- Home
- Security, Compliance, and Identity
- Microsoft Defender for Cloud Blog
- New OpenSSL v3 vulnerability: prepare with Microsoft Defender for Cloud
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
New OpenSSL v3 vulnerability: prepare with Microsoft Defender for Cloud
On November 1st, the OpenSSL team published two high severity vulnerabilities: CVE-2022-3602 and CVE-2022-3786. All OpenSSL versions between 3.0.0 and 3.0.6 are affected and OpenSSL 3.x users are encouraged to expedite the upgrade to OpenSSL v3.0.7 to reduce the impact of these threats.
The vulnerability is a Denial of Service (DoS) for systems that support client certificate-based authentication. An attacker could send a maliciously crafted certificate to a server that parses certificates as part of client authentication and crash the server or execute remote code when it processes the malicious certificate. Currently, we are not aware of any working exploit that could lead to code execution.
What is the impact and how do I identify and mitigate risk?
Microsoft Defender for Cloud telemetry shows that OpenSSL v3 (containing the vulnerability) is significantly less prevalent than earlier OpenSSL versions, which are not impacted by this vulnerability.
Microsoft Defender for Cloud has multiple ways to quickly determine whether your environment is vulnerable and to help prioritize your actions:
- Prioritize remediation for workloads that pose the greatest risk to your organization using attack path analysis, which provides visibility into the impacted workloads that are exposed via the internet and with the potential for lateral movement. To aid analysis, we have added a specific type of attack path for the OpenSSL v3 vulnerability.
- Hunt for all impacted workloads using the cloud security explorer, which enables you to query all workloads impacted by the OpenSSL v3 vulnerability and gain additional context for prioritization.
- Use vulnerability assessments for VMs, containers, and container images,
Prioritize remediation of your riskiest workloads using attack paths
Note: To hunt for impacted workloads, first enable in Microsoft Defender for Cloud the new Defender CSPM service and Defender for Containers if you have containerized workloads. For more details on enabling these services, click here for Defender CSPM and here for Defender for Containers.
To identify Internet exposed machines and containers with vulnerable OpenSSL versions, we have added new attack paths for Azure VMs, AWS EC2, and internet exposed pods.
- Sign in to the Azure portal.
- Navigate to Microsoft Defender for Cloud > Recommendations > Attack path
Figure 1: Attack path access
- Expand any of the attack paths related to OpenSSL v3, for example:
Figure 2: Vulnerable OpenSSL 3.x EC2 instances Attack Path
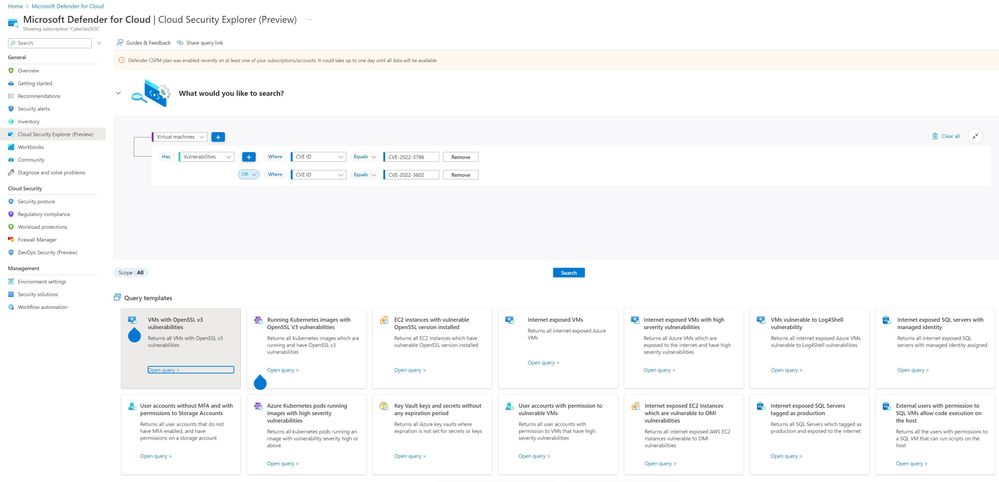
Hunt for all impacted workloads using the cloud security explorer
Note: To hunt for impact workloads, first enable in Microsoft Defender for Cloud the new Defender CSPM service and Defender for Containers if you have containerized workloads. Fo more details on enabling these services, click here for Defender CSPM and here for Defender for Containers.
Understanding the exploitability and business impact of resources is critical for identifying the most urgent tasks and at-risk assets that need to be patched first. Defender for Cloud’s new Defender CSPM plan provides context for your workloads based on multiple data layers including internet exposure, permissions, and connections between identified entities. The new intelligent cloud security graph also identifies potential entry points and workloads with the highest potential exploitability.
To use the templates and query the cloud security graph:
- Sign in to the Azure portal.
- Navigate to Microsoft Defender for Cloud > Cloud Security Explorer (preview).
