- Home
- Microsoft Intune and Configuration Manager
- Intune Customer Success
- Admins Experience: Deploy Hybrid Azure AD-joined devices by using Intune and Windows Autopilot
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Hi everyone, today we have a post by Intune Support Engineer Mingzhe Li. In this post, Mingzhe takes a look at Deploying Hybrid Azure AD-joined devices by using Intune and Windows Autopilot from an Admins perspective. This is a must-read if you’re planning to implement this feature. This is a two part series, see the End-User Experience below:
End-User Experience: Deploy Hybrid Azure AD-joined devices by using Intune and Windows Autopilot
=====
The purpose of this post is to provide an easy, end-to-end guide on setting up hybrid Azure AD joined devices using Windows Autopilot with Microsoft Intune. When working on this topic as a Support Engineer, many customers ask me for a simple tutorial with as many screenshots as possible. Furthermore, my customers would like to know more about the technical workflow of the enrollment process and what log files to investigate. In response to that, I decided to write this article with the hopes that it will help you too and make getting this setup as easy as possible.
This article will describe how to set up the enrollment infrastructure e.g. how to install the Intune Connector for Active Directory, how to set the correct permissions on Active Directory and how to upload devices into the Intune Autopilot Portal etc. The audience of this article will be for IT admins. There is a separate article describing the end-user experience.
Setting up the infrastructure
Before we start with setting up the infrastructure, make sure that we are meeting all the pre-requisites which are described here:
https://docs.microsoft.com/en-us/intune/enrollment/windows-autopilot-hybrid
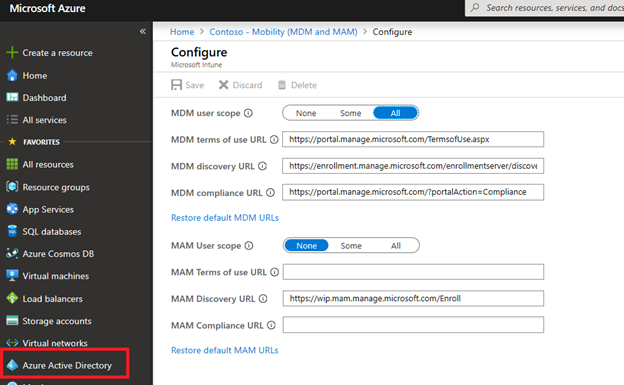
Once you confirmed that your landscape fulfills the pre-requirements according to above article, we need to activate the Auto MDM enrollment in Active Azure Directory.
Activate Auto MDM enrollment
Make sure that Auto-enrollment is activated for those users who are going to enroll their devices.
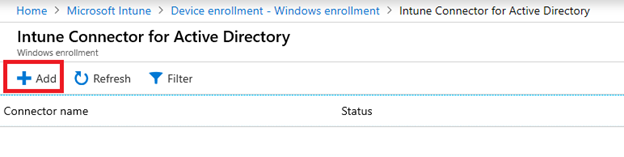
Now, we shall install the Intune Connector for Active Directory. The main responsibility of the connector is to automatically join the device into the on-premise Active Directory domain during the enrollment.
Install Hybrid Autopilot connector
Logon to your Intune portal and navigate to:
Add a new connector, download and install the connector on a Windows 2016 server or higher which is managed by your Active Directory:
Start the installation of the downloaded file ODJConnectorBootstrapper. For troubleshooting the installation, we can check the event viewer logs Windows logs -> Application:
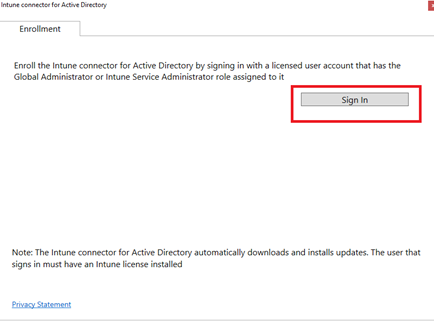
After the installation finished, click on ‘Configure now’ and sign-in with Global Admin account or Intune Admin account. The account also must have a valid Intune license. This will make sure that the connector is properly managed by your Intune tenant.
