- Home
- Microsoft Intune and Configuration Manager
- Intune Customer Success
- Decreasing support for Android device administrator
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Android device administrator management was released in Android 2.2 as a way to manage Android devices. Then beginning with Android 5, the more modern management framework of Android Enterprise was released (for devices that can reliably connect to Google Mobile Services). Google is encouraging movement off of device administrator management by decreasing its management support in new Android releases.
How does this affect me?
Because of these changes by Google, in October 2020 you will no longer have as extensive management capabilities on impacted device administrator managed devices.
Note: This date was previously communicated as fourth quarter of 2020, but it has been moved out based on the latest information from Google.
Device types that will be impacted
Devices that will be impacted by the decreasing device administrator support are those for which all three conditions below apply:
- Enrolled in device administrator management
- Running Android 10 or later
- All Android manufacturers, except Samsung
Devices will not be impacted if they are any of the below:
- Not enrolled with device administrator management
- Running an Android version below Android 10
- Samsung devices (Samsung Knox devices won't be impacted in this timeframe because extended support is provided through Intune’s integration with the Knox platform. This gives you additional time to plan the transition off device administrator management for Samsung devices.)
Settings that will be impacted
Google's decreased device administrator support prevents configuration of these settings from applying on impacted devices.
Configuration profile device restrictions settings:
- Block Camera
- Set Minimum password length
- Set Number of sign-in failures before wiping device (will not apply on devices without a password set, but will apply on devices with a password)
- Set Password expiration (days)
- Set Required password type
- Set Prevent use of previous passwords
- Block Smart Lock and other trust agents
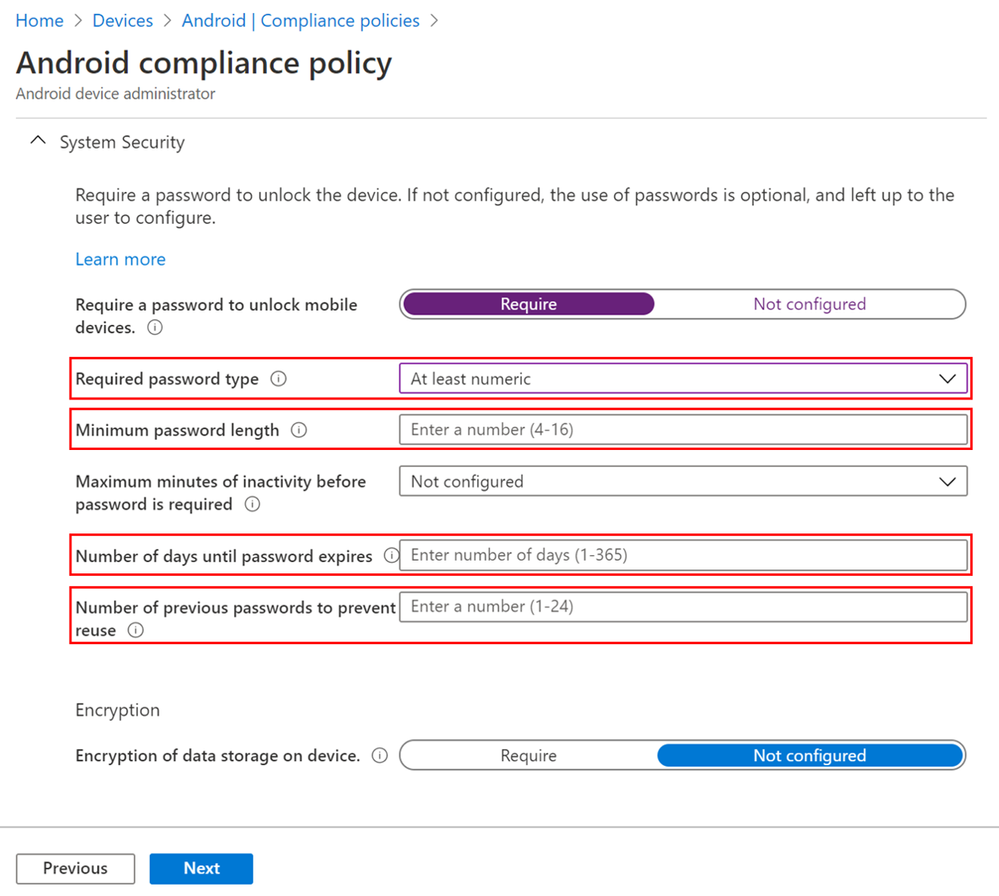
Compliance policy settings
- Set Required password type
- Set Minimum password length
- Set Number of days until password expires
- Set Number of previous passwords to prevent reuse
User experience of impacted settings on impacted devices
Impacted configuration settings:
- For already enrolled devices that already had the settings applied, the impacted configuration settings will continue being enforced.
