- Home
- Security, Compliance, and Identity
- Microsoft Defender for Cloud Blog
- Microsoft Defender PoC Series – Defender CSPM
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Introduction
This Microsoft Defender for Cloud PoC Series provides guidelines on how to perform a proof of concept for specific Microsoft Defender plans. For a more holistic approach where you need to validate Microsoft Defender for Cloud and Microsoft Defender plans, please read How to Effectively Perform an Microsoft Defender for Cloud PoC article.
Cloud Security Posture Management provides organizations with a centralized view of their cloud security posture, allowing them to quickly identify and respond to security risks, ensures compliance, and allows for continuous monitoring and improvement of cloud security posture.
Defender for Cloud CSPM provides organizations with a unified view of their cloud environment across multiple cloud providers, including Azure, AWS, GCP and On-premises.
Defender for Cloud offers CSPM in two plans: a free Foundational CSPM plan and a Premium Defender CSPM plan. To understand the capabilities of CSPM plans, please refer: Overview of Cloud Security Posture Management (CSPM) | Microsoft Learn.
Defender CSPM plan, provides advanced posture management capabilities such as Attack path analysis, Cloud security explorer, Agentless Scanning, security governance capabilities, and also tools to assess your security compliance.
Planning
As part of your Defender CSPM PoC you need to identify the use case scenarios that you want to validate. You can use these 3 blogs from our Tech Community as a starting point to validate proactive security posture management scenarios:
- A Proactive Approach to Cloud Security Posture Management with Microsoft Defender for Cloud
- Proacting Hunting with Cloud Security Explorer in Defender for Cloud - Microsoft Community Hub
- Prioritize Risk remediation with Microsoft Defender for Cloud Attack Path Analysis - Microsoft Commu...
The next scenarios that you can validate are:
- Quick onboard of a virtual machine to see how Agentless Scanning for Machines is effective.
- Validate Agentless container posture capabilities from Defender CSPM
- Create governance rules to assign tasks to workload owners to remediate recommendations.
Preparation
The Defender CSPM plan needs to be enabled on the Azure subscription.
You need at least Security Admin role to enable Microsoft Defender CSPM plan.
Agentless scanning for Machines requires the Subscription Owner to enable the plan.
Agentless discovery of Kubernetes requires you to have one of the following role assignment or equivalent permissions on the subscription:
- Subscription Owner
- User Access Admin and Security Admin.
Enabling Defender CSPM plan
To gain access to the capabilities provided by Defender CSPM, you'll need to enable the Defender Cloud Security Posture Management (CSPM) plan on your subscription
- Open Azure Portal and navigate to Microsoft Defender for Cloud blade.
- From Defender for Cloud's menu, open the Environment Settings page and select the relevant subscription.
- In the Defender plans page, select Defender CSPM turn the status to ON
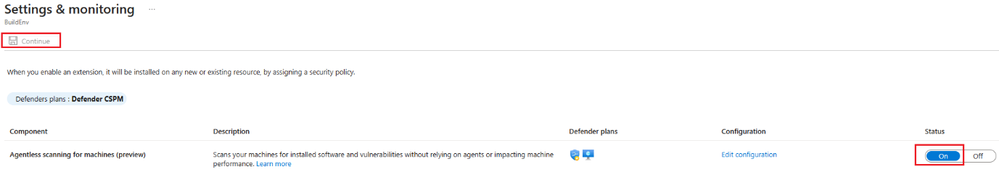
4. Select Settings. Turn ON the Agentless scanning for machines and click continue
5. Click on Save to save the changes
Implementation and Validation
Now that you already validated proactive security posture management approach, let’s validate the other capabilities.
Agentless Scanning for Machines
To validate the usage of agentless capability, you will provision a new Windows Server VM and wait 24 hours to start getting the results. This is a requirement for Agentless scanning to provide vulnerability assessment and software inventory in 24 hours. Leave the setup and comeback after 24 hours. After waiting this time, follow the steps below to see software inventory for this VM:
- Open Azure Portal and navigate to Microsoft Defender for Cloud blade.
- From Defender for Cloud's menu, open the Inventory page and select the Virtual Machine you created, and click on the Virtual Machine. It will take you to the Resource Health Page
- On the right pane click on Installed Applications. Agentless scanning provides visibility into installed software and software vulnerabilities on your Virtual Machine. Learn more about agentless scanning.
- On the right pane click on Recommendations. Click on the recommendation “Machines should have vulnerability findings resolved”. Defender for Cloud shows the vulnerability findings for that VM, ordered by severity. Learn more about View findings from vulnerability assessment solutions in Microsoft Defender for Cloud | Microsoft Le...
Agentless Container Posture
To validate agentless container posture capabilities from Defender CSPM, prepare your environment by following the guidance here.
