- Home
- Microsoft Intune and Configuration Manager
- Intune Customer Success
- Intune certificate updates: Action may be required for continued connectivity
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Update 2/10/2020: The certificates have all now been rotated for Intune. If you or your end users did not take action, such as updating the apps, the Android Company Portal, or if you did not you did not update the SDK or rewrap your line of business apps, here’s the end user experience moving forward:
Existing user with App Protection Policy (APP, also known as MAM) policy:
- They will continue to be protected with the last APP/MAM policy they received.
- They will not get any updates to that existing policy.
- After 90 days (configurable) the corporate data and apps with APP on the device will be wiped. Ninety days from today puts this change on May 12, 2021.
- A few questions have come in around block access. There is a separate block access after 12 hours but that will only apply if your user is not connected to the internet (for example, completely offline).
New user without APP policies:
- They will not be able to get policy to enroll the app and thereby will not be able to use the APP managed application.
- If you did not update the SDK or rewrap your line of business (LOB) apps, then apps cannot continue communicating with the Intune service. If an APP LOB application was wrapped or you are using default enrollment, new users will be blocked from accessing the app.
- The majority of LOB apps fall in this category.
- If they have the Conditional Access policy requiring APP in place, new users will be blocked from getting an access token.
- If they don't have either of these protections in place, they will get application access.
You can still take action by:
- Ensuring Android end users have updated their Company Portal app to the latest version (this change and a number of fixes have been in the Company Portal app since 5.0.05 and higher). On Android, updating the company portal will also update any APP apps.
- If you use any Microsoft applications with App Protection Policies (APP, also known as MAM), you’ll want to ensure you’re using the latest application versions from Microsoft. All the major Office apps have adopted the newer SDK’s and are available in the store.
Please see the post below for the connector information/updates and more information.
From the original post in November, 2020 - Today we're posting the following message in the Message Center (in M365 Admin center under Message Center or in Microsoft Endpoint Manager on the Tenant Admin blade - Service Health and Message Center). We're sharing here to help answer any questions and also to keep you posted on any new updates.
MC225591 (and also MC235267 as a reminder!) - Intune certificate updates: Action may be required for continued connectivity
Microsoft Intune has begun updating our Root certificates to comply with Azure’s new certificate policy. Most management scenarios will work without administrator action, however, there are a few different configurations that may require you to take action to ensure your continued connectivity to Intune.
How this will affect your organization:
Here are the scenarios that are affected and may need action:
- If you use the Intune iOS SDK, Intune App Wrapper for iOS, or Xamarin Bindings, we posted MC222833 asking you to take action and describing which versions are needed.
- If you use any Microsoft applications with App Protection Policies (APP, also known as MAM), you’ll want to ensure you’re using the latest application version with SDK for iOS (SDK version 12.9.0+ has the updated code) or SDK for Android (SDK version 6.7.2+ has the updated code). All the major Office apps have adopted the newer SDK’s and are available in the store.
- If you use Configuration Manager, including co-managed devices, read this article for any conditions that need to be unblocked to enable the root cert updates, such as steps to ensure Windows domain joined co-managed devices continue communicating with the Microsoft Endpoint Manager services.
- For any Intune on-premises connectors in use, such as the Exchange, NDES, ODJ, or PFX connectors, ensure your servers receive the Root Certificate updates. For environments that are disconnected, follow guidance to ensure root certificates are installed on the on-premises servers.
- Note that you may also have to check your Group Policy settings, as it is possible to disable automatic root certificate updates. Update your policy or manually update the certificates on devices including MDM-managed Windows devices.
What you need to do to prepare:
Evaluate your environment with the conditions above and take action as needed.
And for those of you that didn't see MC222833 and later MC230351 but have LOB apps with APP (MAM) here's that post too:
MC222833 (and also MC230351 as a reminder) - Take Action: Adopt the Latest iOS SDK, Intune App Wrapper, and Xamarin Bindings
Microsoft has made a few important service side updates that will require that you adopt the latest Intune App SDK for iOS version 12.9.0 or higher, Intune App Wrapper, version 13.0.0 or higher, or Xamarin binding version 12.9.0 and then have your end users adopt the updated apps by December 31, 2020. Note that the way Android updates, once one Microsoft application with the updated SDK is on the device and the Company Portal is updated, Android apps will update, so this message is focused on iOS.
How this will affect your organization:
Our service telemetry indicates you have applications wrapped by the Intune SDK, the Intune App Wrapper, or Xamarin Bindings.
What you need to do to prepare:
Action will depend on update status:
- If you've wrapped your app, you'll want to re-wrap your app with the latest wrapper (13.0.0 or higher)
- If you integrated the SDK please re-integrate with SDK 12.9.0 or higher
- If you're using Xamarin and have integrated our binding, please pull in the binding 12.9.0 or above
Here are the public repositories:
FAQ (we'll add to this over time provided questions are asked!)
Q: What does an NDES server update look like?
A: We asked one of our service engineers and here's a few steps.
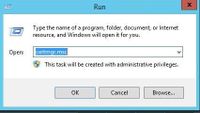
- On the Windows device, Launch/run certlm.msc. Say yes.
Go to Trusted Root Certification Authorities - Open Certificates and ensure the "DigiCert Global Root G2" is there. If it is, you're set!
- If not, the Microsoft Endpoint Manager post here: https://docs.microsoft.com/en-us/troubleshoot/mem/configmgr/connectivity-issues-digicert-global-root... lists common reasons why the cert is not installed.
- In our service engineer's environment, it actually wasn't there, so he got the cert by going to the Trusted Root Certificate Store as described in the above doc.
One of our customers ran into an issue that the certs were downloaded but weren't being applied. Here's the steps they went into on the Exchange connector server to ensure they applied. If you have any other tips let us know!
- Logged into the Exchange Connector server with a local user account.
- From Windows, accessed the Cert manager with certmgr.msc from the Command prompt. One note - if you are logged with different domain account you can add how to access to Run as Steps to access Cert manager.
-
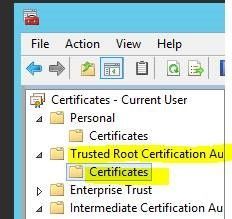
Once you're in Cert manager on the Exchange Connector server, click on Trusted Root Certificate Authority > certificates.
-
Right Click on Certificates > click All Task > and then Import.
-
After Import, select the certs you want to import from your local drive (in this case the new ones).
-
Once you select it will install and ask for confirmation. Then you'll see your new certificates.
Network Access Control (NAC) note
For all Network Access Control (NAC) scenarios, when using a 3rd party provider such as Cisco, please be sure your NAC provider has validated their root CA config. They should have how to do this documented, but in case they don’t:
- Add DigiCert Global Root G2 to their trusted CA store.
- For some providers, they many need to validate the configuration and update as needed.
- Confirm your network can receive traffic so that the configuration can be pushed down to individual ISE boxes.
- For some providers note that it can take time for updates to be distributed.
Updated
- 11/2/2020 with more info on NDES server cert updates.
- 2/2/2021 with Exchange Connector detailed instructions if the certs were downloaded but not applied steps and steps for NAC providers.
- 2/11/2021 with the latest information now that the certs have been rotated.
Let us know if you have any additional questions on this by replying back to this post or tagging @IntuneSuppTeam out on Twitter.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.