- Home
- Microsoft Intune and Configuration Manager
- Intune Customer Success
- Cross-Account Sharing Improvements in App Protection Policies
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Intune App protection policies (APP) are rules that ensure an organization's data remains safe or contained in a managed app. Today, APP provide organizations with two mechanisms to control how managed accounts handle data transfers:
- Send Org data to other apps
- Receive data from other apps
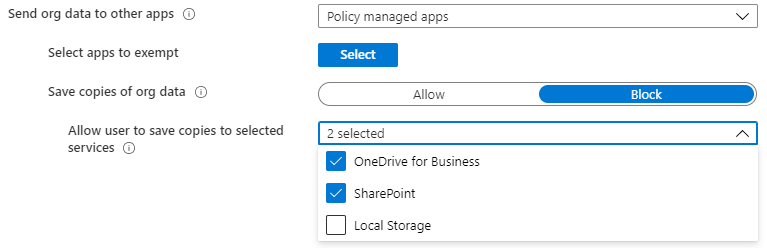
Send Org data to other apps specifies whether the managed account can transfer data to another app. When set to Policy managed apps, to transfer data, the targeted app must also have the managed account logged in and have an APP applied, otherwise, the transfer is blocked. For example, if Jane has an APP assigned and is logged into Outlook and Word, Jane can transfer a Word document from Outlook to Word, but Jane cannot transfer the Word document to her Dropbox app. When Send org data to other apps is set to Policy managed apps, the organization can also control where a managed account can save data, restricting to, if necessary, OneDrive for Business and SharePoint via the Save copies of Org data APP setting.
Figure 1: Send org data to other apps settings
Receive data from other apps specifies whether the managed account can receive data from other apps. When set to Policy managed apps, to receive data, the sending app must also have the managed account logged in and have an APP applied, otherwise, the transfer is blocked. For example, if Jane has an APP assigned and is logged into Word, Jane’s account in Word cannot receive a file transfer from her Dropbox app.
Despite setting the Receive data from other apps to Policy managed apps, multi-identity apps allow users to transfer or share data between accounts within the individual app. For example, within Outlook, Jane can attach a document from her connected personal OneDrive account to an email composed from her work account.
Preventing Cross-Account Sharing
Allowing users to share data within an app due to multi-identity capability is a concern for many security-conscious customers. Many customers enact strict policies on desktop systems that prevent the ability for the user to import data from unmanaged locations, like personal storage repositories. This type of policy is generally implemented to reduce the potential attack vectors for introducing malware into the organization’s systems. Obviously, for these customers, the ability for multi-identity apps to bypass this type of policy is a risk.
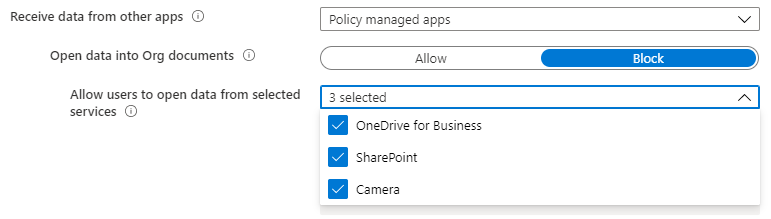
In the second half of 2020, APP is introducing a new policy setting, Open data into Org documents. This setting controls the use of the Open option or other options that enable sharing of data between accounts within apps. Like Save copies of Org data, when Open data into Org documents is set to Block the user cannot open data from any service, except those specified by the organization: OneDrive for Business, SharePoint, and Camera. Open data into Org documents is only enforced when Receive data from other apps is set to Policy managed apps. By default, Open data into Org documents is configured to allow sharing.
Figure 2: Receive data from other apps settings
For organizations that are not concerned with how managed accounts receive data from other apps, no action is necessary, as the existing APP settings and experiences will not change. To take advantage of this functionality when it is released, organizations will need to adjust their App Protection Policies and configure the following settings:
- Set Receive data from other apps to Policy managed apps (if not already configured)
- Set Open data into Org documents to Block
- Set Allow users to open data from selected services to SharePoint, OneDrive for Business, and/or Camera
For apps to support this new functionality, app developers need to integrate the latest Intune SDK and make code changes within their apps. For this reason, the release schedule for supporting this feature within other Microsoft multi-identity apps will vary.
Outlook for iOS and Android
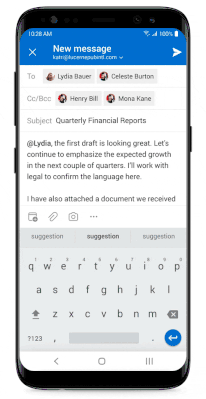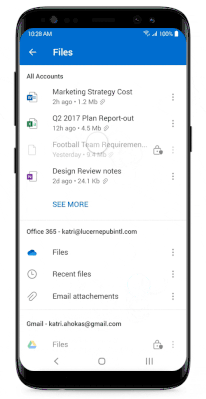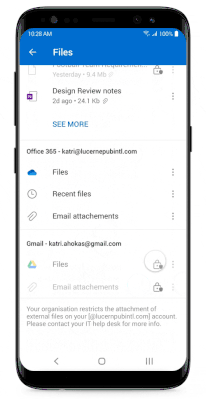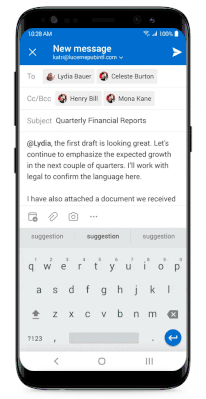
Outlook for iOS and Android is one of the first apps that is taking advantage of this new APP functionality. Outlook will respect the Open data into Org documents functionality around the time that Intune releases the new setting. When composing emails or calendar entries within the managed account, attaching files from restricted locations is prevented, like the camera, if that is defined in the APP:
Figure 3: Camera access is disabled if specified in the APP
Likewise, the file picker blocks attaching content from personal storage services or personal accounts:
Figure 4: File picker blocks attaching content from personal storage services or personal accounts
If composition begins in the personal account and contains an attachment, the user is prevented from changing the account to the managed account:
Figure 5: Changing the from address is blocked when a personal attachment is included in the message body
When previewing personal storage account files, the files cannot be attached to an email message for the managed account:
Figure 6: Cannot insert attachments into the work account when previewing personal files
We hope the data protection improvements with cross-account sharing enable organizations to further reduce attack surface areas. These new settings will be integrated into the App Protection Policy data protection framework enterprise high data protection (level 3) configuration; for more information, see http://aka.ms/appdpf.
As always, if you have any questions, please let us know.
Ross Smith IV
Principal Program Manager
Customer Experience Engineering
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.