- Home
- Security, Compliance, and Identity
- Microsoft Defender for Cloud Apps
- Re: MCAS Policy Creation
MCAS Policy Creation
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 15 2020 01:28 PM
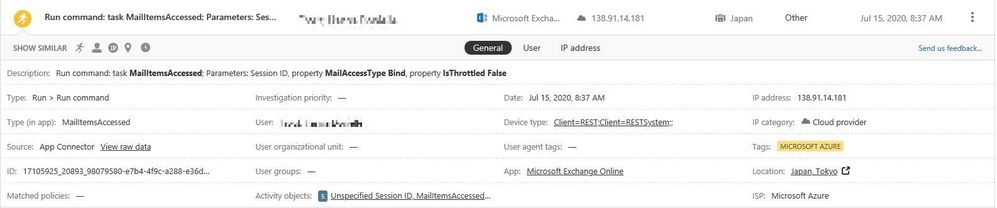
I have noticed an increasing number of accounts being compromised, without generating any alerts I have configured in the Microsoft Cloud App Security portal (Ie. Impossible travel activity)
Is there anyway to create an alert policy for "Run Command: task MailItemsAccessed" when it happens outside of the US?
For example the activity above would generate an alert because the task MailItemAccessed occurred in Japan. What would that policy look like in the MCAS portal?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 15 2020 11:11 PM
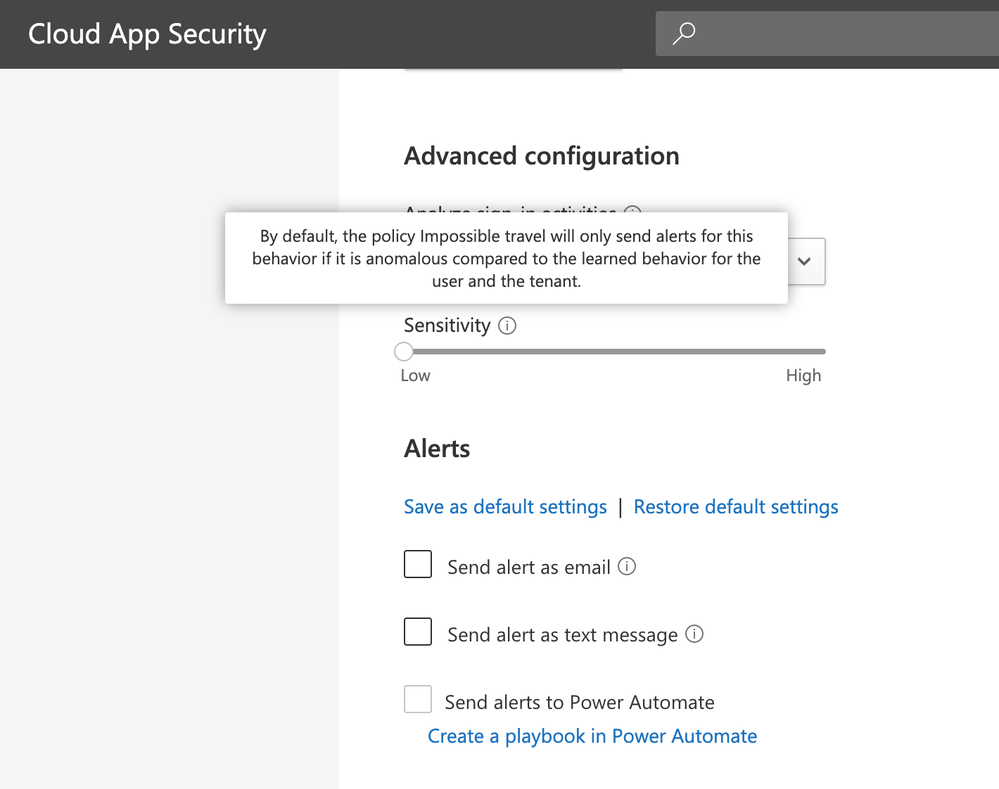
Hi, you could first try changing the sensitivity of the Impossible Travel policy as shown below;
And then ensure you have your alerts configured as required. Have you tried this already?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 16 2020 01:33 PM
@PeterRisingI did try this and I haven't seen any additional alerts being generated since. My main concern is the Impossible Travel policy is looking only at actual sign-in's. I believe what I'm looking to configure an alert for is a Task that is being performed in multiple locations that are considered impossible travel, but I have no idea if that is even possible to configure an alert for.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 17 2020 09:51 AM - edited Jul 17 2020 09:52 AM
Solution@EASchmitt
Does this work for you?
Go to -
Sunglasses (Investigate) -> Activity log -> Advanced (right corner)
- "App" "equals" "Microsoft Exchange Online"
- "Activity objects" "Item" "equals" "MailItemsAccessed"
- "Location" "does not equal" "United States"
If this works, select -> new policy from search and create your policy.
Other things that help:
- In Azure Identity Protection
- Make sure you have a good policy for "User Risk Policy" and "Sign-in risk policy"
- https://portal.azure.com/#blade/Microsoft_AAD_IAM/IdentityProtectionMenuBlade/UserPolicy
- MFA w/conditional access policies
- Include:
- For all users
- Exclude:
- Backup Failsafe account
- CloudApps:
- Office 365 Preview
- Azure Management
- Conditions:
- Sign-in risk- High, Medium
- (Assuming no-one is using legacy auth methods) Client apps- Select All.
