- Home
- Azure
- Azure Integration Services Blog
- Secure Logic App HTTP endpoint with Azure AD integration
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Overview:
We have several ways to secure the Logic App endpoints like restricting inbound IP addresses, using SAS keys and API management instance. API management allows us to secure endpoints with various authentication modes such as client certificates, Oauth and basic credentials authentication.
We can also authorize Logic App HTTP endpoints using Oauth token with the new feature in Logic App "Authorization".You can follow the steps below for implementing this.
Implementation:
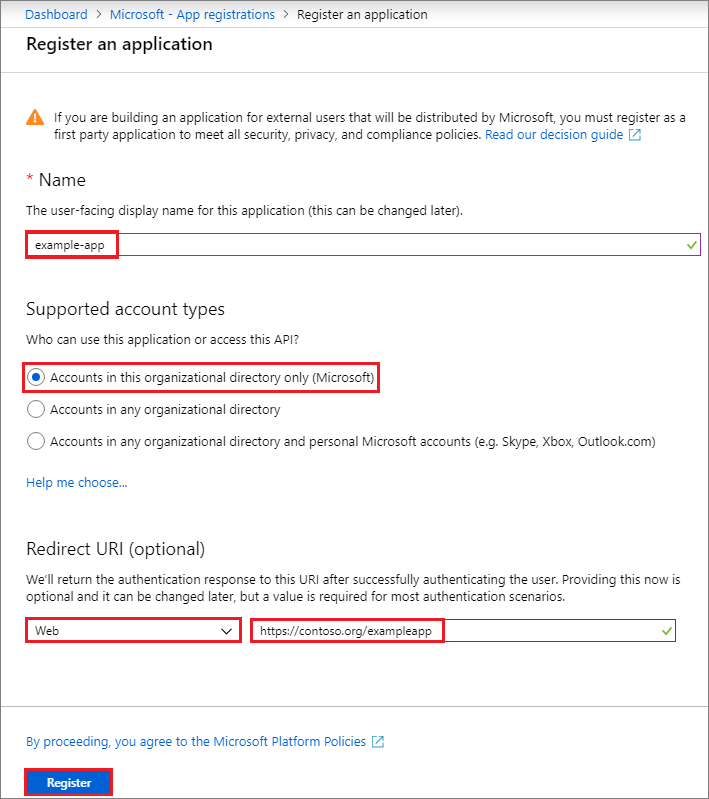
- We have to create an App Registration (Service Principal) in Azure Active Directory . Go to Azure AD and Click on App registrations to add new registration.
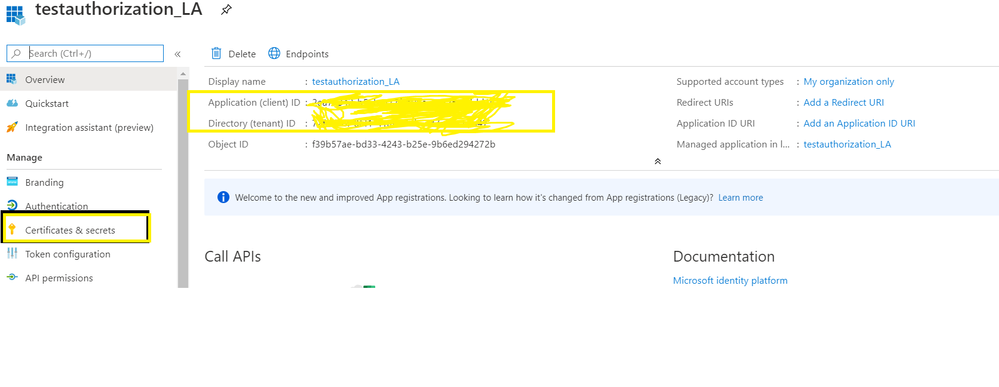
- Open created App registration, Select certificates and secrets and add new secret. Copy the client secret value as it won't be visible later on.
- Collect App registration details from overview page i.e. Client Id, Tenant Id. Which we will be using later to generate Oauth token to access Logic App endpoint.
- Now, we can configure any existing or new Logic App which has HTTP trigger endpoint to authenticate with OAuth tokens.
