- Home
- Security, Compliance, and Identity
- Microsoft Defender for Endpoint Blog
- Discovering internet-facing devices using Microsoft Defender for Endpoint
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Last year, we announced the evolution of the device inventory view in Microsoft Defender for Endpoint. The revamped device inventory view gave SOC analysts visibility into all discovered devices, counts and functional features (such as, search) that enhanced the overall user experience. To build on top of this work, we are expanding our device discovery capabilities through our existing network telemetry and RiskIQ integration. We’re thrilled to announce the ability to discover internet-facing devices is now in public preview.
Threat actors are constantly scanning the internet to identify exposed devices, whether it’s part of an opportunistic malicious activity or a wider targeted campaign. These devices serve as highly accessible entry points to an organization’s environment. Mapping your organization’s external attack surface is a key part of security posture management. However, security teams are faced with the challenges of identifying and prioritizing exposed devices to address the greatest threats on their most critical devices.
To help organizations extend their threat protection across internet-facing devices, Microsoft Defender for Endpoint will automatically map and flag onboarded devices that are exposed to the internet in the Microsoft 365 Defender portal, providing more context to security teams and deeper insights into device exploitability. By providing a view into internet-facing devices, security teams can better prioritize alerts, recommendations and incidents as internet-facing devices oftentimes become an adversary's entry point into the corporate network.
New capabilities to map internet-facing devices
Mapping internet-facing devices is often challenging since there is not a single indicator or logic used to determine that a device is accessible from the internet. With many organizations using public IP ranges, numerous data sources, and classification logics to cross-reference their devices, these varying methodologies make it more difficult for admins to gather the visibility and verify the accuracy of the insights generated across their digital estate. With the new capabilities in Microsoft 365 Defender, we can leverage our existing Microsoft Defender for Endpoint telemetries and integration with RiskIQ to map internet-facing devices through a standardized approach that helps gather these insights with precision and less manual effort.
Integration with RiskIQ
RiskIQ has catalogued the services, applications, and devices exposed on the IPv4 Internet. By leveraging the integration within Microsoft Defender for Endpoint, administrators are able to identify the exact devices that are internet facing. In addition to gaining visibility into internet-facing devices, the RiskIQ integration works hand-in-hand with Defender for Endpoint’s network traffic parsing capability, to provide concrete evidence of network exposures through the obscured view of the NAT.
Relying on Microsoft Defender for Endpoint Signals
The device network connections captured as part of Microsoft Defender for Endpoint signals help to identify internet-facing devices. Using this information, we can identify which external, incoming connections indicate a machine to be facing the internet.
To identify the external IPs that are communicating with internal devices, we need to determine which subnets are part of the corporate network. We can see subnets for machines that are protected by Defender for Endpoint. This information helps to determine whether a connection captured by Microsoft Defender for Endpoint is internal, or external.
Let’s take a look at the user experience
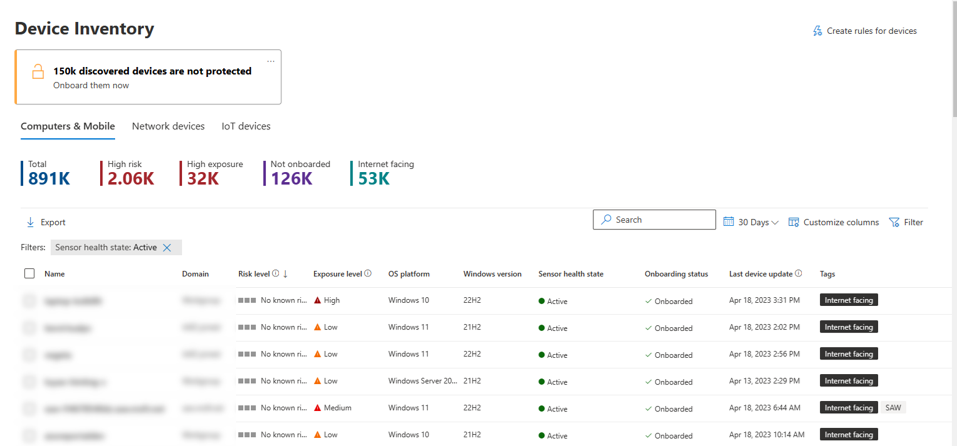
The classified internet-facing devices will appear with the corresponding tag in the device inventory and will also be available via Advanced Hunting.
Notice how the internet-facing devices which were publicly scanned and masked behind the NAT configuration, can now be observed as part of the below query results.
Figure 2 - Querying for internet facing devices via Advanced Hunting
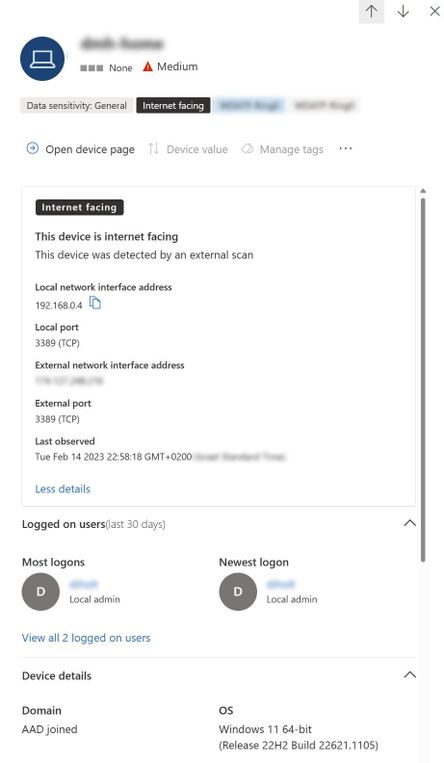
The device pane now shows the internet-facing properties:
Figure 3 - Device pane
Try this for yourself by using this example query which returns the latest results on internet-facing devices:
DeviceInfo
| where Timestamp > ago(7d)
| where IsInternetFacing
| extend InternetFacingInfo = AdditionalFields
| extend InternetFacingReason = extractjson("$.InternetFacingReason", InternetFacingInfo, typeof(string)), InternetFacingLocalPort = extractjson("$.InternetFacingLocalPort", InternetFacingInfo, typeof(int)), InternetFacingScannedPublicPort = extractjson("$.InternetFacingScannedPublicPort", InternetFacingInfo, typeof(int)), InternetFacingScannedPublicIp = extractjson("$.InternetFacingScannedPublicIp", InternetFacingInfo, typeof(string)), InternetFacingLocalIp = extractjson("$.InternetFacingLocalIp", InternetFacingInfo, typeof(string)), InternetFacingTransportProtocol=extractjson("$.InternetFacingTransportProtocol", InternetFacingInfo, typeof(string)), InternetFacingLastSeen = extractjson("$.InternetFacingLastSeen", InternetFacingInfo, typeof(datetime))
| summarize arg_max(Timestamp, *) by DeviceId
The results here will provide streamed instances of the internet-facing devices with their aggregated evidence in the “AdditionalFields” column.
For example:
InternetFacingLastSeen – last time the device was updated as internet facing.
InternetFacingReason – the detection method used to identify internet facing.
InternetFacingPublicScannedIp – what the external address is, in case NAT was detected.
Resources
For those looking to learn more about device discovery, here are some additional resources you can explore.
- Learn more about Investigating internet-facing devices
- Learn more about Microsoft Defender Device Discovery
- Learn more about Network Device Discovery
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.