- Home
- Security, Compliance, and Identity
- Microsoft Defender for Endpoint Blog
- Microsoft Defender ATP unified indicators of compromise (IoCs) experience
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Indicator of compromise (IoCs) matching is an essential feature in every endpoint protection solution. This capability is available in Microsoft Defender ATP and gives SecOps the ability to set a list of indicators for detection and for blocking (prevention and response).
Today we’re announcing the unified indicators experience. In this update we unified several different IoC lists and made the lists more accessible for interactive (portal) and automated (API) use. In addition, we aligned all detection and enforcement means to honor the unified list. The new schema supports several actions such as allow, alert-only, and alert and block. It also supports RBAC for fine-grained control over user access.
Get started
Get up and running by trying out the UX experience. When you’re better acquainted with the capability, learn more about the different usage options described below.
Simple indicator submission
- Select Settings. Under Rules section select Indicators.
- Select the File Hashes tab, then select + Add indicator.
3. Follow the side pane steps:
- Type the desired file hash to block and set the expiry to “never”. Click Next.
- Select a description to display when an alert is raised for this IoC.
- Click Next, Next, and Save.
Congrats! You’ve just created your first IoC.
Explore the other features you see around. Try the batch import or indicator list export.
Available enforcement means
Currently, the main supported means are the cloud detection engine, the AutoIR engine, and the endpoint prevention agent (a.k.a Windows Defender AV).
Detection
The cloud detection engine of Microsoft Defender ATP scans the telemetry collected regularly and tries to match the indicators you set. When there is a match, action will be taken according to the settings you specified for the IoC.
Prevention
The same list of indicators is honored by the prevention agent. Meaning, if Windows Defender AV is the primary AV configured, the matched indicators will be treated according to the settings. For example, if the action is “Alert and Block”, the antivirus will prevent the file executions (block & remediate) and a corresponding alert will be raised. On the other hand, if the Action is “Allow”, the AV will not detect nor block the file from being run.
Note #1: There is a propagation time of several minutes before the blocking policy for a new hash is applied.
Note #2: Trusted signed files will be treated differently. MDATP is optimized for handling malicious files. Trying to block trusted signed files, in some cases, may have performance implications.
Automation (a.k.a. AutoIR)
The automated investigation and remediation behave the same. If an indicator is set to Allow, AutoIR will ignore a “bad” verdict for it. If set to “Block”, AutoIR will treat it as “bad”.
Supported IoCs
In the first phase, the file hashes are fully supported, while network addresses (IP, Domain names) are partially supported (Automation and Detection). Stay tuned as the network blocking and more IoCs become available.
Supported actions
The current actions supported are Allow, Alert-only, Alert&Block. More actions are planned. Please see what actions are supported for each IOC type. The goal is to have parity whenever applicable.
Modify the indicator list
There are five (5!!!) ways to control the IoC lists.
1) Manual Editing
As mentioned earlier, you can edit the list by just adding and removing indicators from the new list experience.
2) Contextual IoC creation
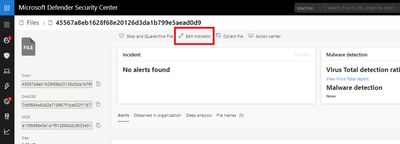
The new unified experience preserves the simplicity of IoC creation and modification from the entity pages. For example, from a file page, you can just block the file as you did before but now with the new unified experience, you can easily pivot to the indicator view to update the response action for the file.
3) Batch IoC import
This is a simple way to import a list maintained in a CSV file. All you need is to:
- Get a list of IOCs.
- Click the import button.
- Download Sample CSV (1).
- Paste the indicators there.
- Set the actions, expiry, and other fields.
- Save the file.
- Click “Choose File” (2).
- Click “Import” (3).
4) Use the Microsoft Defender ATP Indicators API
The new Indicators API is available for custom integrations. Our previous blogs will get you up to speed in minutes.
General Indicators API blog
Push custom Indicators of Compromise (IoCs) to Microsoft Defender ATP
MISP integration
Microsoft Defender ATP and Malware Information Sharing Platform integration
5) Use partner integrated solutions
While it is based on the same API as an extensibility method, some partners already integrate solutions.
For example, Palo Alto Networks AutoFocus/MinMeld created a native integration with Microsoft Defender ATP. See, How to Configure MineMeld to Send Indicators to Microsoft Defender ATP
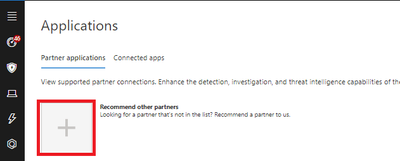
To track supported applications, visit our Applications page.
If you can’t find your preferred solution, use the “Recommend Other Partners” button on the upper left corner.
RBAC support
RBAC is supported for the UX experience. Analysts can set target groups for the IoC. This will be a subset or all the machine groups that the analyst is authorized to access. IoCs set by a global admin will take precedence. Meaning, there’s no way to override them for a subgroup.
The API has no group granularity and it is supported for the entire Org. The access is enabled only in an application context. Refer to the blogs mentioned earlier to learn more about application context.
IoC list size limit
Currently the list size is limited. We optimized the service to deal as quickly as possible with the most important IoCs. The assumption is that when an IoC is fresh or uncommon, there is a need for custom IoC lists. As regular IoCs age, it should be covered by regular AV solutions.
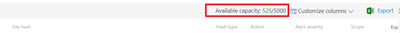
The current limit set to 5000. We will monitor and optimize it.
This work was done based on customer feedback. We would love to get your feedback too.
Microsoft Defender ATP Team
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.