- Home
- Security, Compliance, and Identity
- Microsoft Defender for Endpoint Blog
- Enhanced antimalware engine capabilities for Linux and macOS
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Update: Enhanced antimalware engine for Linux and macOS is now generally available.
The new engine will be gradually rolled out to all devices.
IMPORTANT: Ensure you are applying regular updates. Soon after general availability, app/platform versions older than 101.62.64 (released in February of 2022) will stop getting security intelligence updates.
To ensure Microsoft Defender Antivirus cloud-delivered protection works properly, your security/IT team must configure your network/proxy/internet settings to allow connections between your endpoints and certain Microsoft URLs. To support the new Microsoft Defender for Endpoint on Linux and macOS anti-malware engine enhancements, you must allow-list within the proxy ecosystem in your environment the following URL endpoints:
- go.microsoft.com
- definitionupdates.microsoft.com
- https://www.microsoft.com/security/encyclopedia/adlpackages.aspx
- *.wdcp.microsoft.com
- *.wd.microsoft.com
[How this will affect your organization:]
Starting July 31, 2022, access to these URLs will be *required* to ensure uninterrupted cloud-delivered protection on your Linux and macOS systems behind a proxy. Organizations that have not allow-listed by July 31, 2022, access to the above mentioned URLs will be unable to download threat definition updates required for effective anti-malware protection.
We are announcing a significant upgrade to our next-generation protection on Linux and macOS with a new, enhanced engine.
The Microsoft Defender Antivirus antimalware engine is a key component of next-generation protection. This protection brings machine learning, big-data analysis, in-depth threat research, and the Microsoft cloud infrastructure, to protect devices (or endpoints) in your organization.
The main benefits of this major update include performance and prevention improvements, as well as adding support for custom file indicators on macOS and Linux.
What to expect with this enhancement:
- Better support for protection against known and unknown malware with client-side machine-learning models, heuristics, and correlation between static signals.
- Enhanced cloud-delivered protection with support for metadata-based machine-learning models, file classifications and reputation-based machine-learning models, and more.
- Emergency security intelligence updates are now available through cloud-delivered protection that can help protect against malware outbreaks.
- Better support for false positive and false negative prevention.
- IMPORTANT: Threat naming and definition version nomenclature will change for the purpose of consistency across all platforms and aligning to our overall naming conventions. For more information about how Microsoft names malware, see: Malware names | Microsoft Docs.
- Reduced memory and CPU footprints
- Improved behavior monitoring with lower resource consumption is now available to all our customers as a configurable component for Linux (if enabled).
- Memory scanning, providing better coverage for fileless attacks (Linux).
- Reduced overall package size, significantly reduced security intelligence update download sizes.
- Custom file indicators are now available with “audit”, “allow”, “block & remediate” action . The certificate indicator type will be added at a later date.
Prerequisites
As a preview entry prerequisite, ensure the following requirements are fulfilled:
- During general availability, the new engine will be gradually rolled out to all devices. The process of migration from the old engine to the new engine would last for 3 months
- The minimum Microsoft Defender for Endpoint version number must be 101.62.64 [Feb 2022 build]
- Soon after migration begins, versions older than 101.62.64 will stop getting protection updates
- Organizations which have all devices on a version greater than 101.62.64 would get first preference for the rollout
Key changes to look out for
Custom file indicators
A key feature of the new antimalware engine is the ability to create custom file indicators. You may already have experience with custom file indicators on Windows. The existing three indicator response actions are “allow,” “alert only,” and “alert and block & remediate.” These actions are now supported on macOS and Linux.
Note that warn and block only (block without remediation) indicator types are currently not supported for Linux & macOS. This is visually indicated in the Microsoft 365 Defender portal. In addition, if you have previously created non-scoped custom file indicators (targeted to all devices) in your environment, the indicators will also start applying to any device that is running the new antimalware engine.
Threat nomenclature
The change in threat / malware name is changing to ensure consistency with the standard naming scheme followed across all platforms, including Windows. This is part of the effort for aligning our nomenclature across all platforms and having a standardized naming mechanism.