Learn more about Agentless Container Posture and Agentless discovery of Kubernetes.
To validate the usage of agentless discovery of Kubernetes. Consider the following:
- Open the Azure Portal, open the Subscriptions blade, and select the subscription where you turned on “Agentless discovery of Kubernetes”.
- Select “Access control (IAM)” and click on “Role assignments.”
3. Check that the following role has been created on the subscription:
4. Agentless information in Defender CSPM is updated through a snapshot mechanism. It can take up to 24 hours to see results in Cloud Security Explorer and Attack Path. Leave the setup and comeback after 24 hours.
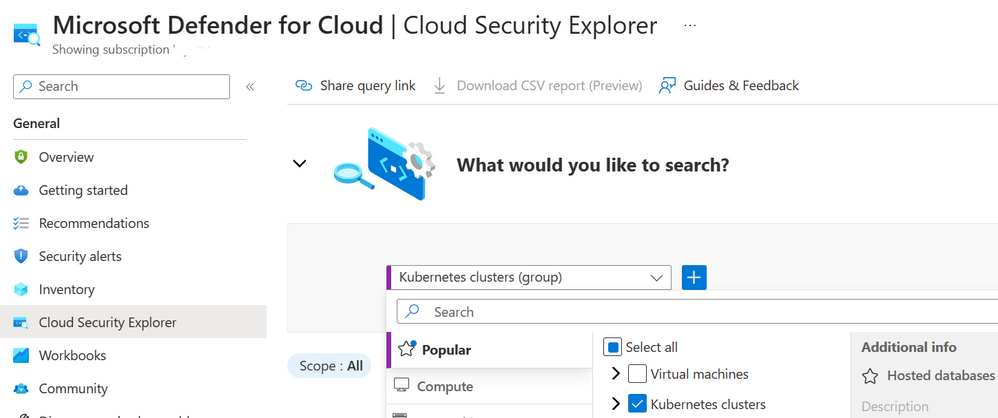
5. Navigate to the Microsoft Defender for Cloud blade select “Cloud Security Explorer” then select “Kubernetes clusters” in the drop-down menu and click search to see clusters that have been onboarded.
Agentless container vulnerability assessment (VA) scanning
Before performing the PoC on container VA scanning, be sure to check the supported environments and image types here.
To validate the image scanning, perform the following steps:
- Open the Azure Portal and navigate to the Microsoft Defender for Cloud blade.
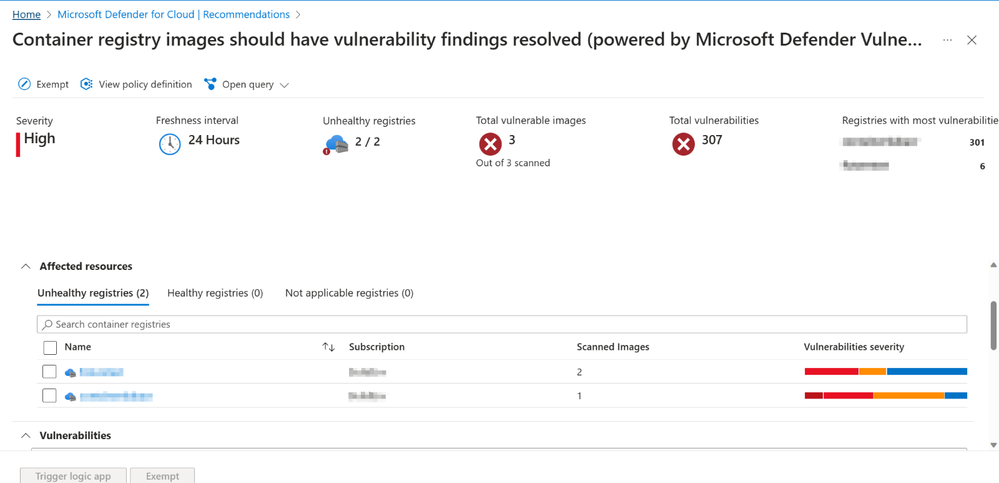
- Navigate to the recommendations tab. Under the “Remediate vulnerabilities” security control, look for the recommendation “Container registry images should have vulnerability findings resolved (powered by Microsoft Defender Vulnerability Management)” or enter it in the search bar.
- If any of the above triggers are met, you should see results appear in the recommendation. Note that it refreshes every 24hrs. To learn more about how to remediate or view the vulnerabilities, visit here.
