- Home
- Security, Compliance, and Identity
- Microsoft Defender for Cloud Blog
- Improved experience for managing the default Azure security policies
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Introduction
To improve your overall security posture, you have to implement security recommendations for your environment.
The Microsoft Cloud Security Benchmark is a Microsoft-authored set of guidelines that are being adopted as the default for security and compliance best practices based on common compliance frameworks.
There are currently multiple options and advanced capabilities for managing security recommendations in Azure. It is often heard from customers that security recommendations need to be managed more effectively, as well as that basic operations need to be performed to fine tune them.
We are pleased to announce an improved user experience that simplifies the day-to-day tasks of security teams that need to operate multi-cloud environments.
Advantages and use-cases
The improved experience allows security teams to review, operate and fine tune security recommendations based on the organizational needs:
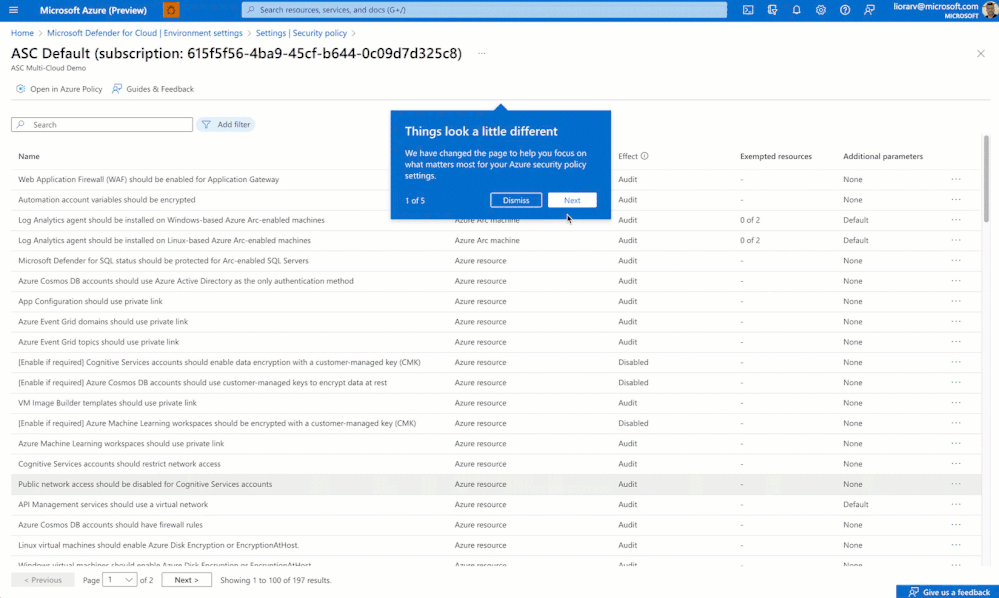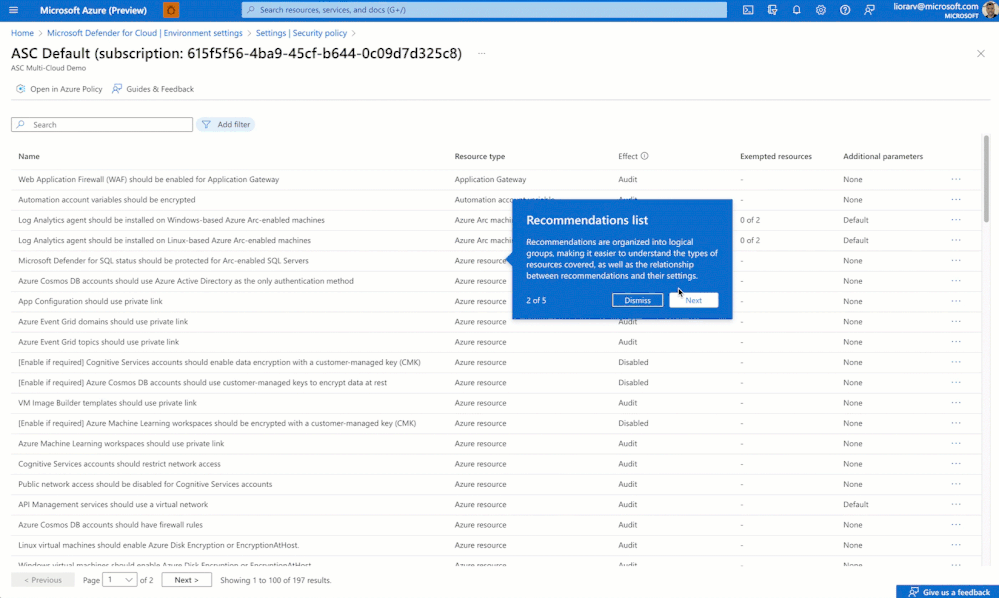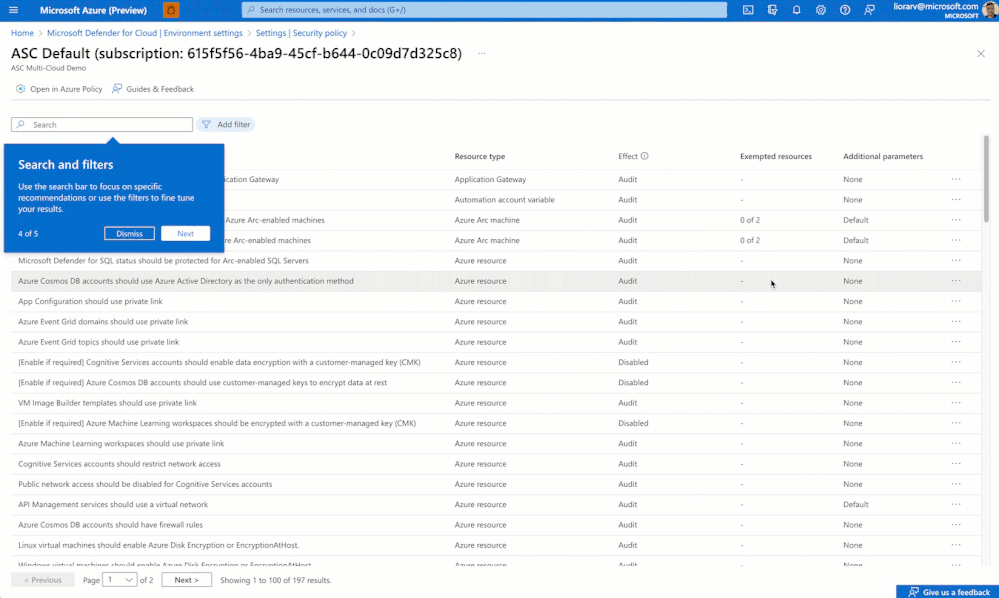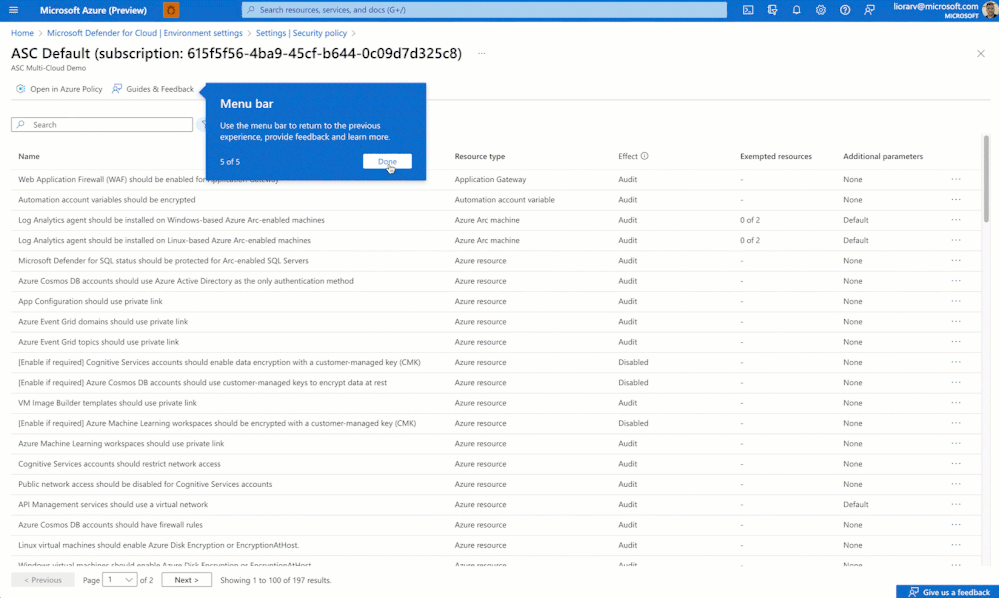
We have changed the page to help you focus on what matters most for your Azure security policy settings. The improved experience allows security admins to have a single view of all security recommendations offered by the Microsoft Cloud Security Benchmark (MCSB) for their Azure environment (formerly the Azure Security Benchmark).
