- Home
- Microsoft Intune and Configuration Manager
- Intune Customer Success
- Managing Microsoft Teams Rooms with Intune
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
We’ve heard a few questions recently from customers looking for guidance how to manage your Microsoft Teams Rooms devices with Intune. This post answers a few of the frequently asked questions and provides general guidance. If you’ve discovered additional tips or tricks on your deployment journey, or have other feedback or suggestions, let us know by commenting on this post!
Teams Room devices can be enrolled and managed by Intune to provide many of the device management and security capabilities available to other endpoints managed by Intune. Because these devices run Windows 10 under the hood, several of the Windows 10 features will be available to use, but many are not applicable or recommended.
In break this post, we'll discuss recommendations for these Intune feature areas:
- Enrollment
- Windows 10 configuration profiles
- Compliance policies
- Conditional Access
- Grouping and targeting
Enrollment
Recommendation: Use an Intune DEM account to Azure Active Directory (Azure AD)-join the device from Windows Settings.
Windows 10 based Teams devices arrive from suppliers prepared with an OS image, user accounts, and pre-configured profiles. For a smooth, automatic MDM enrollment, sign in to the device with the admin profile and perform the Azure AD join from the Settings menu. We recommend you use an Intune device enrollment manager (DEM) account specifically because Teams Room devices are shared and DEM accounts are more practical for managing shared-device scenarios. Learn more about DEM accounts here.
The Teams Rooms resource account can be used for Intune enrollment, but it should not be used for Windows 10 sign-in on the device because it can cause issues during automatic sign-in of the Microsoft Teams Room application account. Please use a tenant or device admin account to administer local device settings.
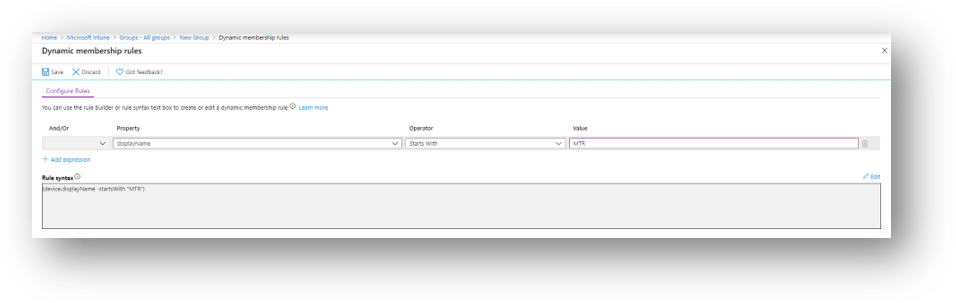
An additional tip is to name Teams Room devices with a prefix that allows devices to be grouped dynamically. For example, use “MTR” for meeting room. You can rename devices with either a Windows 10 configuration policy or manually per device in Intune. We’ll talk about this approach a bit more below, under Grouping and Targeting.
Depending on your current scenario, there are several other enrollment options available:
- Use Windows Configuration Designer to create a Windows 10 provisioning package that performs a bulk Azure AD Join. Details are here.
- Customers who have some devices domain joined and/or managed by Configuration Manager may choose to enable co-management or initiate an Intune enrollment via the Enable automatic MDM enrollment using default Azure AD credentials Group Policy setting.
For more details about available enrollment methods, see Intune enrollment methods for Windows devices.
Windows 10 Configuration Profiles
Recommendation: Use Windows configuration profiles to configure device settings that you need to change beyond the shipped defaults.
The following Windows 10 Configuration Policy types may be used with Windows 10 based meeting room devices:
|
Profile type |
Can you use the profile? |
|
Administrative Templates |
Yes |
|
Certificates |
Yes |
|
Delivery Optimization |
Yes |
|
Device Firmware Configuration Interface |
Check for supported hardware here |
|
Device restrictions |
Yes |
|
Edition Upgrade |
Not supported |
|
|
Not recommended |
|
Endpoint Protection |
Yes |
|
eSim |
Not supported |
|
Identity Protection |
Not supported |
|
Kiosk |
Not supported |
|
PowerShell Scripts |
Yes (Devices must be Azure AD joined or hybrid Azure AD joined) |
|
Security baselines |
Not supported |
|
Shared multi-user device |
Not supported |
|
VPN |
Not recommended |
|
Wi-Fi |
Not recommended |
|
Windows Information Protection |
Not recommended |
NOTE: “Not recommended” in the table means that the Windows 10 policy type is not a good fit for Teams Room scenarios. For example, Team Room devices are not enabled for Wi-Fi, therefore it’s not recommended (or necessary) to configure a Wi-Fi profile. Learn more about available configuration policies here: Create a device profile in Microsoft Intune.
Compliance policies
Recommendation: Use compliance policies to achieve the desired security level for your Teams devices.
You can use compliance policies on your Teams Room devices. Make sure to create the appropriate exclusions for any existing Windows 10 compliance policies that are currently deployed in your organization to All devices. For example, you may have configured the setting Maximum minutes of inactivity before password is required in a policy for all Windows 10 desktop devices but this would result in a poor meeting room experience if applied to Teams Room devices. If you currently have Windows 10 compliance policies deployed to large groups of devices, make sure you use the Exclude group feature so that you can target a more specific compliance policy for the Teams Room devices.
For detailed guidance, see Use compliance policies to set rules for devices you manage with Intune.
Conditional Access
Conditional Access policies with only location-based conditions can be applied to Microsoft Teams Rooms accounts at this time. Microsoft is currently working on updates that will allow additional conditions to be set, such as device compliance.
Grouping and Targeting
It’s helpful to use Azure AD dynamic groups to effectively group all Teams Room devices. To help implement this more easily, use a naming standard during deployment/enrollment. For example, as mentioned earlier in this article, if you want to prefix all device names with “MTR," you can use “MTR-%SER%” to name your devices, which will append the device serial number to the prefix. Then you can use the dynamic group feature to group together all devices that start with MTR. Keep in mind, Azure AD dynamic groups is an Azure AD P1 feature.
NOTE: Device renaming via Intune device management is supported on Azure AD-joined devices but not hybrid Azure AD-joined devices.
When targeting configuration profiles, compliance policies, and apps it’s a good idea to target a group that contains devices rather than users. The reason for device-group assignment is that Teams Room devices sign in to Windows with a local user account (instead of an Azure AD user account) and during sync with Intune, would not request any user-assigned policy.
More info and feedback
As always, we want to hear from you! If you have any suggestions, questions, or comments, please comment below. You can also tag @IntuneSuppTeam on Twitter.
Blog post updates:
- 1/21/2022: Updated Windows 10 configuration profile table to show that security baselines are not supported, removed requirement for Azure AD Premium (now included), additional minor edits.
- 1/27/2021: Updated the More info and feedback section.
- 4/20/2020: Updated the post to include an enrollment best practice: " The Teams Rooms resource account can be used for Intune enrollment, but it should not be used for Windows 10 sign-in on the device because it can cause issues during automatic sign-in of the Microsoft Teams Room application account. Please use a tenant or device admin account to administer local device settings.
- 3/6/2020: Updated the post to clarify what works with Conditional Access and Microsoft Teams Rooms. Removed mention of device compliance checks for CA; that feature is coming.
- « Previous
-
- 1
- 2
- Next »
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.