- Home
- Security, Compliance, and Identity
- Microsoft Defender for Cloud Apps
- Re: Block upload of documents to other office 365 tenant
Block upload of documents to other office 365 tenant
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 14 2021 10:17 PM
I wish to block upload of documents to Other Office 365 tenant on a managed device?
Can this be achieved using MCAS
- Labels:
-
Cloud App Security
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 29 2021 07:05 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 29 2021 10:08 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 30 2021 01:59 AM
Do you mean sharing documents with other tenants? because upload means they already have access to those tenants as guests maybe and the other tenants should take the action from their sides not yours.
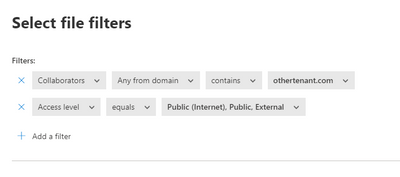
If you're talking about sharing files with another domains/tenant, as i know you can get prevent that using a File Policy in MCAS
Also you can use entire organization instead of Any Any from domain.
Cheers,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 30 2021 02:24 AM
My feeling is, the easiest solution would in fact be to encrypt data and have less focus on where the data is going.
You could also use a simple conditional access policy to block auth from unmanaged devices or only allow with from trusted locations. This means even a user in the source tenant can’t take the data away from a managed device and access it - their auth would be blocked by the conditional access policy.
Ultimately, there are a number of ways of preventing data being accessed outside the source tenant. I don’t believe blocking upload to “any M365 tenant” is a realistic option.
Encryption covers many vectors. Upload to any M365 tenant doesn’t even cover all vectors and would be hard / impossible to manage.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 30 2021 02:43 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 30 2021 03:34 AM
for what a list of millions of domains needed to? Instead of contain we can use do not contain.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 30 2021 04:13 AM
@MZyarah I think we are both wrong. That file policy doesn't even apply to uploads, it's a sharing policy.
And I may be wrong, but I believe a collaborator is defined as a user that has been given explicit access to the data. If the user is not a collaborator, the filter would not apply.
For the policy to work, every file shared would have to be explicitly shared to specific users. If a file is shared without specifying the users it's intended to be shared with, the policy would not apply.
Crucially, that policy does not appear to have any baring on upload of data, because uploading a file is not defined as sharing a file. The file policy in question is specifically a sharing policy - that means it has to be shared - upload does not trigger a sharing policy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 30 2021 04:14 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 30 2021 04:28 AM
I am not talking about sharing or collaborating here, I am talking about upload.
on my corporate device, i can log in to any office 365 tenant and upload documents of my tenant, i want to restrict to only single tenant
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 30 2021 04:40 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 30 2021 05:07 AM
This is not even related to uploading or sharing files, if you don't want your corporate devices access to other tenants you need to use Azure AD tenant restrictions, take a look here.
I hope this will be helpful.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 30 2021 06:01 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 30 2021 06:03 AM - edited Aug 01 2021 04:26 PM
What if all data is encrypted? What happens to sharing or uploading or any other means of exfiltration?
Sharing, uploading, it doesn't matter if the data is encrypted and only corporate devices can be used to authenticate so they can access the data.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 30 2021 07:41 AM
About the Encryption, for me I like to Encrypt the data everywhere however the main question was the MCAS is able to fix this issue!
In the question which not clear enough, I don't think the encryption will solve the requirements.
Let's consider this scenario, you have access for two tenants, one of them provided you with a managed device " mentioned in the main question also".
Now you have Managed Device and access to data in Tenant1 and Only access to data in tenant2 (you can consider the data is encrypted at rest and in transit if you like)
for example, what will prevent the user from opening a web session and browse to the tenant2 OneDrive and copy data from the local/tenant1 data to the second one?
If the encryption help, can you refer me to a doc/blog explaining same thing please.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 01 2021 04:25 PM
Again this now fixes this one very specific issue.
I think we need clearer definition of what the intended outcomes are. I agree, there are many scenarios, without knowing more, I don't believe we can provide an answer.