- Home
- Security, Compliance, and Identity
- Microsoft Defender for Cloud Apps
- Defender for Cloud Apps REST API - Authentication
Defender for Cloud Apps REST API - Authentication
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 16 2023 07:46 AM
Hi Everyone,
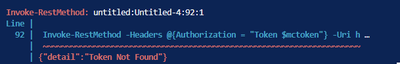
I am trying to automate deployment of policies on MDCAS with Powershell and for testing envrironment i have a test tenant which includes Defender for Cloud Apps. I have created a API Token and used it in my Script but i am getting following error
It works on production Tenant. I dont understand the reason.
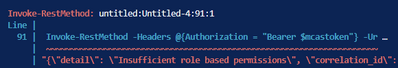
I have also tried Oauth2 Authentication by adding an WebApp in Azure Active Directory and have assigned all neccessary permissions but at this time i am getting the following error
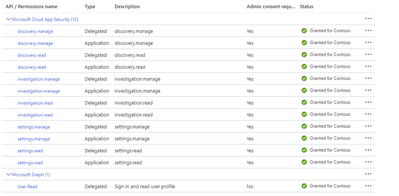
here is the permissons;
Can anyone tell me what i miss? Or is there another way to deploy policies ? Graph API or PS cmdlets?
Thank you in advance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 20 2023 11:09 AM
Hi @mhmmdrn,
There currently isn't a way to deploy policies in an automated manner today.
The endpoint we do support can be found here:
REST API - Microsoft Defender for Cloud Apps | Microsoft Learn
Feel free to add an item and provide your feedback here:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 21 2023 12:24 AM
@Keith_Fleming thank you for your answer, actually my question was about the authentication. Which Role based Permission should i give to authenticate the app which i created Azure AD? Should i give the app subscription level permissions, contributer etc.
By the way, there are some endpoints which are not listed in official documentation. For example;
- /api/v1/policies >> to get all deployed policies
- /api/v1/policy_templates >> to get all policy templates
- /api/v1/policy/discovery >> to deploy app discovery policies with Post method. and so on.
These endpoints work as expected. I tried them. But i need assistence in order to authenticate Test Tenant to deploy policies using Post Method. I can get the policies with Get method at Test Tenant but i doesnt allow me to deploy them.
Thank you in advance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 21 2023 05:36 AM
SolutionHi @mhmmdrn,
The reason you’re seeing the errors in this case is because these are not supported endpoints.
While there are several undocumented endpoints you can find through various methods they are reserved for the internal service and not exposed to an app registration permissions. This is implemented as part of the service so adding RBAC permissions or roles won’t correct the error here.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 21 2023 05:36 AM
SolutionHi @mhmmdrn,
The reason you’re seeing the errors in this case is because these are not supported endpoints.
While there are several undocumented endpoints you can find through various methods they are reserved for the internal service and not exposed to an app registration permissions. This is implemented as part of the service so adding RBAC permissions or roles won’t correct the error here.