- Home
- Microsoft IIS
- IIS Support Blog
- Centralized Certificate Store (CCS) and IIS bindings
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
After IIS8, CCS (Centralized Certificate Store) feature can be used to pick up website certificates from a network share. It makes certificate management a lot easier from a single store instead of managing them in every server’s local certificate stores.
There are two steps to start using CCS:
- Configure IIS to use CCS
- Add an IIS binding to your website (You can use IIS Manager or PowerShell)
Configure IIS to use CCS
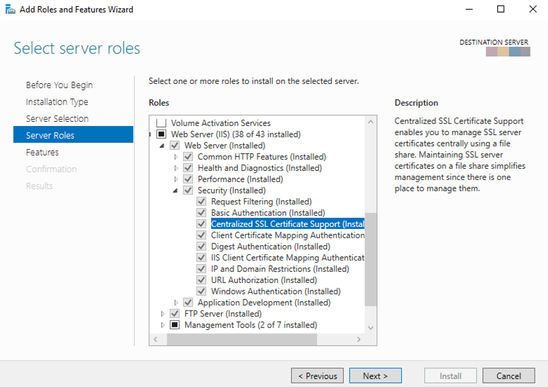
Install CCS feature via Server Manager:
After the installation:
- Open IIS Manager. Click the server name
- Double click on “Centralized Certificates“
- Click “Edit Feature Settings”
- Fill out the settings:
- Physical path (most commonly a network share)
- Username and password to access to this path
- Certificates private key password (if required)
After clicking “OK”, IIS reads the certificates from the path and populates the information about the certificates.
IIS determines which certificate is associated with which website by using the naming convention (<subject name of a certificate>.pfx:(
- If the subject name is www.contoso.com, IIS looks for
www.contoso.com.pfx - If there is no match, it looks for a wildcard certificate with this name:
_.contoso.com.pfx - If there are Subject Alternative Names (SANs), the file names should be
www.contoso1.com.pfxandwww.contoso2.com.pfx
IIS stores the CCS configuration in registry: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\IIS\CentralCertProvider
Add an IIS binding
Add an IIS binding by using IIS Manager
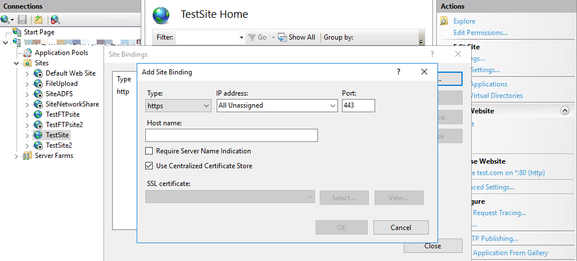
- Go to IIS Manager. Select the website
- Click “Bindings…”. Click “Add“
- Select “https” as the “Type”
- Check “Use Centralized Certificate Store“
Add an IIS binding by using PowerShell
Run the commands below.
New-WebBinding -Name "Default Web Site" -sslFlags 3 -Protocol https -IP * -Port 443 -HostHeader ("localhost")
New-Item -Path "IIS:\SslBindings\!443!localhost" -sslFlags 3
The meanings of the sslFlags parameter:
|
sslFlags |
Description |
Use CCS |
Use SNI |
|
0 |
SSL binding does not use SNI |
0 |
0 |
|
1 |
SSL binding uses SNI |
0 |
1 |
|
2 |
SSL binding does not use SNI, but uses Central Certificate Store (The hostname for certificate lookup is determined based on the binding information in Applicationhost.config) |
1 |
0 |
|
3 |
SSL binding uses both SNI and Central Certificate Store |
1 |
1 |
IIS stores the binding information in Registry: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\HTTP\Parameters\SslBindingInfo
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.