- Home
- Security, Compliance, and Identity
- Microsoft Defender for Endpoint Blog
- Automate the boring for your SOC with automatic investigation and remediation!
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Many customers have successfully moved to full automatic investigation and remediation (auto-IR) in order to "automate the boring" for Tier 1 analysts. If you haven’t started doing this, we suggest reading our blog on operationalizing your organizations Security Operations Center (SOC) with automatic investigation and remediation.
Instead of SOC teams spending time viewing and responding to every alert, automatic remediation for certain kinds of threats can free up teams to focus on high priority security alerts that require investigation and analysis. It’s like having a virtual analyst in your SOC. In the current times with widespread remote work, the virtual analyst is ever more important and relevant for organizations, and we have helped many customers make the shift.
How can automation help you?
- Speed up response - remediate threats within minutes, avoiding additional damage and compromise of additional devices
- Reduce workload – self healing is like having a “virtual analyst” in your SOC working 24/7, taking on a significant load of investigations and threat remediations.
- Lower cost of investigations – when auto-IR is handling alerts investigation end to end, your SOC can review and verify only the investigations and remediation actions that are of interest.
Some newly added features are now generally available to make your life even easier:
- A new settings configuration for automation with machine groups
- The ability to do bulk undo commands to change remediation outcomes
- The ability to add to an allow list your line-of-business applications (LOBs) to avoid unnecessary file quarantines using hash indicators
To set up automatic remediation:
- Go to the Microsoft Defender Security Center (https://securitycenter.windows.com), and choose Settings.
- Under General, select Advanced features.
- Turn on Automated investigation.
- In the Permissions section, select Machine groups.
- Select + Add machine group and create at least one machine group. In the Automation level list, select Full – remediate threats automatically.
- If you haven’t set up your machine groups yet, we’ve added a new reminder banner to make sure you do.
Additional new settings for automatic remediation:
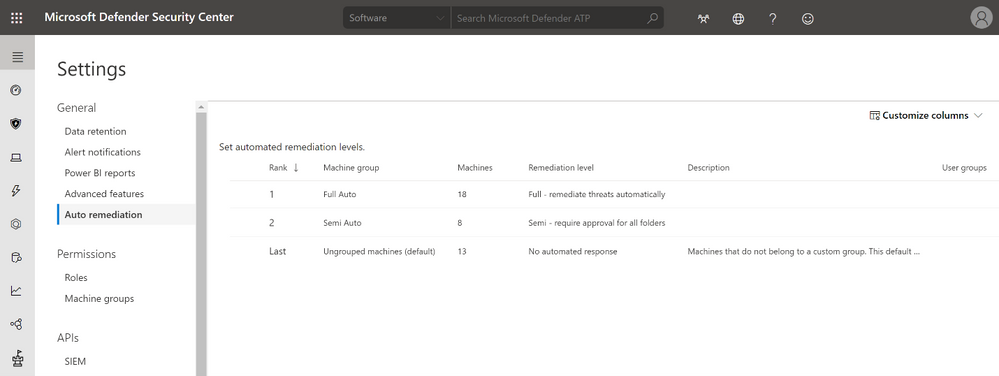
First, you can now set up machine groups to configure automation settings for your groups without requiring global admin permissions. This gives you more autonomy in your security operations teams to drive the right automation behaviors. This can be found under Settings > Auto remediation.
Next, you can select an automation level for each machine group that you create. In your list of machine groups (Settings > Permissions > Machine groups), when you select a row, a fly-out pane opens, enabling you to select the automation level you want. If you have different change controls within your organization, this allows you to effectively set up and manage uniquely your machine group configurations.
Bulk undo:
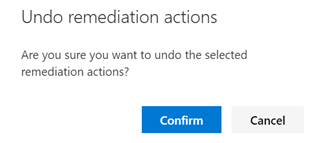
Next, we heard from many customers about adding an ability to do many undo actions at once. We call this capability bulk undo. To use this, go to Automated investigations > Action Center (https://securitycenter.windows.com/action-center), and on the History tab, select the items that you want to undo, such as moving files out of quarantine, as shown below. (You must take this action within 7 days.)
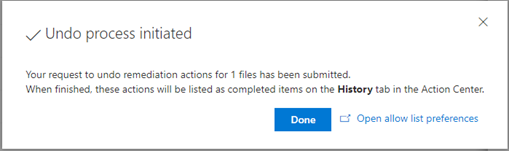
On the confirmation screen, click confirm, and that’s it! You will return to the Action Center, which will reflect the undone action has completed.
Adding applications that may be quarantined to an allow list:
In Automated Investigations > Action Center > History, you can go through, select a specific file(s) to undo remediation actions, and then select Open allow list preferences to add items to an allow list by hash.
The file hash is automatically set. You define an expiration period, (the default is Never), then click Next.
Once you have set this, you will no longer have to worry about any of your applications being flagged as potentially unwanted apps (PUA) and put in quarantine. Instead, your line-of-business apps will be trained in our machine learning playbooks to not take remediation action.
What automation level does Microsoft recommend?
To close out, we recommend that you set all your machine groups to Full – remediate threats automatically. However, we realize that not everyone is ready for that. This is why we offer you flexibility in setting the level of automation that is right for your organization. Here’s a table that describes the various automation levels:
|
Level |
Automation level |
Description |
|
Best (recommended) |
Full - remediate threats automatically |
All remediation actions will be performed automatically. |
|
Better |
Semi - require approval for core folders remediation |
An approval is required on files or executables that are in the operating system directories such as Windows folder and Program files folder. |
|
Good |
Semi - require approval for non-temp folders remediation |
An approval is required on files or executables that are not in temporary folders. |
|
Basic |
Semi - require approval for any remediation |
This is the default automation level. |
Congratulations! You now know how to configure automatic remediation levels and “automate the boring” in your SOC. :smiling_face_with_smiling_eyes:
Let us know what you think by leaving a comment below.
Thank you,
The Microsoft Defender ATP team
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.