Threat names will now follow this format:
<Category>.<Platform>.<Family>.<Variant> ---> [Threat Type]:[Platform]/[Malware Family].[Variant]?![Suffixes]?
Examples:
|
Previous engine syntax |
New engine syntax |
|
Linux |
|
|
Trojan.Linux.Mirai.1 Gen:Variant.Backdoor.Linux.Gafgyt.1 Gen:Variant.Backdoor.Linux.Tsunami.1 Gen:Variant.Trojan.Linux.Gafgyt.5 Trojan.Linux.Xorddos.B Gen:Variant.Application.Linux.Miner.3 |
Backdoor:Linux/Mirai.YA!MTB DDoS:Linux/Gafgyt.YA!MTB Backdoor:Linux/Tsunami.DS!MTB Backdoor:Linux/Gafgyt.cf!MTB Trojan:Linux/Xorddos Trojan:Linux/CoinMiner.N!MTB |
|
macOS |
|
|
Gen:Variant.Adware.MAC.AdLoad.1 Adware.MAC.Bundlore.EJL Adware.MAC.Generic.23253 Trojan.MAC.Lazarus.G |
PUA:MacOS/Adload.L!MTB Adware:MacOS/Multiverze PUA:MacOS/Maltiverza Trojan:MacOS/NukeSped.A!MTB |
Microsoft Defender for Endpoint threat list output
Some examples of the updated threat names when displayed through command line:

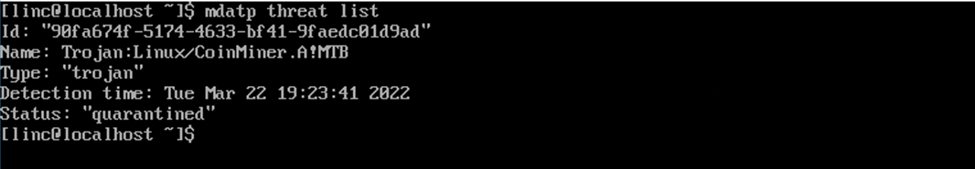
User Interface (macOS)
The following screenshot shows alerts will use the updated threat names in the user interface:

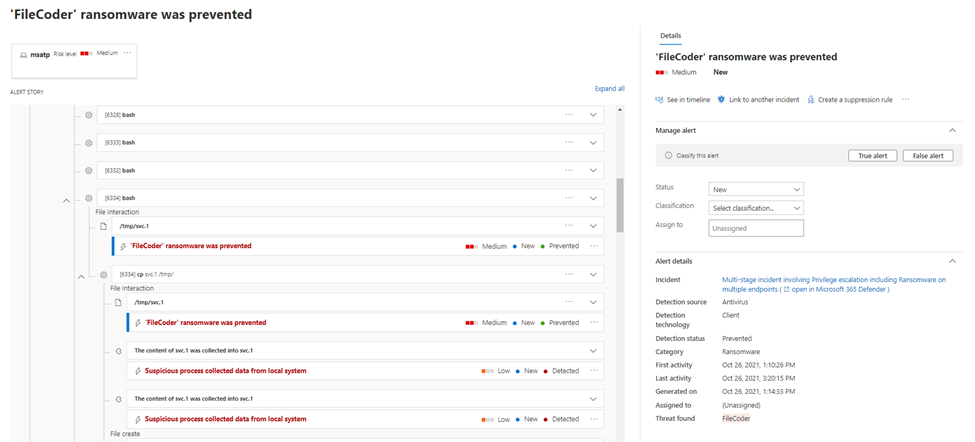
Microsoft 365 Defender portal
Alerts will use the updated threat names in the Microsoft 365 Defender portal.