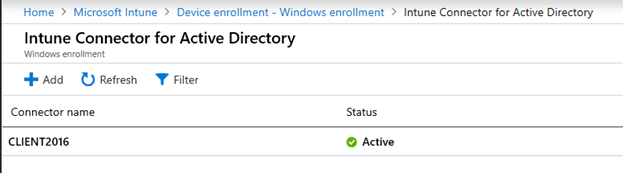
Once the sign-in is completed, the connector should come-up on your Intune portal after a couple of minutes:
If you are unable to sign-in, you can turn off IE Enhanced Security Configuration. If you have a web-proxy, make sure the proxy is bypassed according to https://docs.microsoft.com/en-us/intune/enrollment/autopilot-hybrid-connector-proxy.
Configure your Active Directory
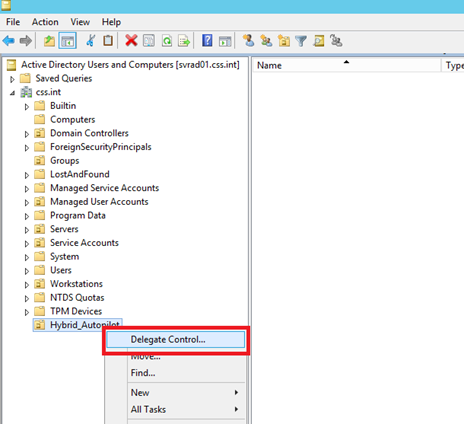
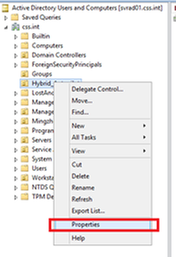
Now, we must make sure that the machine on which the Intune connector is installed, can create computer objects in the Active Directory. Logon to your Domain Controller and run DSA.msc. Create a new OU which includes all hybrid-joined devices using Windows Autopilot and click on ‘delegate control’:
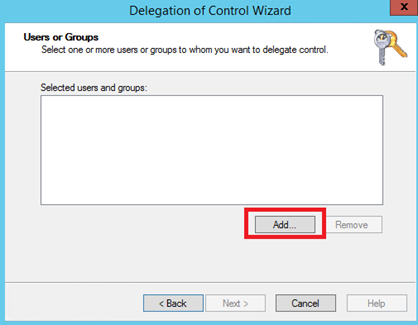
Click on ‘Add’:
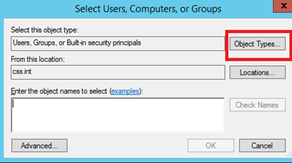
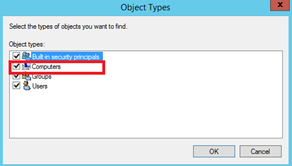
Add Computers to Object Types:
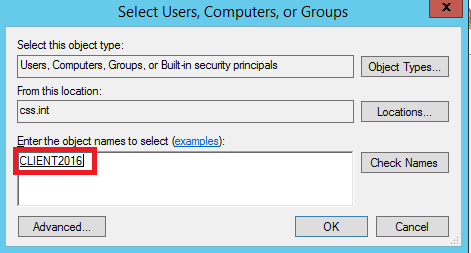
Now enter the name of the Server where the connector is installed:
Follow the instructions and select Create a custom tasks to delegate:
Configure according to below settings:
Finish the configuration.
