- Home
- Microsoft IIS
- IIS Support Blog
- Remove Unwanted HTTP Response Headers
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
The purpose of this blog post is to discuss how to remove unwanted HTTP response headers from the response. Typically we have 3 response headers which many people want to remove for security reasons.
- Server Header - Specifies web server version.
- X-Powered-By - Indicates that the website is "powered by ASP.NET."
- X-AspNet-Version - Specifies the version of ASP.NET used.
Before you go any further, you should evaluate whether or not you need to remove these headers. If you would like to go ahead and remove the headers then follow the following options.
Server Header
There are three ways to remove the Server header from the response. The best one is to use the third option.
1. Using the Registry key.
Create a DWORD entry called DisableServerHeader in the following Registry key and set the value to 1.
HKLM\SYSTEM\CurrentControlSet\Services\HTTP\Parameters
After adding the Registry key, restart the HTTP service using the net stop http command and the net start http command. If the HTTP service doesn’t start up then use the iisreset command. If that also doesn’t work then you can restart the server. Please note that this method is used only when the Server header comes as “Microsoft-HTTPAPI/2.0”. When the request comes to IIS, it first goes to http.sys driver. HTTP.SYS driver either handles the request on its own or sends it to User mode for further processing. When the request goes to User mode that’s the time it returns the server header as “Microsoft-IIS/7.5.”. However when the request returns from the HTTP.SYS driver then the server header comes as “Microsoft-HTTPAPI/2.0”. By placing the above registry key it will remove this specific header. If you would like to remove the Server header as “Microsoft-IIS/7.5.”, then follow the following methods.
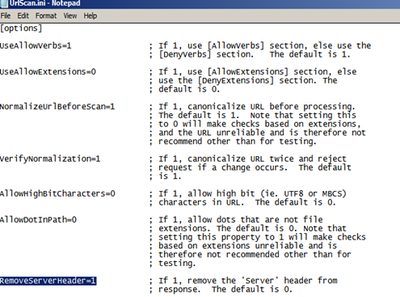
2. Using the URLScan tool.
Install the URLScan on your machine. Please follow the following link for that
http://www.iis.net/downloads/microsoft/urlscan
After installing URLScan, open the URLScan.ini file typically located in the %WINDIR%\System32\Inetsrv\URLscan folder. After opening it, search for the key RemoveServerHeader . By default it is set to 0, but to remove the Server header, change the value to 1. Doing so will remove the Server header Server: Microsoft-IIS/7.5 from the User mode response.
Please note that changes made by URLScan at the global level apply to all of your sites. If you would like to setup this for a particular site then look at the following article (site filter section)
http://www.iis.net/learn/extensions/working-with-urlscan/urlscan-setup
3. Using URLRewrite
If you don’t want to go with URLScan, you can use the URLRewrite module to remove the value of the Server header. Please note that it will not remove the header altogether but it will remove the value of it.
Step 1. Install URLRewrite. To install the URLRewrite please go to the following link
http://www.iis.net/downloads/microsoft/url-rewrite
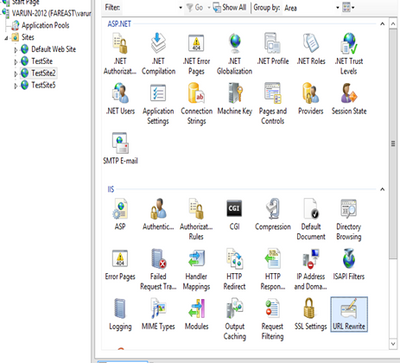
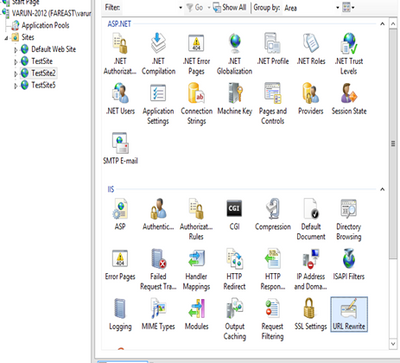
Step 2. Open the site on which you would like to remove the Server header and click on the URLRewrite section.