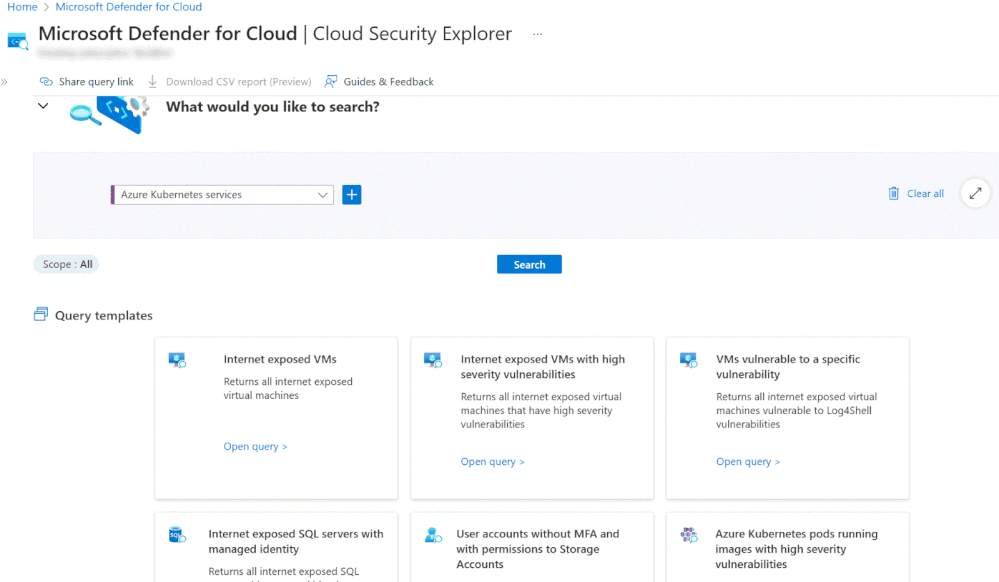
3. You can also view container VA results via the Cloud Security Explorer including filtering by severity, CVE ID, CVSS score and CVSS vector as shown below.
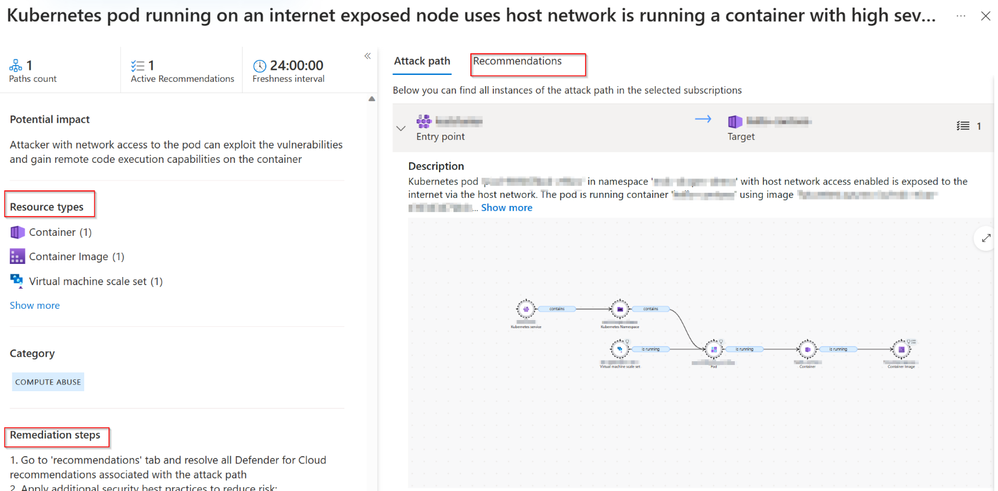
Using attack path analysis to visualize risks and threats to Kubernetes environments
All attack paths show relevant resources in your environment that are impacted by the exploitable path including specific parts of the Kubernetes estate such as the pod and namespace. The attack path also includes remediation steps and applicable recommendations to remediate the attack path.
