Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Home
- Microsoft IIS
- IIS Support Blog
- Host Header Vulnerability
Host Header Vulnerability
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
By
Published
Nov 25 2019 11:31 AM
63K
Views
Nov 25 2019
11:31 AM
Nov 25 2019
11:31 AM
Browsers send Host Header to inform about the URL client wants to visit. Attackers can temper Host Header to manipulate how the application works. Here is how this attack occurs:
- Attacker makes a request with edited Host Header (Example: malicious-site.com)
- Web server receives this Host Header (malicious-site.com)
- If the application is using this Host Header in a link, the malicious site will be displayed. For example, the application may be calling a JS file with Host Header string. In this case, the website will call an address like the one below which points to attacker’s site:
<script src="http://malicious-site.com/script.js">
This type of attack can affect password reset forms and X-Forwarded-Host header as well.
Solution
Security scan tools may flag Host Header related findings as a vulnerability. Here are the best practices for preventing attackers using Host Header:
- Do not use Host Header in the code
- If you have to use it, validate it in every page
- Use hostnames in all IIS websites
- Disable support for X-Forwarded-Host
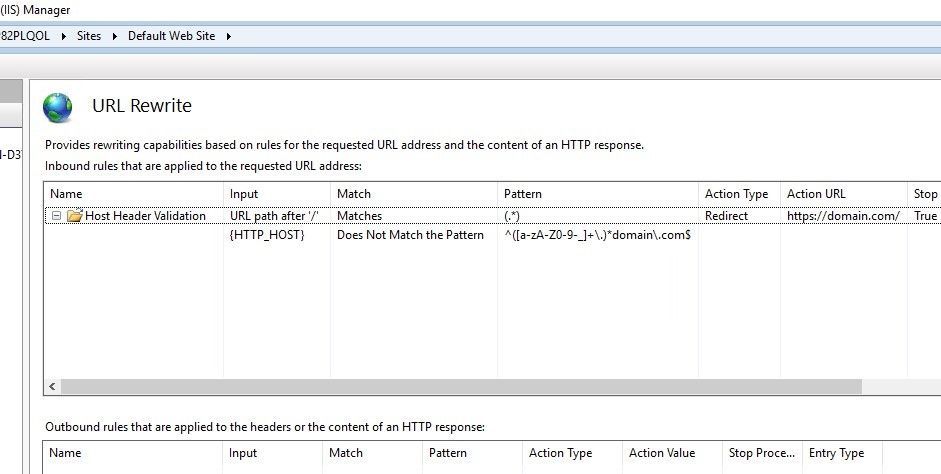
URL Rewrite rules can be used to find malicious host headers:
- Click on the site in IIS Manager
- Go to “URL Rewrite” (it should be installed first)
- Click “Add Rule(s)”
- Select “Blank rule”
- For “Match URL” section, enter (.) into the “Pattern”
- In “Conditions” section, click “Add”
- Enter {HTTP_HOST} into “Condition input”
- Select “Does Not Match the Pattern” from “Check if input string” list
- Enter ^([a-zA-Z0-9-_]+.)*domain.com$ into “Pattern” field (change domain name with yours)
- For the “Action” section, select “Redirect” from the “Action type” list
- Enter your domain address (https://domain.com/) in the “Redirect URL”
- Select “Permanent (301)” from the “Redirect type” list
- Click “Apply”
12 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.