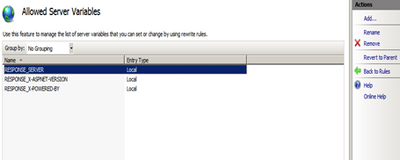
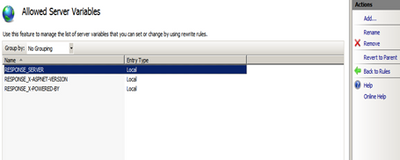
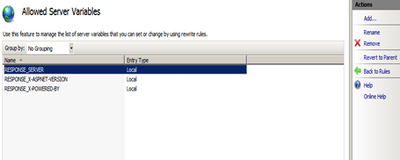
Step 3. Click on the “View Server Variables” in the Actions pane in the right-hand side.
Step 4. Click on the Add button and then enter “RESPONSE_SERVER” in the textbox provided.
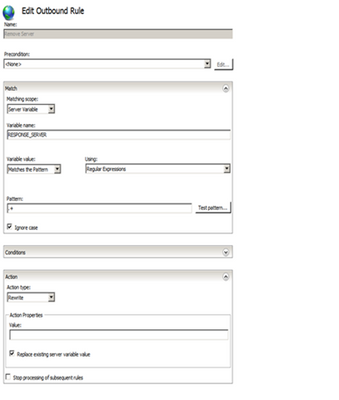
Step 5. Now we need to create an outbound rule. To know how to create an outbound rule, look at the following link
Step 6. Create an Outbound rule as the following.
Please note that this is a website-specific rule. If you want to create the rule for all of your applications, create the rule at the server level. Also, some applications, especially third-party applications, may require the Server header, so you may need to remove this rule for those applications.
X-Powered-By
There are two ways to remove this header as well. The second method would be the preferred one.
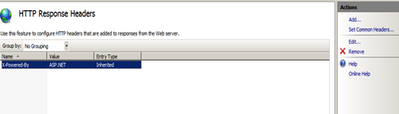
1. Using IIS HTTP Response headers.
Open the site which you would like to open and then click on the HTTP Response Headers option.
Click on the X-Powered-By header and then click Remove on the Actions Pane to remove it from the response.
2. Using URLRewite Rule.
Please note that it will not remove the header altogether but it will remove the value of it.
Step 1. Install URLRewrite. To install the URLRewrite please go to the following link
http://www.iis.net/downloads/microsoft/url-rewrite
Step 2. Open the site on which you would like to remove the X-Powered-By header and Click on the URLRewrite section.
Step 3. Click on the “View Server Variables” in the Actions pane in the right-hand side.
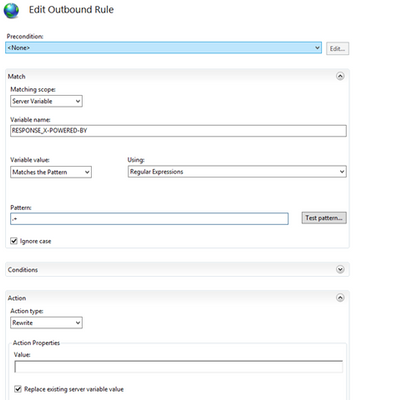
Step 4. Click on the Add button and then enter “RESPONSE_X-POWERED-BY” in the textbox provided.
Step 5. Now we need to create an outbound rule. To know how to create an outbound rule, look at the following link
Step 6. Create an Outbound rule as the following
Please note that this is a website-specific rule. If you want to create the rule for all of your applications, create the rule at the server level. Also, some applications, especially third-party applications, may require the x-powered-by header, so you may need to remove this rule for those applications.
X-AspNet-Version
There are two ways to remove this header as well. The preferred one is the first one.
1. Using the httpRuntime element.
Add the following line in your web.config in the <system. Web> section
<httpRuntime enableVersionHeader="false" />
2. Using an URLRewite rule.
Please note that it will not remove the header altogether but it will remove the value of it.
Step 1. Install URLRewrite. To install the URLRewrite please go to the following link
http://www.iis.net/downloads/microsoft/url-rewrite
Step 2. Open the site on which you would like to remove the Server header and go to the URLRewrite section.
Step 3. Click on the “View Server Variables” in the Actions pane in the right-hand side.
Step 5. Now we need to create an outbound rule. To know how to create an outbound rule, look at the following link
Step 6. Create an Outbound rule as the following.
Please note that this is a website-specific rule. If you want to create the rule for all of your applications, create the rule at the server level. Also, some applications, especially third-party applications, may require the x-aspnet-version header, so you may need to remove this rule for those applications.
Author: Mathur Varun (MSFT)
Tech Reviewed by: Enamul Khaleque (MSFT)
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.