- Home
- Microsoft 365
- Identity & Authentication
- Re: Configuring iOS 12 for O365 Exchange using MFA (OAuth)
Configuring iOS 12 for O365 Exchange using MFA (OAuth)
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 10 2018 01:41 PM
I have iOS 12 beta 6 installed, and Im using Apple Configurator 2.8 to generate a ActiveSync payload that contains the new OAuth 2.0 settings.
The deployment and setup of the Exchange/ActiveSync profile is smooth and easy in iOS 12 as expected.
The final end-user step is the GUI prompt to enter a MFA code (via SMS or the MS Authenticator app). Pretty much performs as expected too (other than a couple extra taps and 'hops' to the MS cloud).
The problem I am experiencing is that Mail/Contacts/Calendar stop syncing after a couple hours of deployment. At this time, I see a generic "Failed to connect to server" error.
There is no way to force a new session/token. No way to re-authenticate again (i.e.; no password field). All ActiveSync-based services stop working until the MDM profile is removed and re-deployed again.
Rinse & repeat.
I'm deploying the Apple .mobileconfig (XML) profile to my test iOS 12 devices via USB (Apple Configurator) and via Meraki MDM. Both yield the same results.
The problem is not related to deployment. The problem clearly appears to be a session time-out or a token refresh failure.
MFA (multi-factor authentication) works great on our Macs and Windows PCs (including Outlook 2016, Skype for Business, Outlook Webmail, etc). Both SMS and the Microsoft Authenticator app work fine for one-time passcodes too.
No App Passwords are used in my environment (other than the initial App Password generated automatically by MS when an O365 account transitions from 'Enabled' to 'Enforced'.
I have been able to reproduce this issue on multiple iOS devices running iOS 12 betas #5 and #6.
I have rebuilt the MDM .mobileconfig profile numerous times (including creating it by hand in a text editor). Profile and payloads look perfect.
I am digging into O365 server/tenant logs now, but I don't see anything interesting yet.
Has anyone else experienced this issue? Any help or feedback is greatly appreciated.
- Labels:
-
Authentication
-
Exchange
-
Mobile
-
Office 365
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 24 2018 02:49 PM
Office 365 MDM through the Intune Company Portal app also seems to not be working for deploying MFA accounts. I was under the impression that this capability would be added with iOS 12, but the behavior seems to be the same as iOS 11 (no way to authenticate with MFA in the Intune Company Portal deployment process). Has anyone gotten this to work since iOS 12 was released? We use both MFA and Office 365 MDM, and so far the two do not seem to get along.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 29 2018 01:55 PM
We use O365 MDM with MFA and it works but it requires the user to create an App Password for the native iOS Mail app.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 25 2019 12:22 AM - edited Feb 25 2019 12:23 AM
Just wondered if you ever managed to get O365 MDM email profiles working for an MFA-enabled account using the Intune Company Portal app on iOS 12 (without using App passwords)? It seems to still not work.
When my user is on an MFA Trusted Network (so that MFA isn't required), authentication works just fine. As soon as the user is outside the Trusted Network where MFA is required, continuous password prompts are received and the iOS 12 Mail.app cannot authenticate.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 18 2019 04:00 PM
@Steven Jenkinson I don't see this as working either. I see that they have added OAuth support for Intune that Office 365 MDM is built on, but it doesn't seem to be enabled for Office 365 MDM? Is anyone from Microsoft monitoring this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 17 2019 12:12 AM
@Dan StranathanHave you fond anything about this?
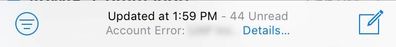
I have a similar issue and I am deploying on IOS12.2+ with Native Mail App and MFA. Deployment and first registration are working well but after a couple of hours mail stop syncing and I have an "Account error" message:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 29 2019 11:34 AM
@StephanBrisson so far I have had mixed results on IOS12 devices. On one of the first devices the native mail asked for a password. I created an App password. Would not accept it. So I found an article online which suggested just deleting that account and adding it back, leaving whatever contacts and notes were already on the device. That took care of it. On my iPhone I just entered the app password. But then on my iPad that would not work, so I just removed the account and added it back.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 29 2019 12:45 PM
@Jim Hill It's supposed to work with Modern Authentication/OAuth, without the need to use an app password. Needing an app password for email on a phone for all users that are on MFA is absurd in 2019. It's supposed to be best practice to turn on MFA for all users these days, but Office 365 MDM doesn't support it? I'm astounded this hasn't gotten more attention.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jun 04 2019 03:55 PM
We are also having the exact same issue, since around iOS 12.2
We've extracted logs from a device and they talk about oAuth tokens failing to refresh.
Raised support ticket with Microsoft but they havent been able to assist.
Have you had any progress or luck with your issue?
Error>: DAEASOAuthTokenRefreshResponse response is not NSHTTPURLResponse. Game over
<Notice>: Received a Transient Network Error: refrehing OAuth Token failed with Error Error Domain=NSURLErrorDomain Code=-1002 "unsupported URL" UserInfo={NSLocalizedDescription=unsupported URL, NSUnderlyingError=0x102bc0ce0 {Error Domain=kCFErrorDomainCFNetwork Code=-1002}}
May 13 11:45:26 iPhone accountsd(DAAccountAuthenticator)[1296] <Error>: Authenticator FAILED Trying To Refresh OAuth2 credentials for account <private> Networking Error
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jun 04 2019 04:58 PM
@webber1979Yes we were able to make it work properly. We are using Airwatch (VMware Workspace One) and we had to change our email profiles deployment parameters. We had to add the OAuth parameter to the email profile but then the user name in the profile was the following: domain\user@domain. It was working in the initial logon (for about an hour) but when the refresh token was expiring the profile was unable to match the user name with anything.
We had to delete the username and the domain from the Email profile (pushed by Airwatch) and then it worked fine.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jun 04 2019 10:44 PM
Thanks for the reply.
Think your issue might be different to ours, we already have oAuth turned on and we use UPN as the username. I've changed this to primarysmtpaddress and hope this may help.
I've also tried removing their activesync device partnership prior to the migration to see if this helps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 21 2022 06:46 AM
Does anyone have any updated advice for using Office 365 MDM to push iOS management profiles, now that EAS is disabled? It still seems to be pushing EAS profiles to my iOS devices. Has anyone been able to get Office 365 MDM to use Modern Auth?