- Home
- Security, Compliance, and Identity
- Microsoft Defender XDR
- Re: Microsoft Azure and Microsoft 365 security - my defense in depth strategy
Microsoft Azure and Microsoft 365 Security - my defense in depth strategy!
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
Mar 26 2021
08:17 AM
- last edited on
Jan 04 2022
12:37 PM
by
TechCommunityAP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 26 2021
08:17 AM
- last edited on
Jan 04 2022
12:37 PM
by
TechCommunityAP
Dear Microsoft Azure and Microsoft 365 security friends,
Who is interested in my (small) company? We don't have anything to protect and we don't have any money. Besides, we have a firewall. Furthermore, Mr. Wechsler, you are a bit paranoid with your security thinking.
These are the first sentences I always hear when it comes to IT (Cloud) security. But the attacker is also interested in a small company and that is to use their system as a bot.
It's not always about money and data. What about the reputation a company has to lose? It takes years to build a good reputation but only one event to damage the reputation. What about the employees, the trust in the company? Do you want to put this at risk as a company, I don't think so!
Yes! Extended protection mechanisms always cost extra, I am absolutely aware of that. But I also pay monthly for car insurance and accident and health insurance. I'm grateful every day when I don't need the insurance. That's exactly how it should feel when it comes to IT (cloud) security.
Let's start with my IT/Cloud security strategy. I am absolutely aware that this list is not exhaustive. There are so many components to consider, plus every infrastructure/company is always different. I'll try to give you a little help here.
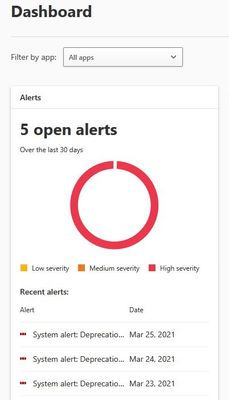
We start with Microsoft 365, as a first additional measure, use all policies that start with "Anti-". You can find all the information in the Microsoft 365 Security Center.
https://security.microsoft.com/threatpolicy
The next step is to use the policies that start with "Safe". You can also find this information in the Microsoft 365 Security Center.
Multi factor authentication is a key element to further protect your identities/users. You can set this up per user or with a Conditional Access Policy (my preferred way). Azure Active Directory helps you integrate this protection.
https://portal.azure.com
If you are subject to a regulatory agency, the Microsoft 365 Compliance Center can help. Here you can set up data loss prevention policies, audits, eDiscovery and much more.
https://compliance.microsoft.com/homepage
In this day and age of bring your own device and work from home, it's a good idea to include the Endpoint Manager. With it you have the possibility to manage endpoints (Mobile Device Management - MDM) and applications (Mobile Application Management - MAM).
https://endpoint.microsoft.com/
Get visibility into your cloud apps using sophisticated analytics to identify and protect against cyberthreats, detect Shadow IT, and control how your data travels.
https://portal.cloudappsecurity.com/
The Cloudapp Security Portal provides you with the best possible support. Here you can allow or sanction cloud app, configure anti-ransomware policies, data loss prevention policies and much more.
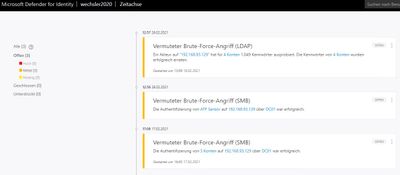
Do you want to know how your Windows Active Directory is doing? Then Microsoft Defender for Identity will help you. With this tool you can transfer the local information to the cloud. With an interface to the CloudApp Security Portal.
https://yourtenant.atp.azure.com/timeline
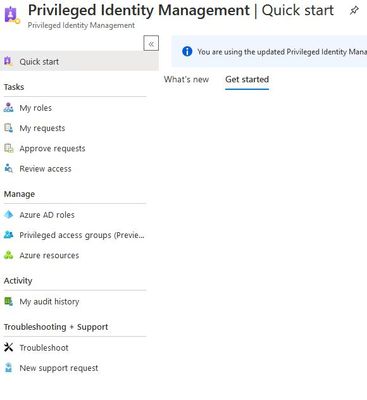
No person should always work with elevated rights. Only work with elevated rights when it is really necessary. This is where Azure Privileged Identity Management (PIM) comes in. With this tool you can configure the access as you need it for your needs.
https://portal.azure.com
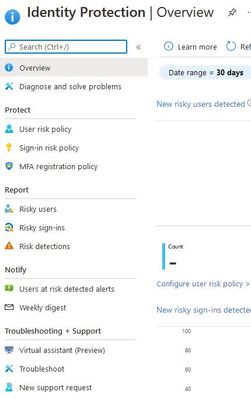
With Azure Identity Protection do you have a tool that allows organizations to accomplish three key tasks:
1. Automate the detection and remediation of identity-based risks.
2. Investigate risks using data in the portal.
3. Export risk detection data to third-party utilities for further analysis.
https://portal.azure.com
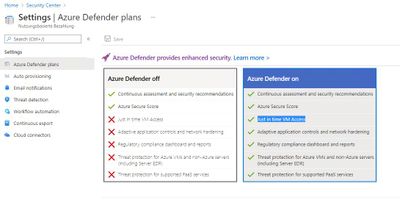
Just in time access for administrators, this is also possible for virtual machines with Just in time VM Access. In Microsoft Defender for Cloud you can configure this feature (and much more).
Microsoft Sentinel helps you keep track of the health of your organization. A SIEM (Security Information and Event Management) and SOAR (Security Orchestration Automation and Response) tool that should not be missing from your portfolio. The tool offers many connectors (98 at the moment) so that you can connect the most diverse portals to Sentinel.
There is still so much to show, I wasn't talking about Role Based Access Control (RBAC) now or Network Security Group (NSG), etc. I know some of you are thinking, hey there is a lot more. I am aware of that. My goal is to give you some positive signals on how you can integrate additional security into your organization.
Thank you for taking the time to read this article.
Kind regards, Tom Wechsler
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 07 2021 12:24 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 07 2021 04:18 AM