- Home
- Security, Compliance, and Identity
- Microsoft Defender XDR
- Can you help me in this query
Can you help me in this query
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 03 2020 03:24 AM
let outlookLinks =
DeviceEvents
| where Timestamp > minTimeRange and ActionType == "BrowserLaunchedToOpenUrl" and
isnotempty(RemoteUrl)
| where
InitiatingProcessFileName =~ "outlook.exe"
or InitiatingProcessFileName =~ "runtimebroker.exe"
| project Timestamp , DeviceId , DeviceName , RemoteUrl, InitiatingProcessFileName,
ParsedUrl=parse_url(RemoteUrl)
| extend WasOutlookSafeLink=(tostring(http://ParsedUrl.Host) endswith "http://safelinks.protection.outlook.com")
| project Timestamp , DeviceId, DeviceName , WasOutlookSafeLink,
InitiatingProcessFileName,
OpenedLink=iff(WasOutlookSafeLink, url_decode(tostring(ParsedUrl["QueryParameters"]["url"])), RemoteUrl);
let alerts =
AlertInfo
| summarize (FirstDetectedActivity, Title)=argmin(Timestamp,Title) by AlertId,
| where FirstDetectedActivity > minTimeRange;
alerts
| join kind=inner (outlookLinks) on DeviceId
| where FirstDetectedActivity -
Timestamp between (0min..3min)
| summarize FirstDetectedActivity=min(FirstDetectedActivity),
AlertTitles=makeset(Title) by OpenedLink, InitiatingProcessFileName,
EventTime=bin(Timestamp, 1tick), DeviceName, DeviceId , WasOutlookSafeLink
links opened from outlook.exe, followed by warning that was ignored by the user.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 03 2020 10:29 AM
Hello @Shviam ,
We are parsing the Safe Links urls for you ![]()
Therefore in the first part of the query, you don't need to parse the url:
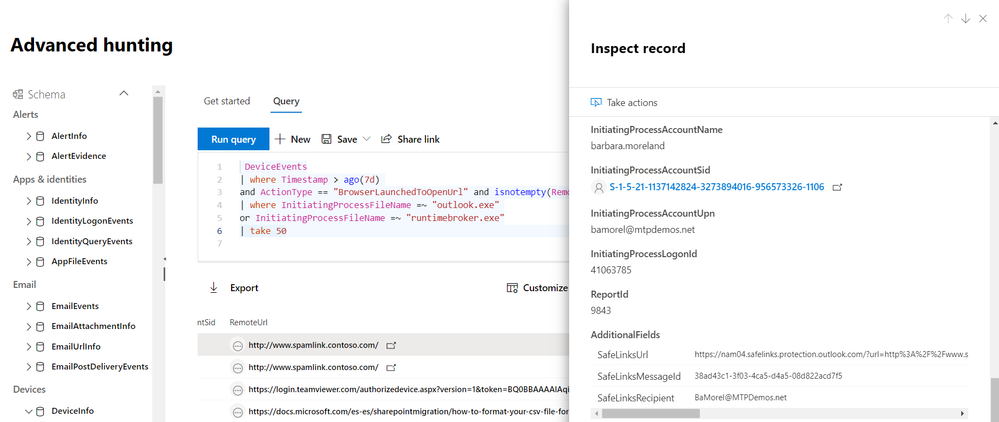
- In the column RemoteUrl we are giving you the actual target url, that in case of Safe Links is "behind" the Safe Links url.
- In AdditionalFields you will have the Safe link complete url, in case this link was a Safe Links url. Using: | extend SafeLinksUrl = tostring(parse_json(AdditionalFields)["SafeLinksUrl"]), you can extract it and get the complete url. In case the url was not a Safe Links, SafeLinksUrl will be null.
An example :
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 04 2020 07:17 PM
@Tali AshThanks a lot
I'm trying to create an analytic rule for which user clicked on the malicious link and they got the warning sign" The URL is in an email message that seems similar to other email messages that are considered suspicious. We recommend that you double-check the email message before proceeding to the site."
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 06 2020 07:35 AM