- Home
- Security, Compliance, and Identity
- Microsoft Defender XDR
- Malware/Threat TrojanSpy:MSIL/AgentTesla.AQ!MTB: False positive?
Malware/Threat TrojanSpy:MSIL/AgentTesla.AQ!MTB: False positive?
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 21 2020 08:21 AM
Hello!
Windows Defender (Windows 10 Pro x64 v1909 build 18363.1016) has blocked 3 times AgentTesla malware on a dual-boot machine (with Linux Mint 19.2 x64). As you may see in the picture below ,it does not say from where it was removed.
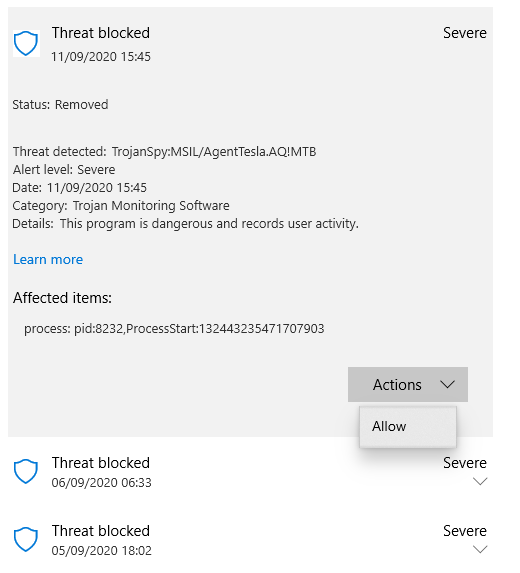
In my own research I could find that AgentTesla is one of those malware which steal and transmit/disclose user info and as well as acts as gateway for ransomware. It is a .NET-based malware.
Microsoft says that "Windows Defender Antivirus detects and removes this threat.". Nonetheless, I have done my best to find and remove it but I was not successful. I have employed:
Windows Defender, which has been run in quick, full, custom (c:\ only) & offline modes;
Microsoft Safety Scanner;
Linux: clamav (from Cisco), running twice with and without the extra unofficial malware signatures;
Bootable Rescue Disks (.iso) from Norton, Trend Micro and Avira.
Windows-based tools Norton Power Eraser and Trend Micro tool.
As I have aforementioned, none of them have found it (okay, it may have been indeed removed).
I would like to know if those notifications could be some sort of false positive. I have never received what seems to be a false positive notification from Microsoft Defender. It have to admit it has startled me. Moreover, may I render this machine as clean?
As usual, all signatures / virus intelligence were updated before scanning.
Thank you,
Sandro
References:
https://krebsonsecurity.com/2018/10/who-is-agent-tesla/
https://www.fortinet.com/blog/threat-research/analysis-of-new-agent-tesla-spyware-variant
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 12 2020 12:18 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 08 2021 06:00 PM - edited Jan 08 2021 06:10 PM
After all this time, my educated guess is that Windows Defender has blocked the malware/threat via its capability of scan incoming network data - the same as other antivirus/firewall bundles do. Therefore, the infection was put aside (and destroyed) before it has reached its final destination e.g., Edge.
And since it was destroyed, this is the reason why I could not find it, no matter how hard I have tried.
And thanks @Cymon_Skinner but there was nothing useful at that location on event log by time I wrote my initial message in September/20 - quite strange, wasn't it? It was the very first place I looked.