For example:

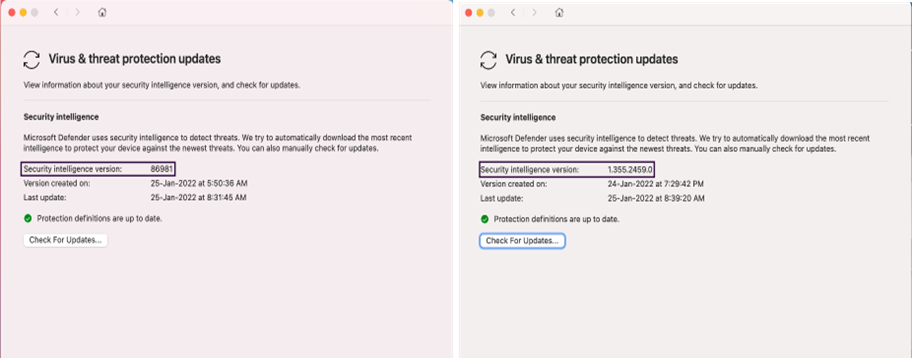
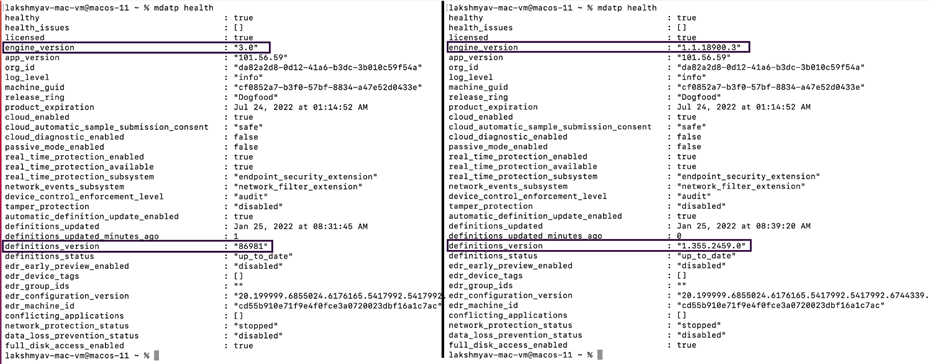
Version numbers
The format of ‘Security intelligence version’ under the About tab and Virus and threat protection updates in the macOS Microsoft Defender interface and using the Linux command line interface will now display a different version numbering scheme.
Security Intelligence/definitions version example: 1.355.2459.0
Engine version example: 1.1.18900.3

Exceptions / Rules configured based on threat names
In the previous engine capability, if any rule has been configured (using “mdatp threat allowed” command) to allow threats based on the threat family name, those rules will not be in effect with the new engine. New rules will have to be created with the corresponding new threat family names. For example, in case of EICAR threats:
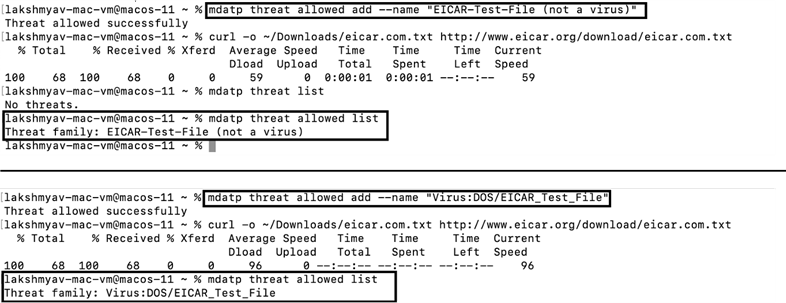
IMPORTANT: Action might be needed
- Ensure your proxy solution allows access to security intelligence and cloud protection locations. Some of these locations were previously listed as "optional" and applied primarily to Windows, at Configure device proxy and Internet connection settings | Microsoft Docs.
- Threat exclusions defined using the old naming convention will need to be updated. In addition, if you have any scheduled queries based on the threat name, you may need to revise them.
Note: In addition to setting exclusions for files that may no longer be covered by allowed threat configuration, you can now also use custom file indicators with the “Allow" action type as a mitigation.
We welcome your feedback and look forward to hearing from you! You can submit feedback through the Microsoft 365 security center.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.