- Home
- Security, Compliance, and Identity
- Microsoft Defender for Cloud Apps
- Re: you dont have any apps deployed with conditional access app control
you dont have any apps deployed with conditional access app control
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 28 2021 09:04 AM
Hi All,
I'm new to m365 and I have something confusing me because I cant find a solution to it, I searched the internet I found Just one post regarding the error :
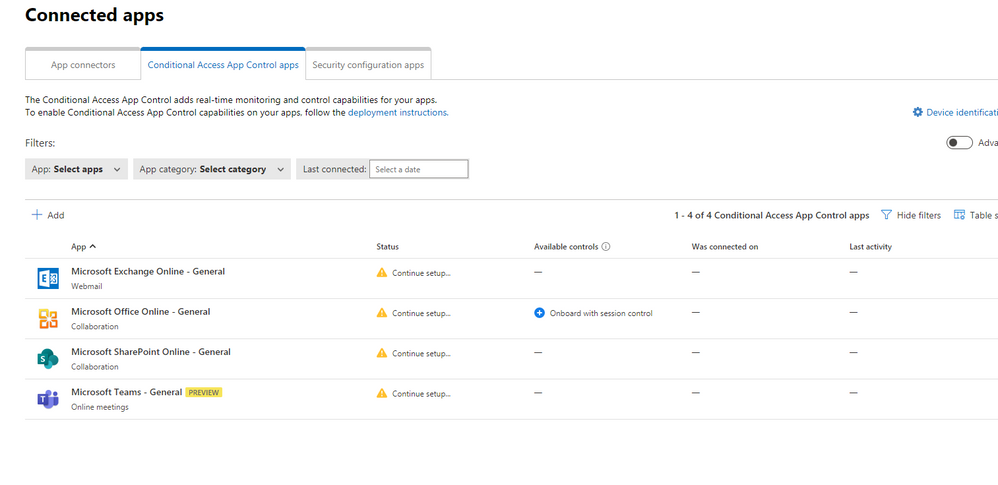
my problem is how I add exchange teams or office 365 to Conditional access app control,
investigate > connected apps > Conditional Access App Control
I add them, but the setup is incorrect asking me all the time to continue setup, please help with it, to configure this step, I searched all the internet cannot find the wright way too add app
what I need to do a session policy from azure security > conditional access >use custom policy
the custom session policy from defender for cloud app asking me that you dont have any apps deployed but when adding exchange or teams share point
please review the picture
I will attache a picture describe the problem
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 29 2021 02:08 AM
Can you please share the goal that you want to reach with your configuration? It will be better to help you if we know your use case.
If it is to secure the access to O365, you can do that with the Conditional Access blade located in Azure Active Directory.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 29 2021 09:33 AM
Hi Dear, @NicolasHon
Yes you are wright I can use Conditional Access but when I need to configure (use custom policy tab) its till me :Custom policies need to be configured in Cloud App Security portal
I've watched a lot of video that teach how to use a MCAS, like how to block access or download from non compliance or even compliance device if the document match the session policy for specific criteria like National ID or any other specific world .
to configure these policy through Microsoft defender for cloud apps you must first configure :
connected apps > then Conditional Access App Control .
I added Microsoft office online ,Microsoft exchange online , Microsoft share point online , and team.
