- Home
- Security, Compliance, and Identity
- Microsoft Defender for Endpoint Blog
- Announcing a global switch for tamper protection
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Advanced breaches like human-operated ransomware campaigns and NOBELIUM continue to pose significant risks to businesses. Most of these breaches involve tampering with security solutions and settings. To defend against these types of breaches, it's clear that tamper protection in Microsoft Defender for Endpoint should be turned on for all devices. Tamper protection helps prevent bad actors from disabling security features, such as antivirus protection, on your devices.
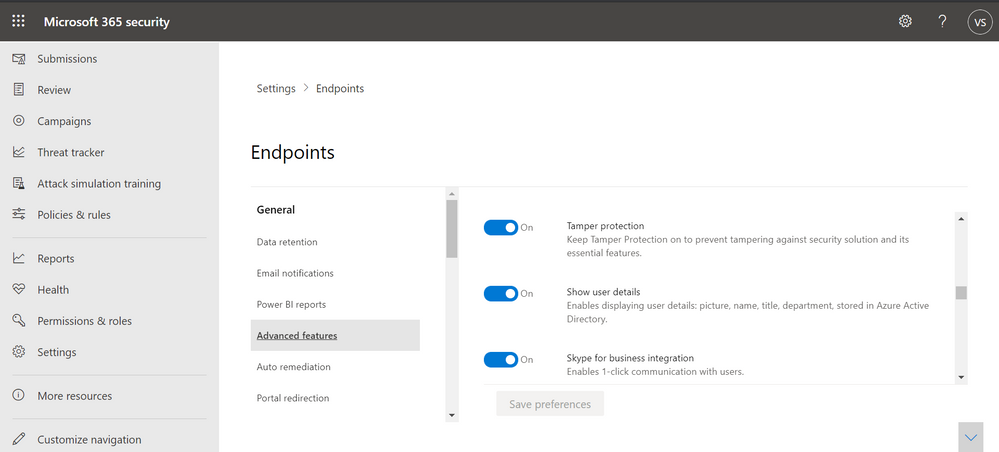
Last year, we announced support for tamper protection on Configuration Manager managed devices (using tenant attach). Now, we are excited to announce that you can use the Microsoft Defender Security Center or Microsoft 365 security center to manage tamper protection for your organization. The update helps ensure that all devices onboarded to Microsoft Defender for Endpoint have tamper protection turned on, and is applicable for both active- and passive-mode devices.
TIP: If you are managing devices in a hybrid environment, or you need more granular control than a tenant-wide setting, continue using Intune or Configuration Manager. We recommend keeping tamper protection turned on, tenant wide. To do that, you can use the Microsoft Defender Security Center or the Microsoft 365 security center, our unified secops experience.
You shouldn’t need to exclude devices from tamper protection; however, if your organization wants to exclude devices, use the Microsoft Endpoint Manager admin center. To learn more, see Exclude groups from a profile assignment.
Currently, the option to manage tamper protection in the security centers is on by default for new deployments. For existing deployments, tamper protection is available on an opt-in basis, with plans to make this the default method in near future.
To learn more, see our documentation about how to Manage tamper protection using the security center. These instructions apply to both the Microsoft Defender Security Center and the Microsoft 365 security center.
There’s more to come!
Additional resources:
- Documentation: Protect security settings with tamper protection
- Tech Community blog: Tamper protection is now generally available
- Tech Community blog: Enable tamper protection in Threat & Vulnerability Management
- Tech Community blog: Announcing tamper protection for Configuration Manager tenant attach clients
Microsoft Defender for Endpoint is an industry leading, cloud powered endpoint security solution offering vulnerability management, endpoint protection, endpoint detection and response, and mobile threat defense. With our solution, threats are no match. If you’re not yet taking advantage of Microsoft’s unrivaled threat optics and proven capabilities, sign up for a free Microsoft Defender for Endpoint trial today.
Microsoft Defender for Endpoint team
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.