- Home
- Security, Compliance, and Identity
- Microsoft Defender for Cloud Blog
- Microsoft Defender for Cloud Data Flow
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Updated diagram: 09/13/2022
Overview
Microsoft Defender for Cloud is Microsoft’s cloud workload protection platform and cloud security posture management service that provides organizations with security visibility and control of hybrid workloads. The Log Analytics Agent must be installed in Windows and Linux operating systems that you plan on collecting data from.
We will examine how data flows when using Microsoft Defender for Cloud, specially the agent collection, central collection of log data, and creation of recommendations and alerts.
Microsoft Defender for Cloud Monitored Resources
Microsoft Defender for Cloud has two modes: Enhanced Security Off and Enable All Microsoft Defender For Cloud Plans. The first one provides security recommendations for compute, network, storage, identity, IoT and application resources in Azure. The second one provides threat detection for those workloads, and in addition to that, it enables you to monitor virtual machines hosted in other cloud providers and on-premises.
Only the data collected from virtual machines will be stored in a Log Analytics workspace. For your PaaS services such as Microsoft Defender for SQL, there is a “Continuous Export” feature that enables security alerts to be stored in a Log Analytics workspace. You can choose whether you want to use an existing workspace or leave Microsoft Defender for Cloud automatically create a default one. Keep in mind that you can gather data from virtual machines running in different subscriptions and store it into a single workspace. Azure Monitor Log Analytics workspace can be retained at no charge for up to first 31 days.
Microsoft Defender for Cloud Agent Data Flow: Log Analytics Agent
The Log Analytics Agent reads various security-related configurations and event logs from virtual machines via TCP 443. The data collected is going to be reflected in the Microsoft Defender for Cloud dashboard. This data will be transformed into recommendations such as missing updates, misconfigures OS security settings, endpoint protection enablement, health and into alerts of threat detections. Microsoft Defender for Cloud updates its recommendations within 24 hours; OS security configuration recommendations within 48 hours; and Endpoint Protection recommendations within 8 hours.
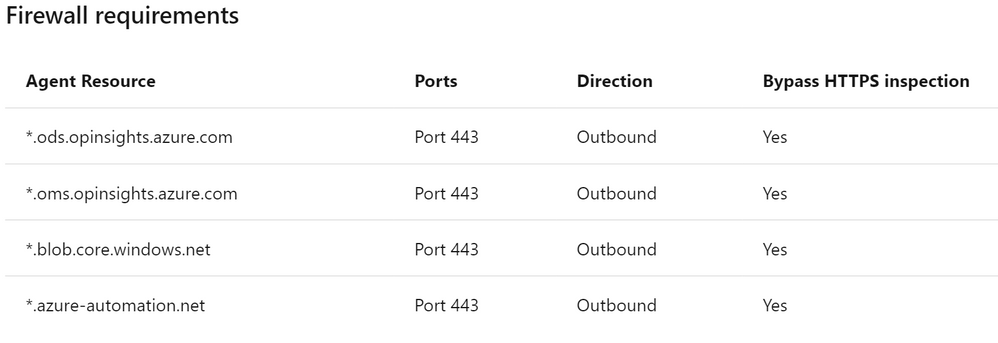
To have the Log Analytics Agent sending collected data into the Log Analytics workspace, your virtual machines will need Internet access. If you have a firewall implementation in your environment, make sure to set inbound and outbound allowance to the 5 agent resources mentioned in the firewall requirements table below, and that has a broader vision of not only the monitored VMs but also other services that are supported by Microsoft Defender for Cloud:
If you need to harden the Log Analytics Agent URLs in your firewall, you can use the list below:
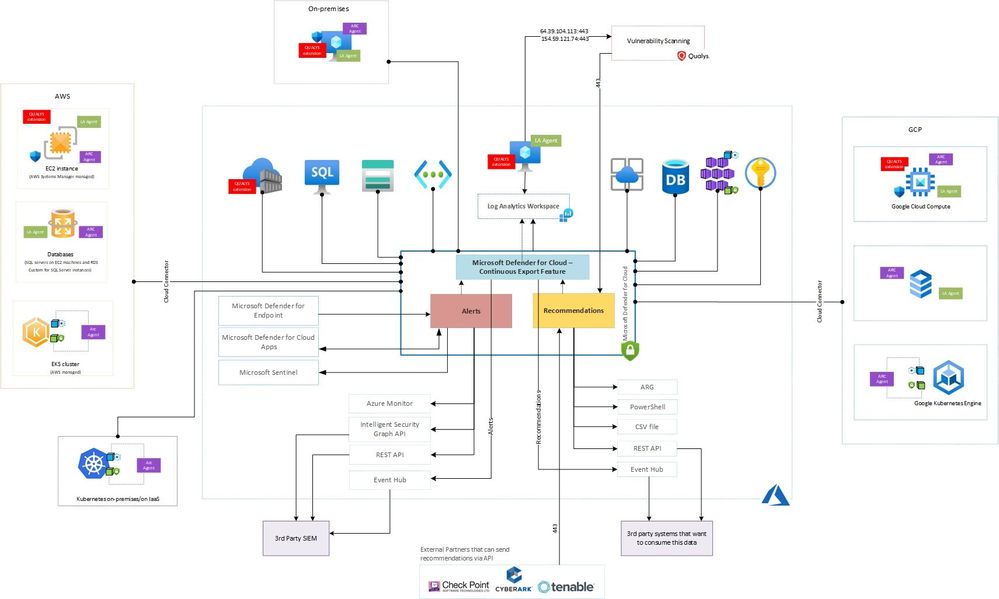
Microsoft Defender for Cloud Log Data Flow
- The Log Analytics Agent scans and collects security configurations and events from Linux and Windows operating systems.
