- Home
- Security, Compliance, and Identity
- Microsoft Defender for Endpoint Blog
- Improving device discoverability and classification using Defender for Identity
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Having visibility into the devices on a network is very important for an organization to help prevent cyberattacks in an ever-expanding threat landscape. Additionally, the more information that can be discovered about the devices, the easier it is to manage them and to protect your network. Having the ability to locate, identify, and accurately classify devices in real-time means you can quickly discover vulnerable devices and carry out intelligent prioritization.
Leveraging Microsoft Defender for Identity as a data source for Microsoft Defender for Endpoint device discovery can help improve discovery coverage and fine tune the classification accuracy.
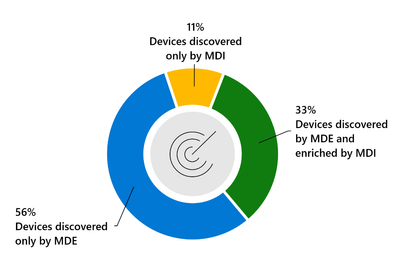
In this blog post, we show how deploying Microsoft Defender for Identity alongside Microsoft Defender for Endpoint can increase both your discovery of devices by ~11% as well as enrich findings by another 33%.
Device discovery
Device discovery is a feature included in Microsoft Defender for Endpoint, which uses passive and active network traffic monitoring to discover and classify new devices on the network. The onboarded devices agent collects this network traffic.
For each newly discovered device, device discovery capabilities attempt to classify information such as device name, device type, OS information, model, and running services.
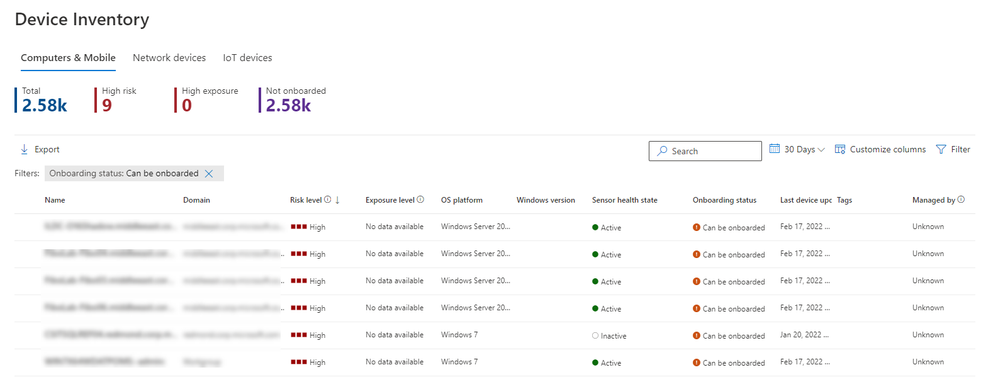
Newly discovered devices will appear in the device inventory tab in the Microsoft 365 Defender portal.
Figure 1 – Device Inventory
You can use the following capabilities to help defend against threats
- Discovering new devices on the network, which can be onboarded to Microsoft Defender for Endpoint.
- Mapping vulnerabilities and unsecure configurations on unmanaged devices
- Detecting and reacting to suspicious network behavior and anomalies coming from specific devices.
Enhance the accuracy of device classification with Microsoft Defender for Identity
Device discovery offers an important turnkey capability that allows for ongoing and precise discovery of devices on the network. On average, organizations will gain extended visibility into 31% newly discovered endpoint devices.
However, there are cases in which identifying and classifying a device based on Microsoft Defender for Endpoint sensor data have a few limitations:
- The visibility perspective – The sensor can only observe network communication between the discovered devices and other onboarded devices. In an instance where there aren’t any onboarded devices on the same network segment as the discovered device, the discovery engine will lack the signals necessary to view that new device. Moreover, the environment hardening / configuration settings (such as firewall access lists, Network Access Translation (NAT)) can further impact the network sensor visibility. As a result, using another independent data source to help enhance visibility could prove beneficial.
- The precision perspective – Windows workstations and servers using only Microsoft Defender for Endpoint might face a challenge in identifying the most accurate and detailed classification for each discovered device. Thus, using a supplemental independent data source can help us distinguish between such cases.
This is where combining Microsoft Defender for Identity and Microsoft Defender for Endpoint can help. Having access to large amounts of high-quality data collected by Microsoft Defender for Identity can significantly improve the classification accuracy of devices detected by Microsoft Defender for Endpoint.
Microsoft Defender for Identity is a cloud-based security solution that leverages your on-premises Active Directory signals to identify, detect, and investigate advanced threats, compromised identities, and malicious insider activity toward an organization.
