- Home
- Microsoft Intune and Configuration Manager
- Intune Customer Success
- Without-Enrollment and Outlook for iOS & Android General App Configuration
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
In January and March, Outlook for iOS and Android launched support for delivering configuration settings when the app is deployed on enrolled devices.
With an Intune service update rolling out this week, administrators will be able to customize the default configuration for several in-app settings when Outlook for iOS and Android has an Intune App Protection Policy applied. That’s right, device enrollment is no longer a condition to manage the general app configuration of Outlook for iOS and Android!
In addition, with this update, administrators can also manage Outlook for iOS and Android’s data protection settings and contact field sync controls within an App Configuration Policy. Admins no longer need to manage these settings with configuration key pairs when using Intune.
Once the Intune rollout is complete, you can either create a new App Configuration Policy with a device enrollment type of “Managed Apps” or update an existing policy to leverage the new controls when the policy is targeted against Outlook for iOS and Android. For existing policies, the configuration keys are automatically consumed in the new policy experience. For more information on which settings are available and how to configure a policy, please see Deploying Outlook for iOS and Android app configuration settings. You can also review Add app configuration policies for managed apps without device enrollment for general steps on how to create a policy.
In deployments where you have both enrolled devices and unenrolled devices, or perhaps only enrolled devices, you may be wondering what type of an App Configuration Policy you should now utilize for managing Outlook's general app configuration settings. If an App Protection Policy is targeted to the users, the recommendation is to deploy the general app configuration settings in a “Managed Apps” enrollment model. This ensures the policy is deployed to both enrolled devices and unenrolled devices.
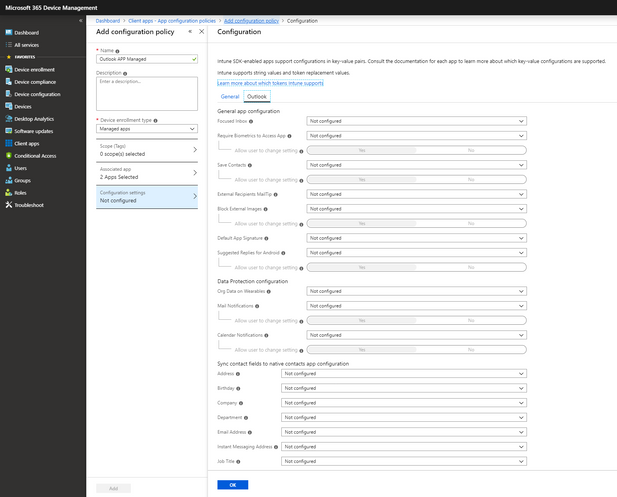
Figure 1: Managed apps App Configuration Policy for Outlook for iOS and Android from https://devicemanagement.microsoft.com. If you're in https://portal.azure.com, then you'll go to Intune -> Client apps -> App configuration policies and add a configuration policy.
In order for the app to apply the policy settings, Outlook for iOS 3.32.0 and later must be installed. Outlook for Android 3.0.108 and later is required; however, that build will not be available to all users until the end of next week.
We hope this functionality aids you in your deployments. If you have any questions, please let us know!
Ross Smith IV
Principal Program Manager
Customer Experience Engineering
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.