- This information is sent to your Log Analytics workspace.
- Microsoft Defender for Cloud uses the collected data from the Log Analytics workspace and from other resources in Azure you choose to monitor to do an advanced threat detection analysis:
- Integrated threat intelligence
- Behavioral analytics
- Anomaly detection
- Microsoft Defender for Cloud generates recommendations (only the ones enabled in Security Policies) and issues alerts based on the analysis.
- The Microsoft Defender for Cloud dashboard will display recommendations and alerts.
Recommendations
Microsoft Defender for Cloud periodically analyzes the state of monitored resources to identify potential security vulnerabilities. This information is transformed into recommendations that have a Secure Score impact. This assessment focuses on improving your security hygiene. When a recommendation is remediated, Microsoft Defender for Cloud will update your Secure Score.
Recommendations will have a short description, resources involved and remediation steps to follow. Some include a Quick Fix feature to act easily and promptly. All recommendations from Microsoft Defender for Cloud will be displayed in its dashboard, but can also be reached through PowerShell, ASC REST API, Event Hub, third party change management or security operations systems, and even downloaded as a CSV file.
At Ignite 2019, Microsoft Defender for Cloud Team announced partnership with Check Point, Tenable and CyberArk that enable these partners to send recommendations to Microsoft Defender for Cloud using API. Assuming you have the right license for those products, you could leverage these capabilities to have visibility of security recommendations in Microsoft Defender for Cloud dashboard. Recommendations can also be triggered by the built-in vulnerability assessment integration with Qualys.
Alerts
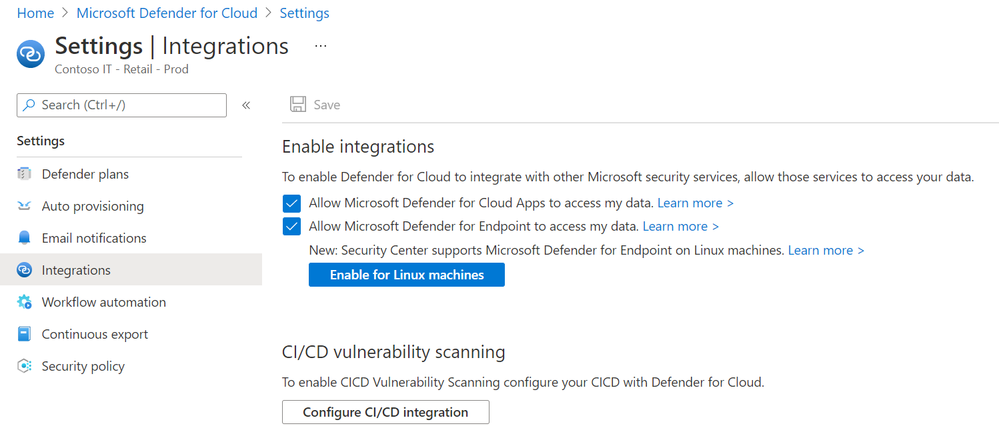
Microsoft Defender for Cloud deploys a variety of alerts, triggered by advanced threat detections, for the monitored resources you set (Azure, on-premises, hybrid cloud environments). They will get assigned a severity to help you prioritize tasks to solve them. Alerts can be seen in Microsoft Defender for Cloud dashboard and Azure Monitor Activity Log, but also they can be configured to push information to ASC REST API, Intelligent Security Graph API, Event Hub, and a third party SIEM solution. When the options shown in the figure below are enabled in ASC settings, ASC will also share analytics with MDATP and MCAS:
For more information on the list of alerts that can be generated by Microsoft Defender for Cloud, read the Alerts Reference Guide.
Continue learning more
Deep dive into Microsoft Defender for Cloud
Microsoft Defender for Cloud REST
Microsoft Defender for Cloud digestion of Azure Policy REST API
Security Alerts in Azure Monitor Activity Log
Export security alerts and recommendations
Connect to the Intelligent Security Graph API
PowerShell – Microsoft Defender for Cloud module
This blog was written as a collaboration between @Kara Cole @Cristhofer Munoz @Tiander Turpijn @Yuri Diogenes @Nicholas DiCola (SECURITY JEDI) and @Fernanda_Vela
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.