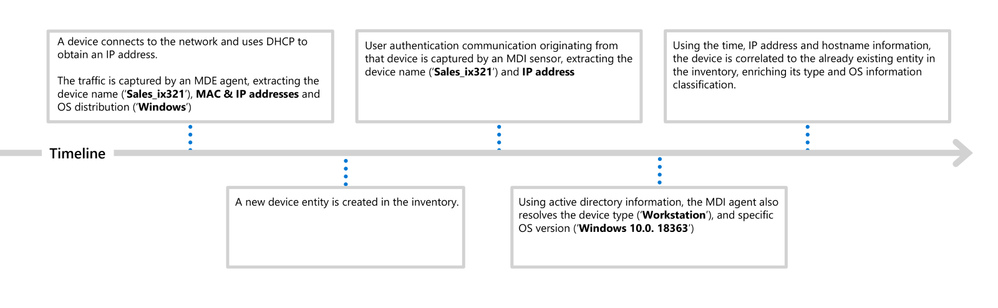
After installation on Domain Controllers, the Microsoft Defender for Identity sensor inspects incoming and outgoing network traffic from within Active Directory. The Microsoft Defender for Identity sensor also collects data from Active Directory logs in order to assess the different users and corresponding devices connected to the domain.
Microsoft Defender for Identity uses this data (device type, OS information, and hostname) in conjunction with device discovery capabilities to enhance classification richness, improve confidence, and provide better visibility
How Microsoft Defender for Identity and device discovery signal correlation works
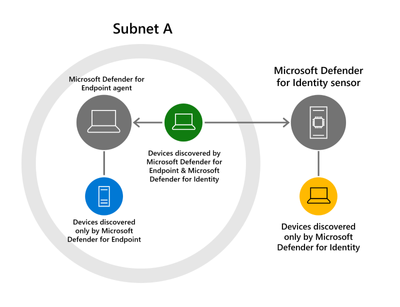
Device discovery capabilities attempt to simultaneously correlate Active Directory user authentication data, which is captured by Microsoft Defender for Identity sensors (which are installed on Domain Controllers) from domain joined devices, with other network traffic communication observed by the Microsoft Defender for Endpoint sensors.
As Microsoft Defender for Identity and Microsoft Defender for Endpoint sensors operate independently, just a single sensor from either or both has the ability to observe each device on a given network. Therefore, by using these tools together, we aim to extract as much discovery and classification data as possible from Microsoft Defender for Identity.
For devices observed by both Microsoft Defender for Identity and Microsoft Defender for Endpoint, we can enrich the device classification for better device discovery accuracy. Furthermore, devices that were only observed by the Microsoft Defender for Identity sensor will populate in the Microsoft Defender for Endpoint device inventory, extending your device coverage.
However, as each product has visibility into different strong device identifiers (for example, MAC address for Microsoft Defender for Endpoint network signals and Active Directory Object GUID for Microsoft Defender for Identity authentication signals), the correlation logic relies on shared properties, such as time, IP addresses and hostnames.
Figure 2 – Microsoft Defender for Identity & Microsoft Defender for Endpoint device discovery
Impact Evaluation
Figure 3 – Product discovery impact
For the average organization, Microsoft Defender for Identity integration increases the number of discovered devices by 11% - these devices benefit from rich classification information.
When looking at the devices that were observed by both Microsoft Defender for Identity and Microsoft Defender for Endpoint, we can see that for 51% of these devices, Microsoft Defender for Identity managed to enrich the Microsoft Defender for endpoint device information, usually with the OS build version (see Figure 4).
For 19% of these devices, Microsoft Defender for Identity helped Microsoft Defender for Endpoint to distinguish between Windows Servers and Windows Workstations which share the same OS build version.
Figure 4 – Discovery timeline
Our data also demonstrated a correlation between a higher number of discovered devices onboarded to Microsoft Defender for Endpoint and a lower number of new devices discovered by Microsoft Defender for Identity.
Figure 5 – Device which was discovered via MDI
Conclusion
Gaining visibility into both your complete asset inventory as well as the rich context of the devices involved has always presented a challenge that remains a top priority for the Microsoft customer support initiative. Last year, we added discovery capabilities to Microsoft Defender for Endpoint, enabling us to start discovering unmanaged endpoints. Since then, we have combined these discovery capabilities with signals from Microsoft Defender for Identity in order to expand overall visibility, improve accuracy and gain a more complete view of all the devices (workstations, servers and mobile) on your network.
Learn more about Microsoft Defender for Identity, and begin a trial for Microsoft Defender for Identity here.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.