there is no help how to configure and add those apps to Conditional Access App Control . I need help to configure these apps to allow defender for cloud app to connect . there is no explanation into internet . could you please help me
I read a lot of articles at Microsoft also there is no data specifically for add what I mention above
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 31 2021 02:11 AM
Did you try to open a ticket by Microsoft? I've always had good experiences with the support for Azure.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 01 2022 12:01 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 12 2022 07:25 AM - edited Jan 12 2022 07:27 AM
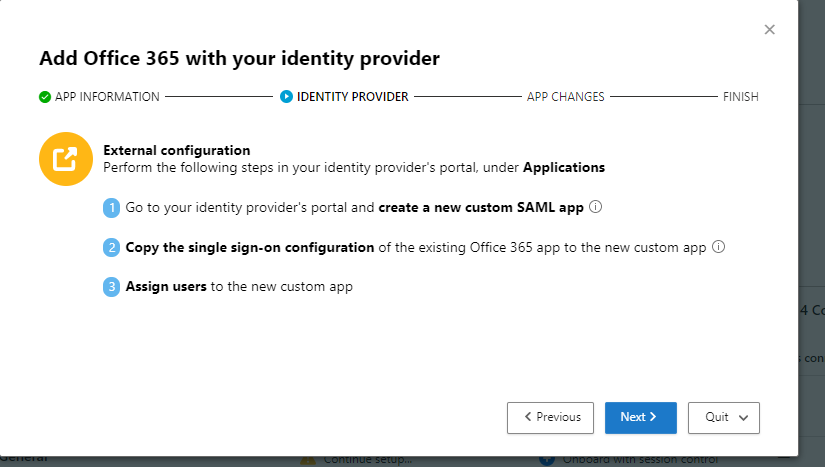
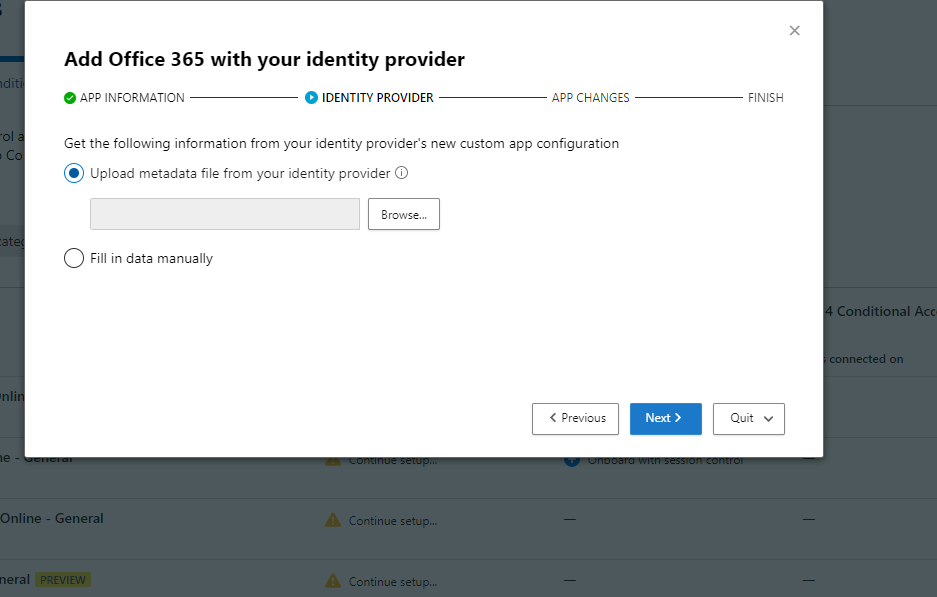
For apps on this list, you must follow these instructions. For all other apps, you must follow these instructions.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 12 2022 01:31 PM
Thank you for your replay
I read this article before how to add app to conditional access
https://docs.microsoft.com/en-us/defender-cloud-apps/proxy-deployment-aad
what I need? there is no exact article explaining how to add your office 365 subscription { exchange , teams , etc} to ((( Conditional Access App Control Apps)))
Like what I will show you in image I searched all the internet no one discussing
Just I need my office apps you can find how to add google amazon and a lot of product but not your office app
I know that I need to create a conditional access session policy, but after that you need some apps to work with defender for cloud apps
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 25 2022 07:02 AM
Yes, I could see how that is confusing.
Since O365 apps are already configured to use Azure AD as the identity provider (IDP), you can still use the instructions for featured apps, but skip straight to step 2.
Hope that helps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 10 2023 01:05 AM
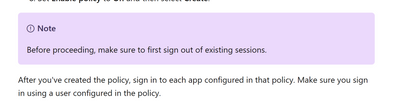
I had the same issue , it turns out it will not detect the App until after you trigger conditional access on the App , so you must sign in to the App with a user that is applying to the policy.
You will need to wait for a couple of minutes for this to take effect , you can also inspect the sign-in logs of the user from Azure AD portal to make sure that the conditional access policy is applied to the sign-in attempt.
This is mentioned in the docs
Regards
Amr