- Home
- Azure
- Azure Integration Services Blog
- Azure Logic Apps - Authenticate with managed identity for Azure AD OAuth-based connectors
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
When you enable and use a managed identity (formerly Managed Service Identity or MSI) for authentication, your logic apps can more easily access Azure resources that are protected by Azure Active Directory (Azure AD). A managed identity removes the need for you to manage credentials or Azure AD tokens by providing Azure services with an identity that is managed by Azure AD.
Azure Logic Apps currently supports both system-assigned and single user-assigned managed identities for specific built-in triggers and actions such as HTTP, Azure Functions, Azure API Management, Azure App Services, and so on. This blog post announces preview support for using your logic app's managed identity to authenticate to Azure AD OAuth-based managed connector triggers and actions.
Below is the list of connectors supporting managed identity authentication in preview with more support coming for other connectors in the future:
|
Connector |
Connector API name |
|
Azure Container Instance |
aci |
|
Azure Resource Manager |
arm |
|
Azure Automation |
azureautomation |
|
Azure Data Factory |
azuredatafactory |
|
Azure Data Lake |
azuredatalake |
|
Azure Key Vault |
keyvault |
|
Azure Event Grid |
azureeventgrid |
|
Azure Sentinel |
azuresentinel |
|
Azure Data Explorer (Preview) |
kusto |
|
Azure AD Identity Protection (Preview) |
azureadip |
|
Azure IoT Central V3 (Preview) |
azureiotcentral |
|
HTTP with Azure AD |
webcontents |
Prerequisites
- An Azure account and subscription. If you do not have a subscription, sign up for a free Azure account. Both the managed identity and the target Azure resource where you need access must use the same Azure subscription.
- To give managed identity access to an Azure resource, you need to add a role to the target resource for that identity. To add roles, you need Azure AD administrator permissions that can assign roles to identities in the corresponding Azure AD tenant.
Configure managed identity authentication on supported connectors
- In the Azure portal, you can either use an existing logic app that has enabled the user-assigned or system-assigned managed identity, or you can create a new logic app and then enable the system-assigned or user-assigned managed identity on your app. The example in this blog post uses a logic app's system-assigned managed identity. You can set up your logic app with either the system-assigned identity or a single user-assigned identity, but not both. A group of logic apps can share a user-assigned identity because they're not bound to a single Azure resource, while the system-assigned identity strictly belongs to a single Azure resource and can't be shared.
- On the target Azure resource where you want the managed identity to have access, give that identity role-based access to the target resource. This role lets your logic app authenticate access to the target resource at runtime by using the managed identity’s Azure AD tokens.
- In the Azure portal, open your logic app in the Logic App Designer. Add a trigger or action from a connector that supports managed identity authentication and then select an operation.
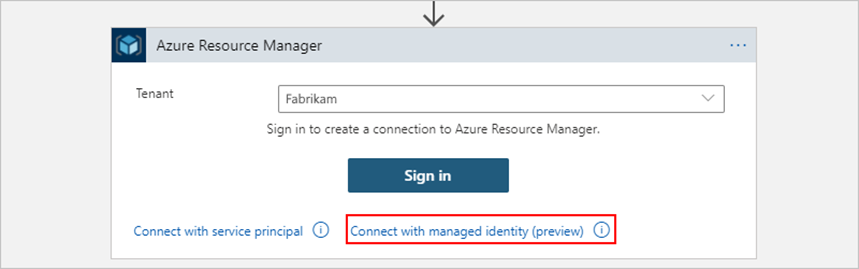
The above example in this post sets up the Azure Resource Manager action, named Read a resource, to use the logic app's system-assigned managed identity for authentication and read the specified Azure resource. - Create a new connection by selecting Connect with managed identity (preview).
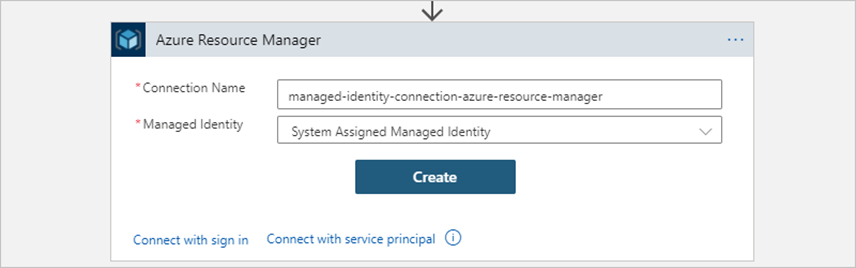
The action now shows the managed identity drop-down list, which includes the managed identity type that's currently enabled on the logic app.
If the managed identity isn't enabled, the following error appears when you try to create the connection.
After successfully creating the connection, the designer can fetch any dynamic values, content, or schema by using managed identity authentication. - Provide the required input for the action that you selected. The connection name appears at the bottom of the action shape.
- Add any other actions that your logic app requires to run. When you're done, save the workflow.
- To test your logic app, on the designer toolbar, select Run.
How does a connection with a managed identity work at runtime?
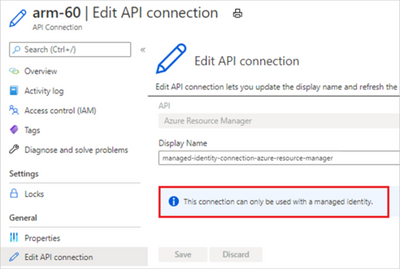
Connections that you created to use a managed identity are a special connection type that you can use only with a managed identity.
At runtime, the connection uses the managed identity that’s enabled on the logic app. This configuration is saved in the logic app definition’s parameters object, which contains the $connections property object that includes pointers to the connection’s resource ID, the api’s resource ID and connectionProperties. The authentication property in connectionProperties contains user-assigned identity’s resource id if a user-assigned identity is associated with the logic app. No additional input is required in authentication property object other than type, if a system-assigned identity is associated with the logic app.
During runtime, the Logic Apps service checks whether any managed connector trigger and actions in the logic app are configured to use the managed identity and that all the required permissions are set up to use the managed identity for accessing the target resources that are specified by the trigger and actions. If successful, the Logic Apps service retrieves the Azure AD token that’s associated with the managed identity and uses that token to authenticate to the target resource and perform the configured operation in trigger and actions.
Next steps
We’d like your feedback! Please try the managed identity support managed connections that support Azure AD OAuth and let us know what you think. Stay tuned for managed identity support in more connectors such as SQL Server, Office, Power platform, and other Azure connectors.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.