- Select one of the templates relevant, for example “VMs with OpenSSL v3 vulnerabilities”
Figure 3: Cloud security explorer query for VMs containing vulnerable OpenSSL 3.x packages
Learn more about cloud security explorer and other Defender CSPM capabilities.
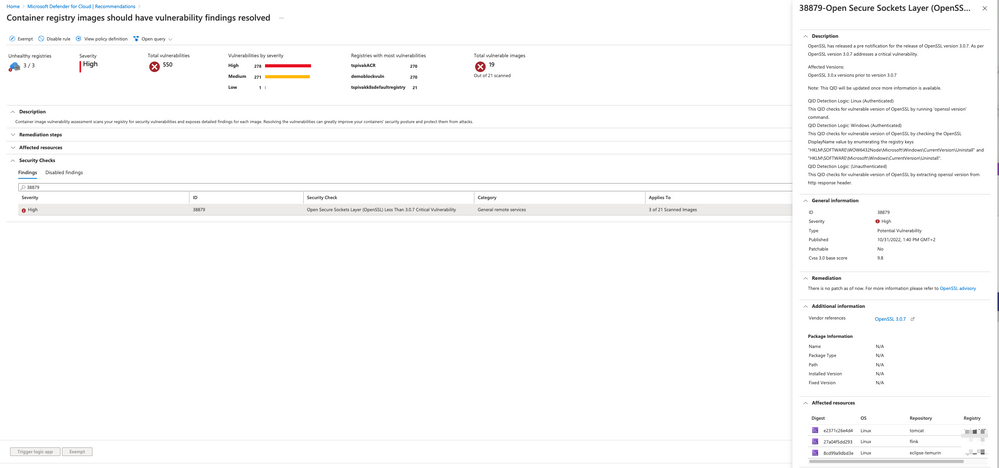
Use vulnerability assessments for VMs, containers and container images
Vulnerability assessment reports can be reviewed in both the Defender for Cloud recommendations platform or using Azure Resource Graph.
To view vulnerability management reports using Defender for Cloud’s recommendations platform:
- Sign in to the Azure portal.
- Navigate to Microsoft Defender for Cloud > Recommendations
- Select the relevant recommendation and search for the specific QID or CVE.
Figure 4: Container images affected by the OpenSSL v3 vulnerability (recommendation)
Relevant recommendations:
- Azure VMs: Machines should have vulnerability findings resolved
- AWS VMs: EC2 instances should have vulnerability findings resolved
- Container images in ACR: Container images should have vulnerability findings resolved
- Container images in ECR: Elastic container images should have vulnerability findings resolved
- Running container images in AKS: Running container images should have vulnerability findings resolved
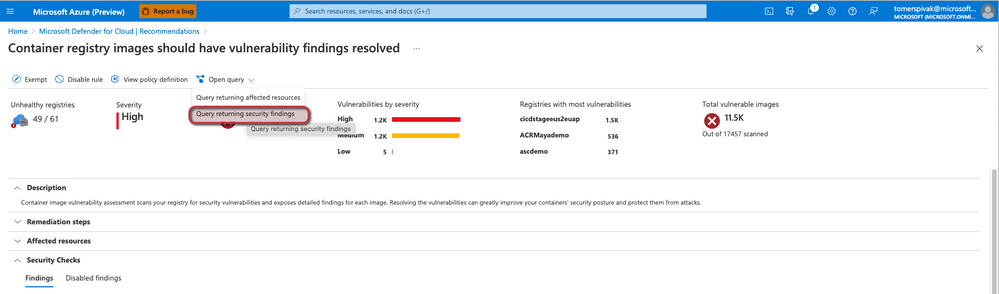
To view vulnerability management reports using Azure Resource Graph:
- Follow the above steps. Within the recommendation screen select Open Query > Query returning security findings and adjust to query to search for the relevant CVEs/QIDs:
Figure 5: Open Azure Resource Graph query from a recommendation
Sample query for retrieving images impacted by the vulnerability:
securityresources
| where type =~ "microsoft.security/assessments/subassessments"
| extend assessmentKey=extract(@"(?i)providers/Microsoft.Security/assessments/([^/]*)", 1, id)
| where assessmentKey == "dbd0cb49-b563-45e7-9724-889e799fa648"
| extend Props = parse_json(properties)
| extend Status = tostring(Props.status.code)
| where Status =~ "Unhealthy"
| extend additionalData = Props.additionalData
| extend qid = tostring(Props.id)
| where qid == "38879"
| extend registryHost = tostring(additionalData.registryHost)
| extend repository = tostring(additionalData.repositoryName)
| extend digest = tostring(additionalData.imageDigest)
| extend azureResourceId=tostring(split(id,"/providers/Microsoft.Security",0)[0])
| distinct subscriptionId,registryHost, repository, digest, azureResourceId
Next Steps
Read more about Microsoft’s guidance related to OpenSSL 3.0-3.0.6.
Read more about how to identify and patch vulnerable assets with Microsoft Defender Vulnerability Management.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.