Create device group on Intune portal
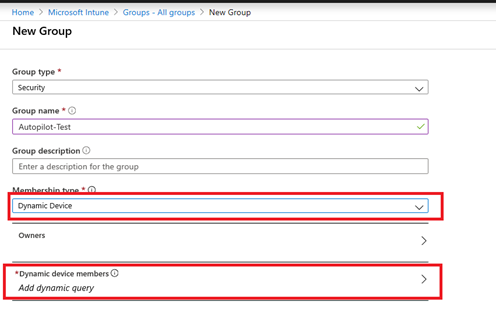
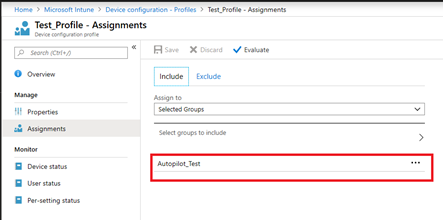
Logon to your Intune portal and create a new dynamic device group (in our example Autopilot_Test) on the Intune portal:
The membership rule should be:
device.devicePhysicalIDs -any _ -contains "[ZTDId]"
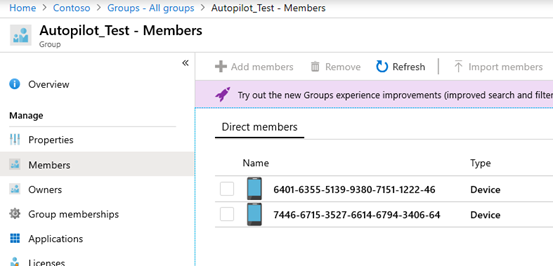
This group will include all devices uploaded into the Intune Autopilot portal so that we can deploy the Autopilot enrollment profile and the domain join profile at a later point in time.
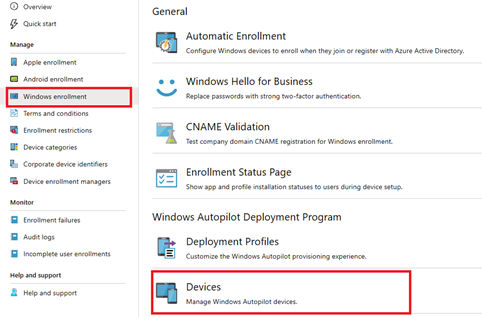
Upload your devices to the Intune Autopilot portal
After we have created the device group, we need to obtain the hardware hash from the device to be enrolled. The hardware hash will usually be provided by the hardware vendor. Alternatively, you can also run below Powershell commands on the device. A csv file will be created and stored into the directory C:\HWID.
md c:\\HWID
Set-Location c:\\HWID
Set-ExecutionPolicy -Scope Process -ExecutionPolicy Unrestricted
Install-Script -Name Get-WindowsAutoPilotInfo
Get-WindowsAutoPilotInfo.ps1 -OutputFile AutoPilotHWID.csv
Import the csv file to the Intune Autopilot portal:
The import can take up to 15 minutes.
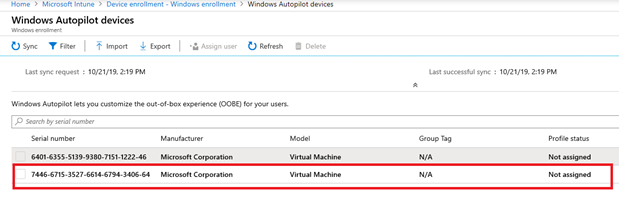
Once the device is successfully synched, a new entry will come up in the portal:
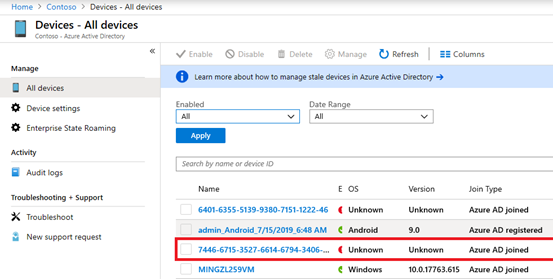
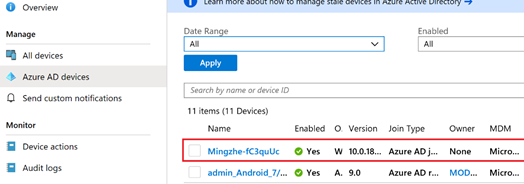
This device entry should also come-up in Azure AD:
The device group we previously created will be populated automatically with the synched devices:
In case the device appears in the Intune Autopilot portal after synching but not in the Azure AD device list, make sure that the same device is not already registered/joined within the current Azure AD tenant or within any other Azure AD tenants.
