- Home
- Security, Compliance, and Identity
- Microsoft Defender for Cloud Apps
- Adding an external user as MCAS administrator
Adding an external user as MCAS administrator
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 30 2020 05:26 PM
Hi,
My client added my account as guest in their Azure AD (I can access other Azure resources using it) and also added it as an MCAS admin following the instructions described in https://docs.microsoft.com/en-us/cloud-app-security/manage-admins. However, when I login into our MCAS, I don't see their tenant an option to select under my account (as it was supposed to be). I did log out and logged in again, tried different browsers, etc. Are there any additional steps to enable external admins in MCAS? Maybe it takes a while for the permission to apply (this was done several hours ago)? We had no problems adding my account as admin for Defender ATP and Azure ATP (though those work differently from that perspective).
Thanks,
Adrian
- Labels:
-
Cloud App Security
-
MSSP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 02 2020 11:40 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 02 2020 11:48 AM
Not yet, I guess there are some additional requirements that are not documented. We will open a ticket with Microsoft. We have no issue with others like Azure ATP, Defender ATP, Security Center etc. but then they are totally different products.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 02 2020 12:27 PM
Interesting. Might try this myself and see what results I get. Please will you post back if you get a resolution in the meantime? ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 02 2020 12:44 PM
@PeterRising Sure, will do. I've also sent you pm if you want to try it with our test environment.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 02 2020 01:04 PM
I just tried this out between my two test tenants and it worked great first time.
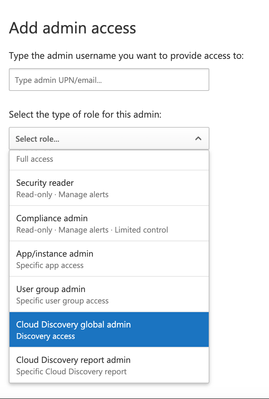
Under Settings > Admin Access, I added Cloud Discovery Global Admin access;
Then on my other tenant (to whom I sent the invite), from the dropdown I was able to select the tenant I'd sent the invite from;
Guessing this is exactly what you also did? ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 02 2020 01:21 PM
Yes, those were the steps but I can't see the client tenant when logging into our tenant (from the account dropdown list). We'll have to check with the client again, maybe they did something wrong though they said they followed the instructions to the letter. Normally, one would get an error if the account they tried to add had some sort of problem.
One thing that maybe has some importance is the fact that my account has been set as "guest" into the client's Azure AD (to perform other administration tasks) but I would think that should not affect the ability to add the same account as external admin in MCAS.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 03 2020 03:57 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 03 2020 08:03 AM
For those interested, after going and back and forth with Peter on this issue, we identified that one can access the customer MCAS portal by using;
https://<organization name>.portal.cloudappsecurity.com/
even when the customer organization doesn't show up as option in our own MCAS Portal when accessed through https://portal.cloudappsecurity.com/.
The trick is to find the actual organization name, as it is not always obvious. Is not clear why some tenants do show in the main portal while other are not, we suspect that it could be a licensing limitation as there are so many possible combinations. The permissions of the MSSP account don't seem to be the problem. If anyone has additional info, it would be great if they can share it.