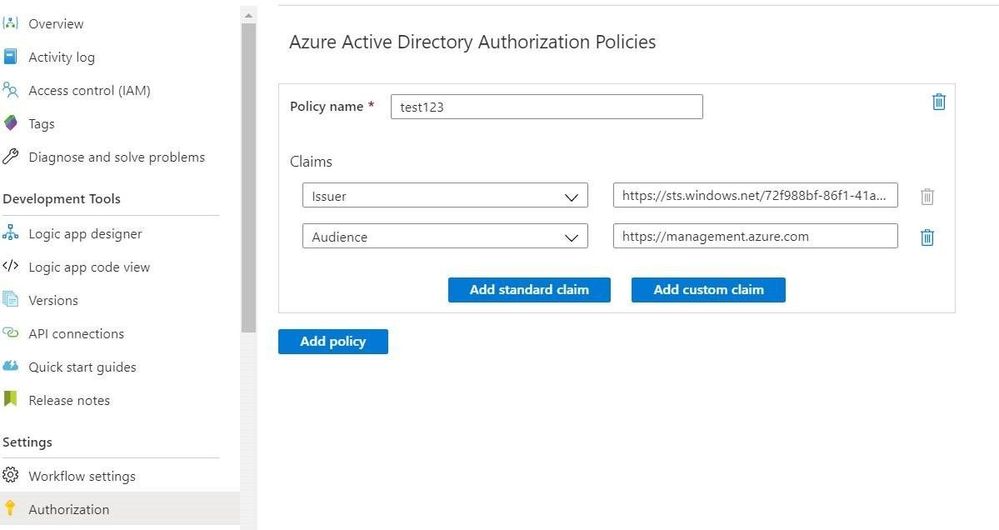
- Go to Logic App --> Authorization and add new Policy and claims to authenticate with Oauth tokens as in screenshot below.
Issuer: https://sts.windows.net/{{TenantId}}/
Audience: https://management.azure.com
- Now, Logic App endpoint supports with Oauth authentication. Now ,generate the Oauth token using App registration details and trigger Logic App with the Oauth token.
REST API to generate OAuth tokens:
URL: https://login.microsoftonline.com/{{tenantId}}/oauth2/token
Verb: POST
Parameters:
Client_Secret: client secret collected in App registration
grant_type: client_credentials
client_id : Application Id of App registration
resource: https://management.azure.com
Trigger LogicApp HTTP endpoint with OAuth token:
- Go to LogicApp and get the HTTP endpoint URL and remove SAS key from URL.
Example: https://prod-17.centralindia.logic.azure.com:443/workflows/d04bc34e3fdd403091de956ed28c48cd/triggers...&sig=Bq9fGp3wZ0Q7mDTdozBtvlljpXBIrGevi394_19RuHY
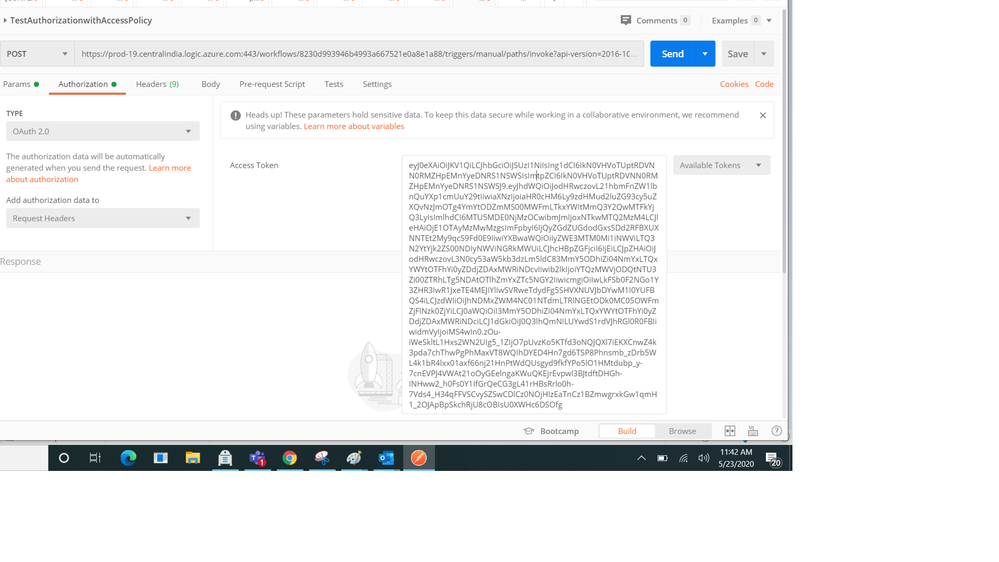
- Now we can call the endpoint above with OAuth token (Bearer key ) collected above as in screenshot below.
References:
https://docs.microsoft.com/en-us/azure/logic-apps/logic-apps-securing-a-logic-app#secure-triggers
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.