Security recommendations are organized into logical groups, which makes it easier to understand the types of resources covered, as well as the relationship between parameters and recommendations. For example, security recommendations for Containers require additional customer configurations to ensure they are tuned for specific use cases. Using filters such as “additional parameters,” security admins can now view all recommendations that run with default values and change them. Once identified, use the “manage effect and parameters” to view corresponding settings.
To operate security recommendations in a much more effective way, we simplified the way to choose between multiple effects: “Audit” evaluates the compliance state of resources according to recommendation logic. “Deny” prevents deployment of non-compliant resources based on recommendation logic and “Disabled” prevents the recommendation from running. We often hear customers wanting to reset a specific recommendation to its default value. Using the “reset to default” you can revert changes and make sure both effect and additional parameters are being rested to the default.
Finally, use search and filters to look for recommendations and the manage exemptions per recommendation, Soon, you will also be able to export the data to CSV.
Try it today!
The improved experience is available today on Azure commercial and soon on national clouds.
Learn more
Furthermore, a new set of teaching bubbles has been added to help you learn how to use Defender for Cloud's security recommendations and links to official documentation located on the "Guides & Feedback" button.
Feedback
We value your opinion, and we want to hear from you. That is why we have added a feedback button, where you can share your thoughts and suggestions with us. Your feedback helps us improve our products and services and provide you with a better user experience.
Acknowledgements
Special thanks to the reviewers of this article, Lara Goldstein and Linnet Kariuki.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.