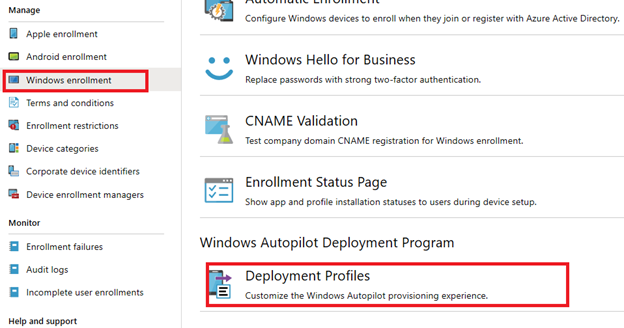
Create Autopilot profile
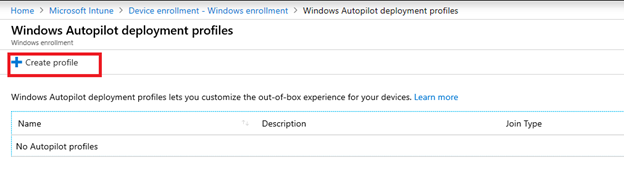
Once we have confirmed that the device group is successfully populated with the synched Autopilot devices, we can start to create the Autopilot enrollment profile:
For example, you can set settings as below:
Deploy the profile to the dynamic device group you created:
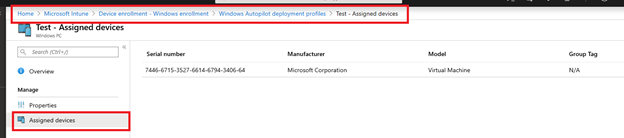
Wait until the device appears under the enrollment profile so that we can confirm that the device is assigned to the profile:
This can take up to 10 minutes.
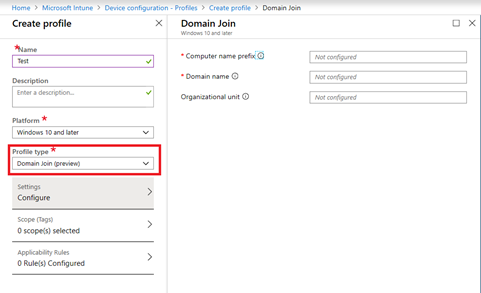
Create domain join profile
Afterwards, we need to create the domain join profile and deploy it to our Autopilot devices. The domain join profile will include parameters such as your domain name and the definition of the OU you created for Autopilot devices. During the enrollment process, the information included in the domain join profile will be exported into a BLOB file and processed by the Intune connector. The Intune connector will add the device into the on-prem Active Directory domain based on the information stored in the BLOB file.
Navigate to:
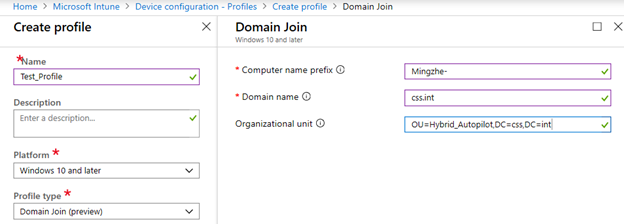
Fill the values with the required information:
Computer name prefix: This parameter defines the prefix for each computer enrolled with Autopilot into Intune. If the prefix is set as Mingzhe-, the device would look as below once enrolled into Intune:
Domain name: Provide the full domain name here.
Organizational unit: This should include the distinguished name of the Autopilot OU. In our example, we previously created the OU Hybrid_Autopilot. We can get the distinguished name of this OU here:
Save the profile and deploy it to your Autopilot device group:
Configure hybrid Azure Active Directory join
As the device will be hybrid Azure Active Directory joined during the enrollment, we need to configure required settings on your Azure AD Connect server. A how-to guide can be found in below links:
If you have a federated environment:
If you have a managed environment:
https://docs.microsoft.com/en-us/azure/active-directory/devices/hybrid-azuread-join-managed-domains
We have now completed all steps to enable the Windows Autopilot process on the target.
Mingzhe Li
Intune Support Engineer
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.