- Home
- Security, Compliance, and Identity
- Microsoft Defender for Cloud Apps
- Re: Cloud app Security client certificate
Cloud app Security client certificate
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 10 2021 08:39 AM
Hello all, i am following the below article on how to configure cloud app security to work with client certificates. I am currently using the demo cert that is called out in the article . The client cert has been added to the user cert store on the local machine, and the root cert was imported into cloud app security.
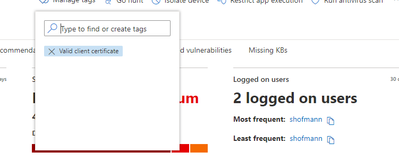
I have also tagged the device with "Valid client certificate" in endpoint manager,
(per below)
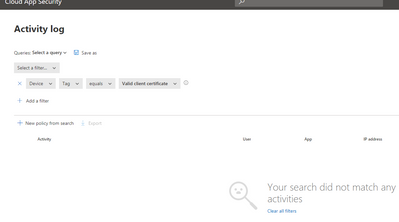
However when i do a search for all devices with tag - "Valid client certificate" i get back zero results. Need help understanding why cloud app security is not able to discover the device that i previously tagged ?
- Labels:
-
Cloud App Security
-
Cloud Discovery
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 03 2021 10:42 AM
https://docs.microsoft.com/en-us/defender-cloud-apps/proxy-deployment-aad
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 26 2023 02:03 PM