- Home
- Microsoft Intune and Configuration Manager
- Intune Customer Success
- Setup Assistant with modern authentication for ADE - Intune Public Preview
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Updated 8/27/21: We're excited to take the preview tag off and share that Setup Assistant with modern authentication for ADE (iOS/iPadOS 13+ and macOS 10.15+) is now generally available! See Automatically enroll iOS/iPadOS devices by using Apple's Automated Device Enrollment on how to use this authentication method on iOS/iPadOS devices, and Automatically enroll macOS devices with the Apple Business Manager or Apple School Manager for macOS devices.
We’re excited to announce support for a new authentication method for Apple's Automated Device Enrollment (ADE) which is Setup Assistant with modern authentication. This new authentication method is available for iOS/iPadOS devices running 13.0 and later and for macOS devices running 10.15 and later, in public preview in Microsoft Endpoint Manager.
For automated device enrollment scenarios where the authentication method is Setup Assistant with modern authentication, you can create a filter rule based on the enrollment profile name (enrollmentProfileName). See: Using filters with Setup Assistant with modern auth for ADE for corporate iOS/iPadOS/macOS devices to learn more.
Overview
When creating an ADE enrollment profile, you can choose a new authentication method: Setup Assistant with modern authentication. This authentication method for ADE allows your organization to require authentication with Azure Active Directory (Azure AD) in an out-of-box experience (OOBE) during enrollment with Setup Assistant, prior to users accessing the home screen. You have the option to also require multi-factor authentication (MFA) depending on the settings in your Conditional Access policy.
Users are required to authenticate with their Azure AD credentials twice: once during enrollment with Setup Assistant, and then again when they sign in to the Company Portal. After initial authentication with Azure AD during Setup Assistant, the home screen appears, and users can freely use the device for resources not protected by Conditional Access. User affinity is established when a user arrives at the home screen after the setup screens. However, the device will not show in a user's device list in the Azure AD portal until the user signs in to Company Portal. The additional sign in to the Company Portal app fully completes a device’s Azure AD registration and gives the user access to corporate resources protected by Conditional Access. This method provides all the security of authenticating with the Company Portal but doesn’t make users wait until the Company Portal installs on the device before they can start using it.
The correct Company Portal version will automatically be delivered as a required app to the device for iOS/iPadOS. We recommend choosing a Volume Purchase Program (for the enrollment profile. Otherwise, it will be delivered when the user sets up their Apple ID during the Setup Assistant screens. To learn how to get the Company Portal on macOS devices, see Add the Company Portal for macOS app.
Company Portal Redirection
A new improvement we’ve made to our onboarding experience helps guide users to complete that second Azure AD authentication by automatically redirecting to the iOS/iPadOS Company Portal when the user attempts to access corporate data.
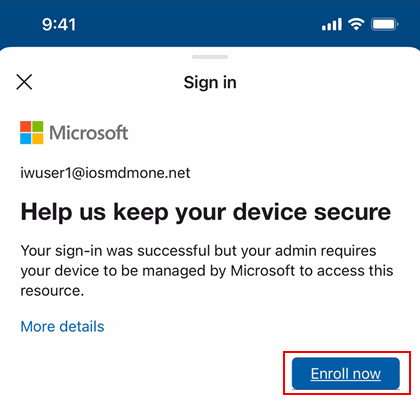
If users open any managed iOS/iPadOS applications that are protected by Conditional Access and they haven't completed the additional Azure AD sign in to the iOS/iPadOS Company Portal, they will be redirected to the Company Portal from those other apps as part of this new change. This way, users are guided to complete that last step before they can access resources protected by Conditional Access.
Here is what it will look like if a user tries to open an app protected by Conditional Access before authenticating in the Company Portal:

Configuration in Microsoft Endpoint Manager admin center
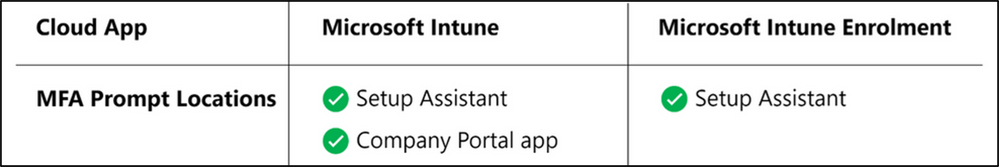
The Intune documentation explains how to configure the Setup Assistant with Modern Authentication for iOS/iPadOS device enrollment and macOS device enrollment. In the Microsoft Endpoint Manager admin center, you can a user for multi-factor authentication. For instructions, see Require multi-factor authentication for Intune device enrollments. The following screenshot provides an example of the prompt locations:
Enrolling devices with user device affinity but without Azure AD registration
For both iOS/iPadOS and macOS, user device affinity (also known as primary user) in Intune is established when a user lands on the home screen after the Setup Assistant screens. However, the device is not fully registered with Azure AD until the additional sign in to Company Portal, as mentioned above. This is also when device compliance is assessed, and the device shows as compliant in the Microsoft Endpoint Manager admin center. However, if you would like to keep devices fully enrolled with Intune but without Azure AD registration, this is also supported.
After the user completes the initial Azure AD sign in during Setup Assistant, if there are no resources protected by Conditional Access and if Azure AD registration is not required, then this authentication method can be used to fully enroll the device. If you choose this ADE flow, which does not require users to sign in to the Company Portal post enrollment, you will see the following device behavior:
- The device will not show up in a user’s device list in the Azure AD portal (since there is no device identity association within Azure AD).
- The device will not show up as compliant in the Microsoft Endpoint Manager admin center.
Keep in my mind
-
When enrolling an iOS/iPadOS device with Setup Assistant with Modern Authentication, app configuration policies are automatically applied to the iOS/iPadOS device. Don’t send a separate app configuration policy to the Company Portal for those iOS/iPadOS devices or it will result in an error.
-
If you choose Setup assistant with Modern Authentication as the authentication method for a device that is not running the correct software version, users will fall back to the legacy Setup Assistant ADE flow.
- For iOS/iPadOS, we recommend selecting to install the Company Portal app from a VPP token in the enrollment profile. When VPP is used, the application can be downloaded and installed without user interaction. When VPP isn't used, an Apple ID is required to install the application. If the user doesn't sign in to an Apple ID during Setup Assistant, they will be prompted to sign in when Intune attempts to install the Company Portal.
- For more information about connecting Intune to Apple Volume Purchase Program (VPP), see How to manage iOS and macOS apps purchased through Apple Business Manager with Microsoft Intune. Once you have connected to VPP you can add the Company Portal app to your Apple Business Manager/Apple School Manager inventory so it can be assigned through Intune.
Let us know if you have any questions by commenting on this post or reaching out to @IntuneSuppTeam on Twitter.
Post updates:
8/20/21 - added post on using filters with Setup Assistant with modern auth for ADE for corporate iOS/iPadOS/macOS devices.
8/26/21 - we're excited to take the preview tag off and share that Setup Assistant with modern authentication for ADE (iOS/iPadOS 13+ and macOS 10.15+) is now generally available!
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.