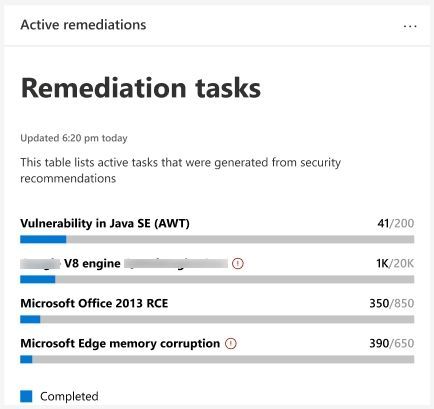
- Real-time remediation status. Microsoft Defender ATP provides real-time monitoring of the status and progress of remediation activities across the organization.
How Microsoft Defender ATP’s Threat & Vulnerability Management works
We designed Threat & Vulnerability Management with the primary goal of helping organizations reduce exposure to threats and increase organizational resilience. To do this, we’re introducing two new metrics:
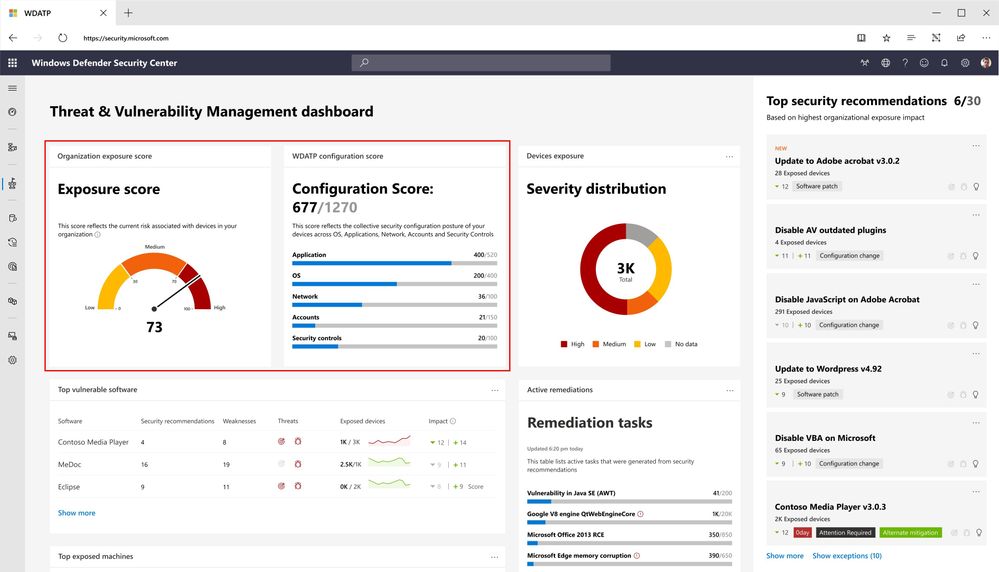
- Exposure score reflects the current exposure associated with devices in the organization based on dynamic vulnerabilities, threat, and business context.
- Configuration score shows the collective security configuration posture of devices based on security best practices.
The Threat & Vulnerability Management dashboard provides real-time visual of these scores, which are continuously assessed based on environmental changes.
The weaknesses identified in the environment are mapped to actionable security recommendations and prioritized by their impact on the organizational exposure score.
Each security recommendation includes an actionable remediation recommendation, which can be pushed into the IT task queue through a built-in integration with Microsoft Intune and SCCM.
The status and progress of these remediation activities can be monitored through the dashboard.
Threat & Vulnerability Management also provides real-time visibility into the software inventory, with important information like vulnerabilities associated with software versions installed on devices, related exploits and threats, and impact to exposure score.
When pivoting to a specific machine, Threat & Vulnerability Management provides machine exposure level, security recommendations, vulnerabilities identified on the machine, and other critical information. This data, together with alerts and incidents data provides security operations with a much clearer picture during incident investigations.
Preview available soon
Threat & Vulnerability Management is just the latest innovation to be added to Microsoft Defender ATP, which continues to evolve to provide customers with powerful, real-time, and integrated means to discover, prioritize, and remediate threats. Customers who have turned on Microsoft Defender ATP preview features will see this game-changing capability in their dashboard within the next month.
Not yet enjoying the benefits of Microsoft Defender ATP’s industry-leading optics and detection capabilities? Sign up for free trial today.
Update (July 2, 2019): General availability
As of June 30, 2019, Threat & Vulnerability Management is generally available. Read the announcement: Microsoft’s Threat & Vulnerability Management now helps thousands of customers to discover, prioriti....
Microsoft Defender ATP team
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.