- For newly enrolled devices, newly assigned settings, and updated settings, the impacted configuration settings will not be enforced (but all other configuration settings will still be enforced).
Impacted compliance settings:
- For already enrolled devices that already had the settings applied, the impacted compliance settings will still be enforced in the Settings app and the user will still be compliant. The Microsoft Endpoint Manager console will report these impacted settings on these devices as Not Applicable.
- For newly enrolled devices, newly assigned settings, and updated settings, the impacted compliance will not be sent down to the device, so they will not be enforced in the Settings app and the user will still be compliant. The Microsoft Endpoint Manager console will report these impacted settings on these devices as Not Applicable.
Additional user experience change for Wi-Fi profiles:
- Users will need to accept additional permissions, and explicitly accept Wi-Fi configurations when they're deployed. Note: Wi-Fi configurations will not appear in the known Wi-Fi networks list, but will automatically connect when in range.
- If the user disconnects from the Wi-Fi network manually, the network appears in the network list as “Available via Company Portal” and the user can manually reconnect. If you unassign a Wi-Fi profile for a network a device is connected to, the device will be disconnected the next time it checks into Intune.
- There are no changes in behavior for existing Wi-Fi profiles. There are also no changes to the admin experience in the Microsoft Endpoint Manager admin center.
Custom Wi-Fi profiles with pre-shared keys:
- As communicated in MC223443, an additional change is happening with October's Company Portal release where you will no longer be able to create custom Wi-Fi profiles to include a pre-shared key (PSK) in the profile.
- How will this affect you: If you use custom Wi-Fi profiles in order to include a PSK in the profile, this will continue working for devices that already have the profile installed but the policies will no longer work for newly-enrolled Android 10+ devices once the Company Portal upgrades in October.
- What you need to do to prepare: If possible, we encourage you to move to Android Enterprise. If not, make sure all Wi-Fi profiles for Android device administrator are set before October's Company Portal release expected to start mid-October.
Cause of impact
Devices will begin being impacted in October 2020. At that time, there will be a Company Portal app update that will increase the Company Portal API targeting from level 28 to level 29 (as required by Google).
At that point, device administrator managed devices that are not manufactured by Samsung will be impacted once the user completes both these actions:
- Updates to Android 10 or later
- Updates the Company Portal app to the version that targets API level 29
Additional impacts based on Android OS version
Android 10: For all device administrator managed devices (including Samsung) running Android 10 and later, Google has restricted the ability for device administrator management agents like Company Portal to access device identifier information. This restriction impacts the following Intune features after a device is updated to Android 10 or later:
- Network access control for VPN will no longer work
- Identifying devices as corporate-owned with an IMEI or serial number won't automatically mark devices as corporate-owned
- The IMEI and serial number will no longer be visible to IT admins in Intune
Android 11 updates after enrolling: These are the changes that will impact device administrator managed devices when they update to Android 11:
- For device administrator devices (excluding Samsung) running Android 11 and later, Google has removed the ability for management agents like Company Portal to enforce blocking Camera, even before the October update to the Company Portal app. Policies blocking camera that are applied to devices before they update to Android 11 will continue to apply.
