- Home
- Security, Compliance, and Identity
- Microsoft Defender for Cloud Blog
- Creating custom recommendations & standards for your workloads with Microsoft Defender for Cloud
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Introduction:
Have you ever found yourself in a situation where you wanted to determine which AWS resources are missing a tag? You can accomplish this use case using custom recommendations for AWS workloads in Defender for Cloud. The following steps solve the problem of creating a custom recommendation that identifies which Amazon RDS instances are missing a tag, but they can be applied to other use cases too.
To learn more about this feature, you can watch the following video.
Note: To use the option of creating custom recommendations and standards with KQL, you need to have the Defender Cloud Security Posture Management (CSPM) plan enabled. To learn more about Defender CSPM capabilities, you can start at https://learn.microsoft.com/en-us/azure/defender-for-cloud/concept-cloud-security-posture-management.... If Defender CSPM is not enabled, it's still possible to create standards with built-in recommendations and create custom recommendations based on Azure policy.
To create a custom recommendation for with Defender for Cloud, you need to configure the following parts:
- Create custom standard
- Create custom recommendation
- Assign the standard containing custom recommendations
Whenever you create a custom recommendation for Azure/AWS/GCP workloads in Defender for Cloud, you need to go through a wizard and sequentially configure all three parts, starting with creating a custom standard.
Create custom standard
You can think of standard as a logical grouping for custom recommendations for your Azure/AWS/GCP resources. For the purposes of this article you can either use an existing standard or create a new one. To create a new standard, sequentially perform the following steps:
- Log in to the Azure Portal.
- Navigate to the Defender for Cloud dashboard.
- Select Environment settings and then click the desired security connector.
- Select Standards > + Create > Standard.
- Insert name and description for standard (like in figure 1).
- Choose the custom recommendations you want to add to this standard. For the purposes of this article leave this blank for now.
- Click Create.

This creates the standard and you can see it under Standards (figure 2).

Create custom recommendation
To create a custom recommendation that identifies which Amazon Relational Database Service (RDS) instances are missing a tag, sequentially perform the following steps:
- Log in to the Azure Portal.
- Navigate to the Defender for Cloud dashboard.
- Select Environment settings and then click the desired security connector.
- Select Standards > + Create > Recommendation.
- Insert name and description for remediation. Then insert the remediation description and select the severity. Select the standards you created in the previous step.
- Click Next.
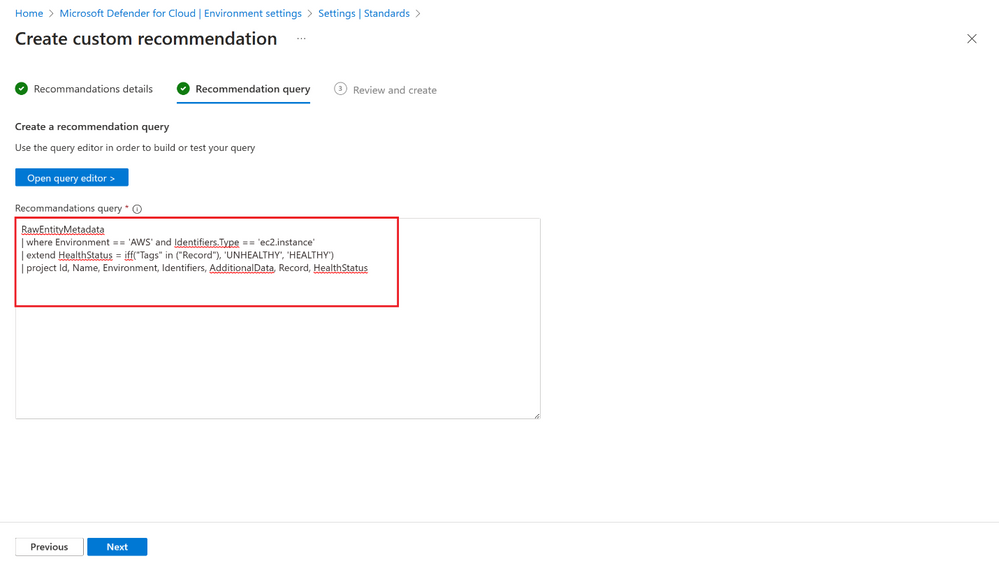
- Select the Open query editor.
- In the editor that appears, insert the following KQL query:
RawEntityMetadata
| where Environment == 'AWS' and Identifiers.Type == 'rds.cluster'
| extend HealthStatus = iff("Tags" in ("Record"), 'UNHEALTHY', 'HEALTHY')
| project Id, Name, Environment, Identifiers, AdditionalData, Record, HealthStatus
- Run query. The results that are returned are based on your own AWS environment. After you’re confident that the results are indeed what you’re after, copy the KQL query to the previous tab (like in figure 3), and click Next.
- Click Create.
After you click on create, a notification appears confirming that you successfully created a new recommendation.
Exercise:
As a firm believer in learning by doing, for extra credit create another custom recommendation that detects EC2 instances, that have a named KMS key attached. This exercise further strengthens your knowledge around custom recommendations. If you need help with the query for this recommendation, you can use the following query:
RawEntityMetadata
| where Environment == 'AWS' and Identifiers.Type == 'ec2.volumes'
| extend KMSKeyID = tostring(Record.KmsKeyId)
| extend HealthStatus = iff(isempty(KMSKeyID), 'UNHEALTHY', 'HEALTHY')
After you create the custom recommendation(s), you can proceed with assigning the custom standard you created. Please note that after you create a custom standard, by default it’s not assigned and you need to assign it.
Assign the standard containing custom recommendations
To create a new standard, sequentially perform the following steps:
- Click the three dots on the right.
- Select Assing standard.
- Click Yes.
After performing these steps, the value in the Assigned to column changes to Account in case you onboarded an AWS single account (figure 4).

Conclusion:
In summary, the query editor allows you to run the KQL query over the data in your Azure/AWS/GCP environment and provides you with results, you can use to validate the query as you’re writing it. After you’re confident the query you created is returning the results that you’re after, you can use the query to create a custom recommendation for your Azure/AWS/GCP resources. You can then group several custom recommendation with a custom standard and assign it to your AWS accounts. Same applies for GCP projects and organization. While in this article, the examples covered focus on AWS, you can use this capabilities for GCP and Azure resources too!
Reviewers:
Yael Genut, Product Manager
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.