- Home
- Security, Compliance, and Identity
- Microsoft Defender Vulnerability Management Blog
- Harden endpoint security for COVID-19 and working from home with Threat & Vulnerability Management
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Attackers have shifted their focus to take advantage of the COVID-19 outbreak. Recent threats have ranged from malicious coronavirus-themed email and social engineering campaigns, to exploitation of endpoint configuration weaknesses on remote worker devices being used outside the normal security-controlled office environment.
While adhering to security best practices is always a good idea, it has now become imperative to harden your organization’s surface area against specific misconfiguration categories that can be leveraged to exploit the increase in remote work such as permissions, remote access control, lockout policies, network shares, security controls, and more.
To help you effectively identify, assess, and remediate these endpoint misconfigurations, the Microsoft Defender Advanced Threat Protection (ATP) research team has added new assessments to our already rich set of existing secure configuration assessments in Threat & Vulnerability Management (TVM), which are geared towards hardening against threats related to the current outbreak.
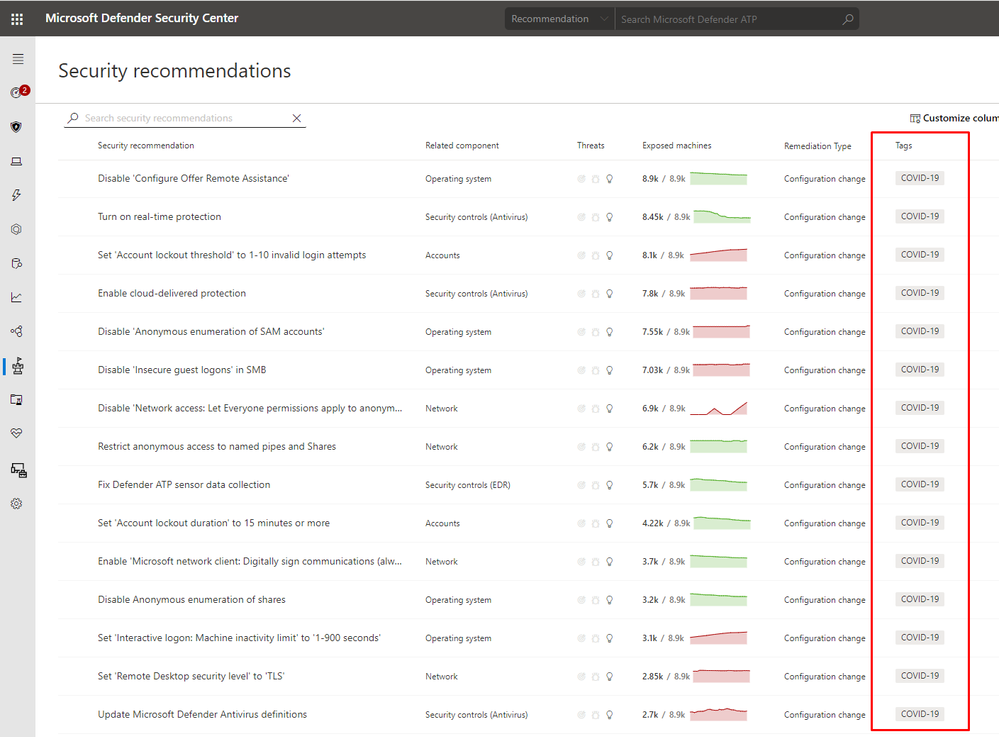
In addition, we are also introducing a new “COVID-19” tag next to each of the COVID-19 related Threat & Vulnerability Management (TVM) security recommendations to help you easily search for these configuration assessments. To see this tag, open the security recommendations page in TVM, and filter to show only the COVID-19 related recommendations.
Continuous vulnerability assessment for remote worker devices
Since Threat & Vulnerability Management isn’t based on periodic scanning, but rather provides continuous endpoint vulnerability assessment based on the built-in OS sensor, our vulnerability assessment will continue to seamlessly work for devices at home in exactly the same manner as it does in the office environment. It can be used to support the ongoing vulnerability assessment and monitoring of Windows patch status, as well as the use of potentially vulnerable applications, and remote collaboration tools that have grown in popularity.
Leveraging advanced hunting
In addition to viewing this new information in the Microsoft Defender Security Center, you can also leverage our advanced hunting capabilities to slice and dice the findings based on your unique needs. Use the following examples below as reference:
- A summary per each COVID-19 related assessment of how many machines are compliant/non-compliant with the recommended configuration, arranged by operating system:
DeviceTvmSecureConfigurationAssessment
| where IsApplicable == 1
| join kind=inner (
DeviceTvmSecureConfigurationAssessmentKB
) on ConfigurationId
| where Tags contains "COVID"
| summarize ConfigurationName=any(ConfigurationName), TotalApplicableMachines=dcount(DeviceId), CompliantMachines=dcountif(DeviceId, IsCompliant == 1), NonCompliantMachines=dcountif(DeviceId, IsCompliant != 1) by ConfigurationId, OSPlatform
| sort by ConfigurationId, OSPlatform asc
- A detailed list of all misconfigured COVID-19 related configurations on all machines:
DeviceTvmSecureConfigurationAssessment
| where IsApplicable == 1 and IsCompliant == 0
| join kind=inner (
DeviceTvmSecureConfigurationAssessmentKB
) on ConfigurationId
| where Tags contains "COVID"
| project DeviceName, OSPlatform, ConfigurationId, ConfigurationName, ConfigurationCategory, ConfigurationSubcategory, ConfigurationDescription, RiskDescription
Additional resources
As our customers continue to adapt to a new norm, we are committed to providing the tools, help, and resources they need to effectively secure their organizations. Take a look below for additional guidance and information that may help.
- Secure your remote workforce with Microsoft Defender ATP
- Microsoft shares new threat intelligence, security guidance during global crisis
Microsoft Defender ATP team
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.