- Home
- Security, Compliance, and Identity
- Microsoft Defender for Endpoint Blog
- Indicators enhancements: Allow/Block by certificates & more
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Matching Indicators of compromise (IoCs) is essential in every endpoint protection solution. Indicators give SecOps the ability to set a list of IoCs for detection and for blocking (prevention and response).
Today we’re announcing several enhancements to the unified indicators experience:
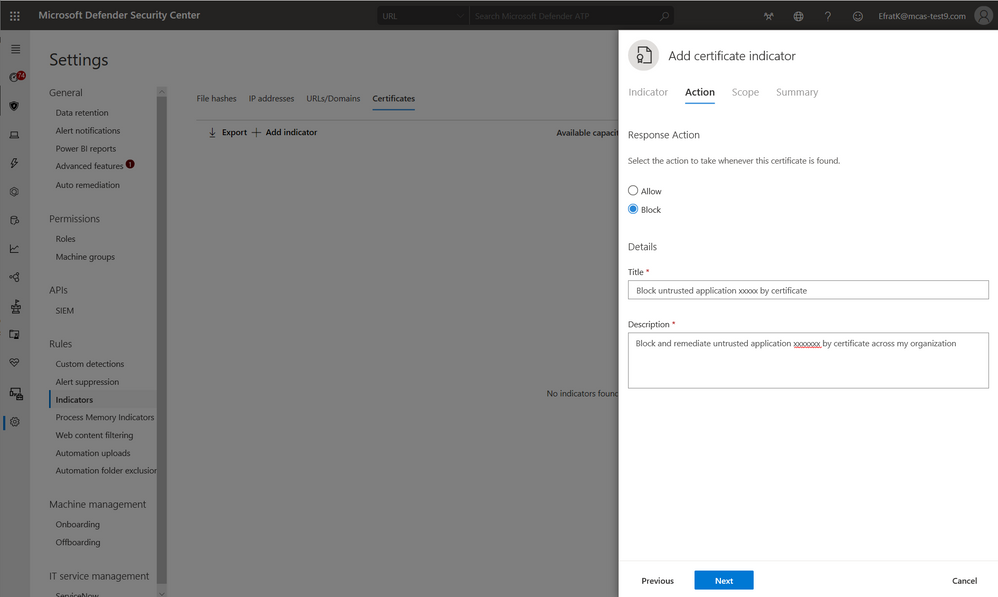
- You can now set an indicator of type certificate that defines the detection, prevention, and exclusion of .
- The “alert and block” action for custom indicators on files can now be applied to files signed by trusted publishers.
- We increased the total limit of indicators across your organization to15,000!
Let’s get started with some suggested use cases.
Allow certificate: attack surface reduction rules
You may want to deploy blocking technologies, such as attack surface reduction (ASR) rules, and allow behaviours or permissions from signed applications to write to protected folders (for example, Controlled Folder Access (CFA)).
Historically, you could only exclude file paths and folders from attack surface reduction rules. Today, you can create exclusions based on certificates.
To try it out:
- Enable the specific ASR rule you would like to apply certificate exclusion for into block mode
- When you execute a file, its activity will be blocked (if block mode was enabled).
- Sign this file with a valid certificate as defined in the prerequisite section.
- In the navigation pane, select Settings >Rules > Indicators.
- Select the Certificate tab
- Add the .CER or .PEM certificate as an indicator with the ‘allow’ action.
- The file’s executable content should now be able to run (i.e. ASR does not block the behavior).
Block certificate
There may be instances when you may want to block the use of a specific signed application across your organization. Using the block certificate action, Microsoft Defender AV will prevent file executions (block and remediate) and the automated investigation and remediation behave the same.
Previously, the automated investigation and remediation engine managed a separate allow / block list for certificates. We have now aligned all detection and enforcement means to honor a single unified list. Your previously set certificate rules have been migrated to the new unified Indicator setting page.
Block files signed by trusted publishers
You may want to block files signed by trusted publishers for scenarios such as when a version of a signed application has a reported vulnerability (CVE). You may also want to prevent the application’s associated file hashes from executing within your corporate environment.
It's important to understand the requirements before creating indicators for files.
For more information, see Create indicators for files.
Microsoft uniquely combines these powerful methods into an integrated approach that protects endpoints more effectively against both malware and breaches. We will continue to iterate these capabilities to bring Security Operations more flexibility in creating custom indicators to protect their organizations.
As always, we welcome and appreciate your feedback!
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.