- Home
- Microsoft 365
- Microsoft 365
- Strategies to Configure and Monitor Controlled Folder Access to Protect Against Ransomwares
Strategies to Configure and Monitor Controlled Folder Access to Protect Against Ransomwares
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 23 2020 06:49 AM - edited Apr 23 2020 06:52 AM
One of concerns for IT Professionals is to make sure their PC won’t be infected with ransomwares. Windows Defender has a great feature called Controlled Folder Access which provides greater protection against ransomwares. However, it is important to make sure it won’t be against production. Sometimes, when you enable this policy, then it might block legitimate changes by trusted programs. Therefore, it is important to work on proper planning to make sure it provides protection while it won’t harm production. You could manage Controlled Folder Access using Group Policy and you could navigate to Computer Configuration > Administrative Templates > Windows Components > Windows Defender Antivirus > Windows Defender Exploit Guard > Controlled Folder Access and there you could set policies to manage Controlled Folder Access. You will have three configurations here:
Configure allowed applications: In case, if there is a change made by trusted program and it has been blocked by Controlled Folder Access, then you could create whitelist and add those applications here. Make sure they are trusted application and test application before add it to allowed list.
Configure Controlled folder access: This is important configuration where you could enable this and you will have multiple modes. It is recommended to enable it in testing environment with your applications to see if there is any incorrect detection (to discover if you need to add any application to allowed list) and then enable audit mode for group of users and once you make sure your policy is working as expected, then deploy policy to enable it and keep monitoring and testing and deploy it in larger groups.
Configure protected folders: By default, when this setting is enabled it will protect Windows folders including Documents, Pictures, Videos, Music and Favorites. However, if you want to protect additional folder like folders which are being used for company’s project or any other sensitive folders, then it is place where you could define it.
Now let’s go back to deployment strategy, first try to setup a testing PCs and simulate your environment and use all applications which you are using in your company on these testing PCs and see if there is any application which you will need to add in allowed list. Make sure add all folders that you are using in Configure protected folders. Then you will need to setup Configure Controlled folder access and you will see the following.
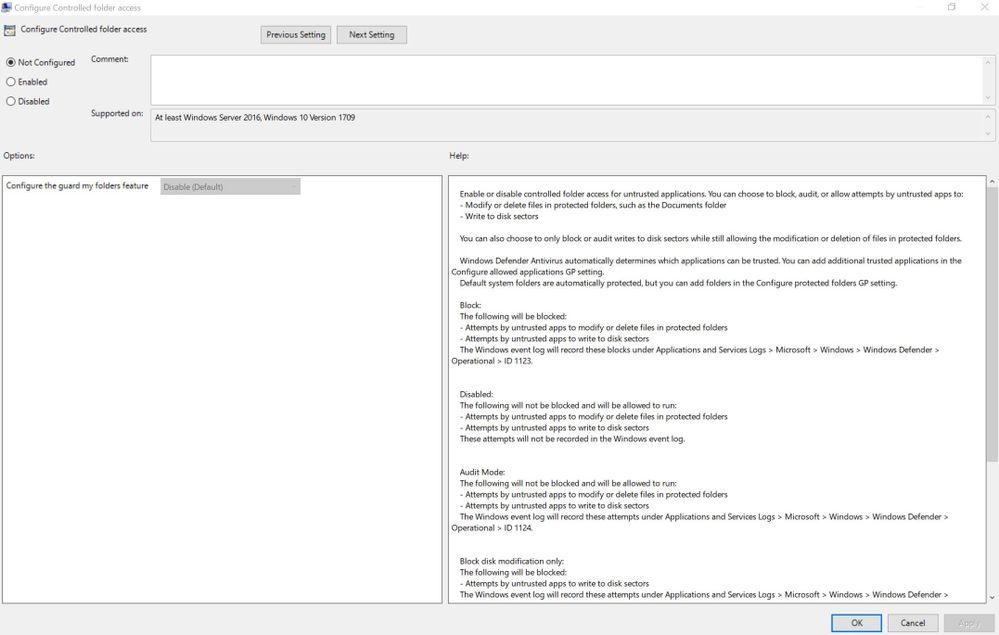
It is recommended to first set it to Audit disk modification only and monitor users and look for any incorrect blocking, then enable Audit Mode and do monitoring and observe if there are any additional unwanted changes. One you have list of incorrect detection which you might need to add them to trusted app and you believe you have most of applications under your list, then configure Block disk modification only and in this case, it is not only about auditing but it will start blocking unauthorized changes and you will need to observe in this mode and if everything was okay, then set Block and you have protection. You should do this with small group of people in different division in company and then expand it to everyone. Take a note that if company is making change to software or installing new programs, you might need to investigate and switch to audit mode again. Note that all log files including the one for auditing will be placed on Applications and Services Logs > Microsoft > Windows > Windows Defender > Operational in the Event Viewer and you should look for event IDs 1123 and 1124. These settings are proactive measurements against 0-days ransomwares. Please take a note that enabling Controlled Folder Access is NOT replacement for other protection strategies like deploying Windows Update ¸ Anti-Malware signature, SmartScreen filer, Anti-Spam Policy, Backup, etc. However, it could be considered as additional defense layer against ransomwares.