- Home
- Security, Compliance, and Identity
- Microsoft Defender for Cloud Apps
- Re: Editing 'Risky sign-in' policy in Microsoft Defender for Cloud Apps
Editing 'Risky sign-in' policy in Microsoft Defender for Cloud Apps
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 21 2021 05:19 AM
Hi Guys,
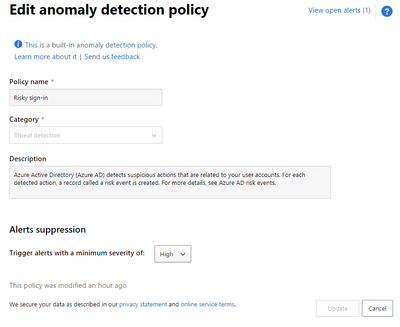
I wonder if I can edit the 'Risky sign-in' policy in Microsoft Defender for Cloud Apps, It looks like I can only edit the 'Trigger alerts with a minimum severity of'. I am trying to exclude certain IP, so I won't get alert when someone is logging in from it. I already added this IP to the whitelist option in 'Tag as a Corporate IP and add to whitelist', but I still get alerts when there is any activity from this IP.
Thank you for your help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 22 2021 06:45 AM - edited Nov 22 2021 06:47 AM
@ozh123 ,
Risky sign-in detections are ingested from Azure Identity Protection to MCAS (the reason can not add exclusions on this particular MCAS policy):
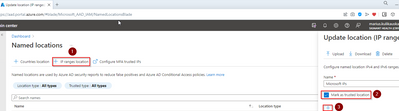
In this case create a new trusted IP range in Azure IdP blade: https://aad.portal.azure.com/#blade/Microsoft_AAD_IAM/NamedLocationsBlade
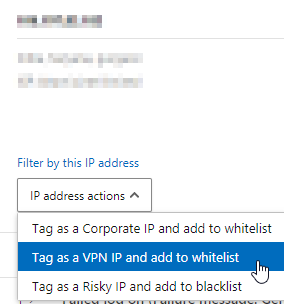
Also, one more option to remove this IP from showing up in false positive alerts - whitelist and tag as VPN from MCAS:
Type in IP and whatever tag name for your reference:
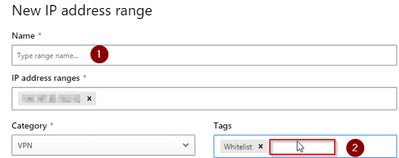
I do not like this too much due to descriptive inaccuracy since those IPs I want to whitelist are not my companies VPNs, but seem to help in many cases not to show up in alerts anymore.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 14 2024 11:33 AM
@ozh123 Addressing unwarranted 'Risky sign-in' alerts in Microsoft Defender for Cloud Apps necessitates engaging with Azure Identity Protection to establish a trusted IP range. This step is critical because it directly influences the source of risk assessments, thereby potentially reducing alerts for whitelisted IPs. If alerts continue despite this measure, consider the alternative of tagging the IP as a VPN in Defender for Cloud Apps, albeit with caution due to possible inaccuracies.
These actions represent a focused approach to refining alert mechanisms and ensuring that they align with your network's actual security posture.