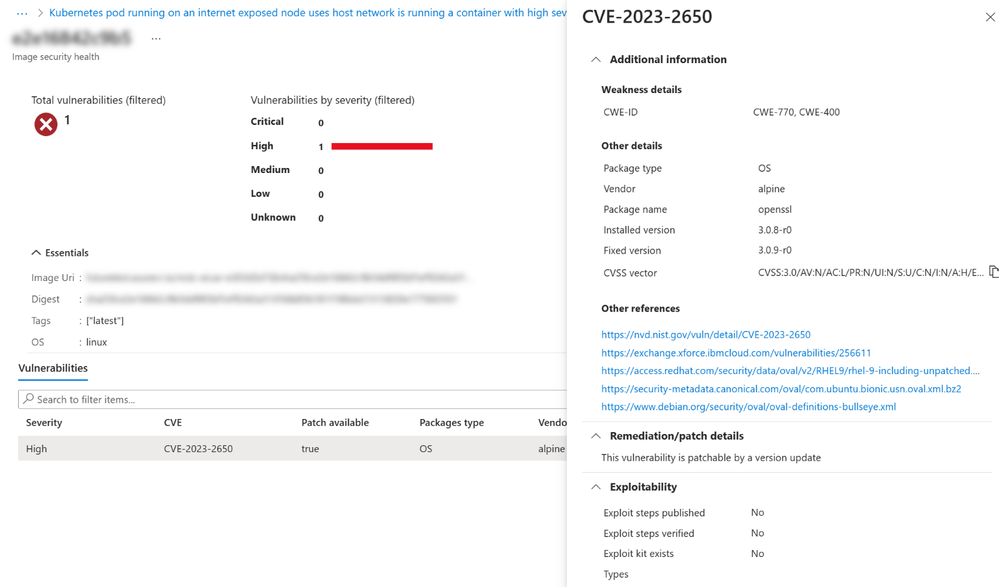
The attack path above references high severity vulnerabilities, to view the vulnerabilities identified, click on the container image.
In the “Insights” section, you can view a dropdown list of all vulnerabilities on the container image. After selecting the vulnerability, clicking on “Open the vulnerability page” will take you to a filtered overview of the vulnerability where you can view information such as remediation/patch details and exploitability.
Using cloud security explorer for risk hunting by querying various risk scenarios.
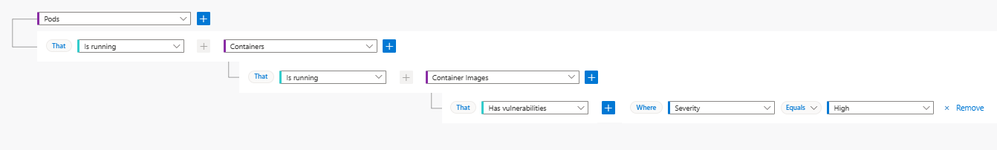
To validate the cloud security explorer for agentless container posture, you can utilize built in “Query templates” or create a custom search. For more information on possible insights and connections in the cloud security explorer. Search for “Kubernetes” in the list of insights.
Consider the following example as a custom search: List all Kubernetes clusters that have unhealthy recommendations and are running images vulnerable to remote code execution.
Governance
The last scenario to validate, is Governance. Follow the steps below to assign a Governance Rule to remediate high severity vulnerabilities on the VM
- Open Azure Portal and navigate to Microsoft Defender for Cloud blade.
- From Defender for Cloud's menu, open the Environment Settings page and select the relevant subscription.
- Under settings Select Governance Rules(Preview)
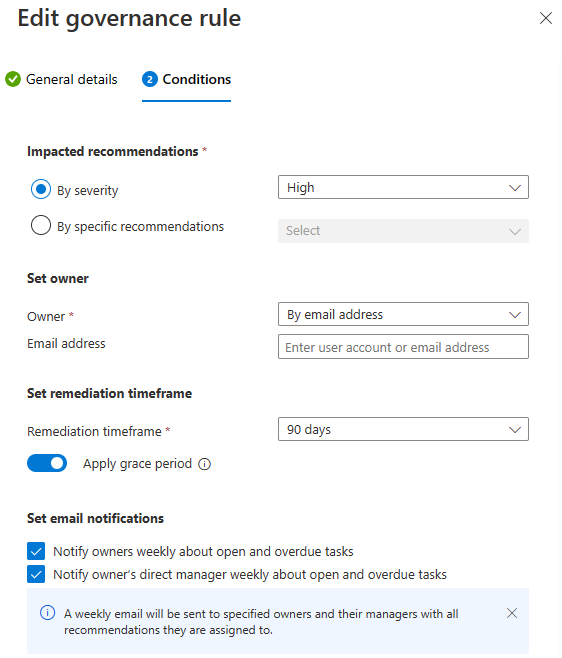
- Click on +Create governance rule
- Give a rule name, select scope at subscription level, priority 100
- Under conditions, select By severity -> High, Owner -> By email address, specify the email address of the workload owner to receive notification email, Remediation timeframe -> 90 days
- Notify Owners weekly about open and overdue tasks and click Save.
- Click on save. A weekly email will be sent to specified owners and their managers with all recommendations they are assigned to.
Conclusion
By the end of this PoC you should be able to determine the value proposition of Microsoft Defender CSPM and the importance to proactively mitigate risks in your environment.
Stay tuned for more Microsoft Defender PoC Series!
More Resources
To learn more about Defender CSPM capabilities, visit the following resources:
- Defender for Cloud in the Field – Governance capabilities
- Defender CSPM Lab
- Defender CSPM Webinar
-
Agentless Container Posture Management | Defender for Cloud in the Field
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.