- With Android 11, trusted root certificates can no longer be deployed to devices enrolled with device administrator (except on Samsung devices). Users must manually install the trusted root certificate on the device. With the trusted root certificate manually installed on a device, you can then use SCEP to provision certificates to the device. In this scenario you must still create and deploy a trusted certificate policy to the device, and link that policy to the SCEP certificate profile.
- If the trusted root certificate is on the device, then the SCEP certificate profile will install successfully.
- If the trusted certificate cannot be found, the SCEP certificate profile will fail.
Android 11 new enrollments: These are the changes that will impact new device administrator enrollments for devices on Android 11:
- Samsung devices configured for Knox Mobile Enrollment will not be able to enroll in device administrator management if they are running Android 11. To enroll these devices, they should either be configured for Android Enterprise management or they can continue to enroll in device administrator management without Knox Mobile Enrollment through the Android Company Portal app. This will not impact devices that are already enrolled and then update to Android 11.
What do I need to do to prepare for this change?
To avoid the reduction in functionality coming in October 2020, we recommend the following:
- New enrollments: Onboard new devices into Android Enterprise management (where available) and/or app protection policies. Avoid onboarding new devices into device administrator management.
- Previously enrolled devices: If a device administrator managed device is running Android 10 or later or may update to Android 10 or later (especially if it is not a Samsung device), move it off of device administrator management to Android Enterprise management and/or app protection policies. You can leverage the streamlined flow to move Android devices from device administrator to work profile management.
- Configure Password Complexity: For impacted devices running Android 10 and later, a future setting called Password Complexity lets you continue enforcing password restrictions and compliance. Password Complexity is a measure of password strength that factors in password type, length, and quality. This setting will be added to the admin console in September, giving you time to configure it for impacted devices. Note: Admins will need to set the Password toggle to "Require". For more information see: New setting for Password complexity for Android 10 and later for device administrator enrolled devic....
What if I have non-Samsung devices that cannot move to Android Enterprise?
Some devices can’t move from device administrator to Android Enterprise management. For example, Google hasn’t made Android Enterprise available in some markets. You can still use Intune to manage non-Samsung devices with device administrator, but the changes to functionality mentioned in this post will apply. For guidance on managing devices when Android Enterprise isn’t available, see: How to use Intune in environments without Google Mobile Services.
Additional information
- Move Android devices from device administrator to work profile management
- Set up enrollment of Android Enterprise work profile devices
- Set up enrollment of Android Enterprise dedicated devices
- Set up enrollment of Android Enterprise fully managed devices
- How to create an assign app protection policies
- How to use Intune in environments without Google Mobile Services
- Understanding app protection policies and work profiles on Android Enterprise devices
- Google’s blog about what you need to know about Device Admin deprecation
- Google's guidance for migration from device administrator to Android Enterprise
- Google's documentation of deprecated device administrator APIs
Blog post updates:
- 8/10/20: Update to clarify the Company Portal app API version under the cause of impact section.
- 8/24/20: We previously communicated that this change will come in the fourth quarter of 2020. Updated post as this change will be made in October 2020.
- 8/27/20: Update to include an additional user experience change for Wi-Fi profiles, additional impacts based on Android OS version, a scenario on what if you have non-Samsung devices that cannot move to Android Enterprise, and a recommendation to configure a new setting called Password Complexity for devices running Android 10 and later.
- 9/8/20: With a small edit to update formatting.
- 9/9/29: Update to the: "Android Additional impacts based on Android OS version/Android 11" section.
- 9/23/20: Added a Note to the "Configure Password Complexity" section as admins will need to set the Password toggle to "Require" to leverage this setting.
- 10/1/20: Updated the "Impacted compliance settings" section.
- 10/6/20: Added a note about using custom Wi-Fi profiles with pre-shared keys.
- 11/6/20: With an update to the "Additional user experience change for Wi-Fi profiles" section.
- 3/2/21: Update to the: "Android Additional impacts based on Android OS version/Android 11" section to include a note around newly enrolled Samsung devices configured for Knox Mobile Enrollment on Android 11.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.