- Home
- Security, Compliance, and Identity
- Microsoft Defender for Endpoint
- ASR - Behavior Changes - Blocking under User Context Now?
ASR - Behavior Changes - Blocking under User Context Now?
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 02 2022 05:50 PM - edited Aug 02 2022 05:54 PM
Since July 7-27-2022
I have been seeing around 40 of 1800 machines in my work environment that are showing blocks under %userprofile% or usercontext for .dll blocks. This is new behavior and is recent. All of our machines have the same ASR rule applied, I checked on the machines via registry and their ASR rules are the same.
ASR Rule/Example Path - that is having this issue
Block executable content from email client and webmail
GUID: be9ba2d9-53ea-4cdc-84e5-9b1eeee46550
Path: %userprofile%\AppData\Local\Assembly\tmp*variousfilesandpaths.dll
Did this behavior change, is this a preview of a new feature or is this a bug? I am afraid this may spread to more machines.
We have E5 License and an MS Ticket Open as well. Hoping someone hear knows something as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 12 2022 07:24 AM
"WDSI Security Intelligence team have gotten back to me and provided the following solution:
We have reviewed the reported issue, and this is known issue
• And regarding ASR issues related to Block executable content from email client and webmail we have provided global fix. The changes will be reflected in the security intelligence version 1.373.181.0 or above. So, we request you to update to the latest security intelligence version and verify the issue. "
so after updating a problem client indeed it changed. we get an all new error message and block event in the defender report.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 12 2022 07:37 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 12 2022 08:45 AM
Good to know, i did not get any events in the last hours, but lot people are probably enjoying the weekend already.
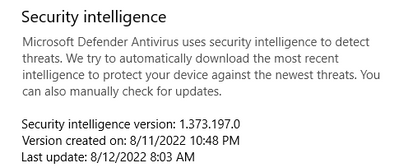
To check which version is installed on the computer, run the following Powershell Command:
Get-MpComputerStatus | fl *version*
To force an update of the signatures, run the following commands in an elevated command prompt (source: https://www.microsoft.com/en-us/wdsi/defenderupdates:(
cd %ProgramFiles%\Windows Defender
MpCmdRun.exe -removedefinitions -dynamicsignatures
MpCmdRun.exe -SignatureUpdate
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 12 2022 08:58 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 12 2022 09:03 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 12 2022 09:33 AM - edited Aug 12 2022 09:36 AM
Windows 10 Settings > Windows Security > Open Windows Security > Click "Check for Updates" under Virus & threat protection updates.
Edit: So far the updated definition has not helped we are now seeing improvements, however it seems like they are still making adjustments.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 12 2022 01:58 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 15 2022 01:07 AM
some users that had problems dont have them anymore
in reports -> ASR rules i also dont see any more blocks of our 3rd party software in "block exe content from email and webmail" so bit early to be sure but for now it looks like all is fixed for us
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 15 2022 01:50 AM
Solution- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 15 2022 05:45 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 16 2022 03:51 AM
We can carry out manual Defender updates and reboots. In the meantime, can you advise if we need to do anything else to remove these false-positive detections please?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 16 2022 05:13 AM
You may need to review your ASR rules though and see if other rule types are causing the block, then in that case you may still need to create special exclusions for that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 16 2024 12:12 AM
could that be a possible regression?
- « Previous
- Next »