- Grant Access
- Require MFA.
- Include:
- Prevent legacy auth with or without conditional access.
- (via Exchange Online Powershell) For Users not using legacy methods (exclude service accounts using internal email services)
- Connect-EXOPSSESSION -UserPrincipalName [insert your email or admin email]
- Sign-In.
- New-AuthenticationPolicy "MFA Required" -AllowBasicAuthPop:$false \ -AllowBasicAuthSmtp:$false \ -AllowBasicAuthImap:$false \ -AllowBasicAuthWebServices:$false \ -AllowBasicAuthOutlookService:$false \ -AllowBasicAuthPowershell:$false \ -AllowBasicAuthReportingWebServices:$false \ -AllowBasicAuthRpc:$false \ -AllowBasicAuthMapi:$false \ -AllowBasicAuthAutodiscover:$false \ -AllowBasicAuthActiveSync:$false
- Set-User -User "Users actual name like 'John Smith'" -AuthenticatonPolicy "MFA Required"
- Connect-EXOPSSESSION -UserPrincipalName [insert your email or admin email]
- For Service Accounts (Set as needed, example SMTP/IMAP)
- New-AuthenticationPolicy "Legacy Service Accounts" -AllowBasicAuthPop:$false \ -AllowBasicAuthSmtp \ -AllowBasicAuthImap \ -AllowBasicAuthWebServices:$false \ -AllowBasicAuthOutlookService:$false \ -AllowBasicAuthPowershell:$false \ -AllowBasicAuthReportingWebServices:$false \ -AllowBasicAuthRpc:$false \ -AllowBasicAuthMapi:$false \ -AllowBasicAuthAutodiscover:$false \ -AllowBasicAuthActiveSync:$false
- Set-User -User "HP-MFP-0120" -AuthenticatonPolicy "Legacy Service Accounts"
- I'd recommend considering moving any accounts like a copier or scanner out of the office 365 environment and into a Amazon-SES if possible.
- (via Exchange Online Powershell) For Users not using legacy methods (exclude service accounts using internal email services)
Hope this helps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 20 2020 06:35 AM
@Jonathan GreenThank you! I was just able to circle back around to this and the first part did exactly what I was looking for.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 17 2020 09:51 AM - edited Jul 17 2020 09:52 AM
Solution@EASchmitt
Does this work for you?
Go to -
Sunglasses (Investigate) -> Activity log -> Advanced (right corner)
- "App" "equals" "Microsoft Exchange Online"
- "Activity objects" "Item" "equals" "MailItemsAccessed"
- "Location" "does not equal" "United States"
If this works, select -> new policy from search and create your policy.
Other things that help:
- In Azure Identity Protection
- Make sure you have a good policy for "User Risk Policy" and "Sign-in risk policy"
- https://portal.azure.com/#blade/Microsoft_AAD_IAM/IdentityProtectionMenuBlade/UserPolicy
- MFA w/conditional access policies
- Include:
- For all users
- Exclude:
- Backup Failsafe account
- CloudApps:
- Office 365 Preview
- Azure Management
- Conditions:
- Sign-in risk- High, Medium
- (Assuming no-one is using legacy auth methods) Client apps- Select All.
- Grant Access
- Require MFA.
- Include:
- Prevent legacy auth with or without conditional access.
- (via Exchange Online Powershell) For Users not using legacy methods (exclude service accounts using internal email services)
- Connect-EXOPSSESSION -UserPrincipalName [insert your email or admin email]
- Sign-In.
- New-AuthenticationPolicy "MFA Required" -AllowBasicAuthPop:$false \ -AllowBasicAuthSmtp:$false \ -AllowBasicAuthImap:$false \ -AllowBasicAuthWebServices:$false \ -AllowBasicAuthOutlookService:$false \ -AllowBasicAuthPowershell:$false \ -AllowBasicAuthReportingWebServices:$false \ -AllowBasicAuthRpc:$false \ -AllowBasicAuthMapi:$false \ -AllowBasicAuthAutodiscover:$false \ -AllowBasicAuthActiveSync:$false
- Set-User -User "Users actual name like 'John Smith'" -AuthenticatonPolicy "MFA Required"
- Connect-EXOPSSESSION -UserPrincipalName [insert your email or admin email]
- For Service Accounts (Set as needed, example SMTP/IMAP)
- New-AuthenticationPolicy "Legacy Service Accounts" -AllowBasicAuthPop:$false \ -AllowBasicAuthSmtp \ -AllowBasicAuthImap \ -AllowBasicAuthWebServices:$false \ -AllowBasicAuthOutlookService:$false \ -AllowBasicAuthPowershell:$false \ -AllowBasicAuthReportingWebServices:$false \ -AllowBasicAuthRpc:$false \ -AllowBasicAuthMapi:$false \ -AllowBasicAuthAutodiscover:$false \ -AllowBasicAuthActiveSync:$false
- Set-User -User "HP-MFP-0120" -AuthenticatonPolicy "Legacy Service Accounts"
- I'd recommend considering moving any accounts like a copier or scanner out of the office 365 environment and into a Amazon-SES if possible.
- (via Exchange Online Powershell) For Users not using legacy methods (exclude service accounts using internal email services)
Hope this helps.