- Home
- Healthcare and Life Sciences
- Healthcare and Life Sciences Blog
- Microsoft Purview - Paint By Numbers Series (Part 3c) - Data Loss Prevention with Teams Chat
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Before we start, please not that if you want to see a table of contents for all the sections of this blog and their various Purview topics, you can locate the in the following link:
Microsoft Purview- Paint By Numbers Series (Part 0) - Overview - Microsoft Tech Community
Disclaimer
This document is not meant to replace any official documentation, including those found at docs.microsoft.com. Those documents are continually updated and maintained by Microsoft Corporation. If there is a discrepancy between this document and what you find in the Compliance User Interface (UI) or inside of a reference in docs.microsoft.com, you should always defer to that official documentation and contact your Microsoft Account team as needed. Links to the docs.microsoft.com data will be referenced both in the document steps as well as in the appendix.
All of the following steps should be done with test data, and where possible, testing should be performed in a test environment. Testing should never be performed against production data.
Target Audience
The Data Loss Protection (DLP) section of this blog series is aimed at Security and Compliance officers who need to prevent data from being sent via Teams chats to untrusted users.
Document Scope
This document is meant to guide an administrator who is “net new” to Microsoft E5 Compliance through the configuration of Teams Data Protection Loss (DLP).
It is presumed that you already have a Sensitive Information Type that you want to use in your DLP policy. For the purposes of this policy, I will use the data from the Exact Data Match I created in part 1a of this blog series.
This document will only be dealing with SIT data being shared through the Teams Chat. It will not be dealing with Files being shared either through Teams Chat or shared Teams sites. That will be covered in a future blog entry.
Out-of-Scope
This document does not cover any other aspect of Microsoft E5 Compliance, including:
- Sensitive Information Types
- Exact Data Matches
- Microsoft Cloud App Security (MCAS)
- Records Management (retention and disposal)
- Data Protection Loss (DLP) for Exchange and Endpoint
- Information Protection
- Information Governance
- Advanced eDiscovery
It is presumed that you have a pre-existing of understanding of what Microsoft E5 Compliance does and how to navigate the User Interface (UI).
It is also presumed you are using an existing Information Types (SIT) or a SIT you have created for your testing.
This file will not be covering the sharing of files through Teams or through Teams chat.
If you wish to set up and test any of the other aspects of Microsoft E5 Compliance, please refer to Part 1 of this blog series (listed in the link below) for the latest entries to this blog. That webpage will be updated with any new walk throughs or Compliance relevant information, as time allows.
Overview of Document
- Choose which Sensitive Information Types (or SIT) you wish to use.
- Create a Teams DLP policy
- Test your Teams DLP policy against a Teams chat with two internal users
Use Case
Your company does not want Sensitive data to be shared between users, by accident or on purpose.
Definitions
There are no extra definitions for this part of the blog series.
Notes
- There are no extra notes for this part of the blog series.
- It will take a minimum of 15 minutes after DLP policy creation for the account to take effect. It can take up to 24 hours for the policy to propagate in a tenant. This can take up to 7 days depending on how your tenant replication is configured on the backend.
Pre-requisites
- Have 2 Teams users you can use for testing.
- Have completed Part 1a of this blog series (Exact Data Matches)
DLP Creation
- On the left-hand navigation field, select Data Loss Protection.
- In the right-rand pain, select Policies and Create Policy
- First you need to Choose the information to Protect. Select Custom –> Custom Policy and then click Next.
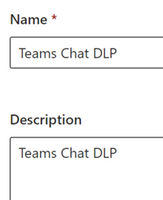
- Name your Policy and give it a description. Then click Next.
- Example = Name – Teams Chat DLP
- Example = Description – Teams Chat DLP
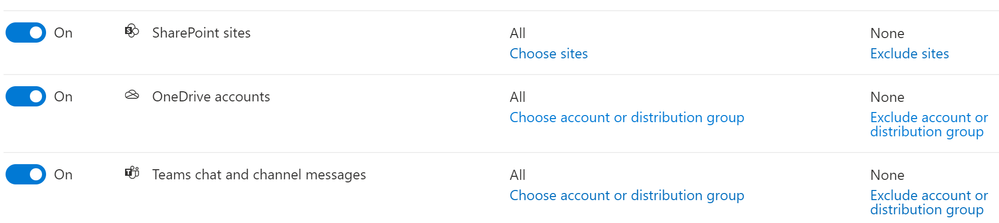
- Chose the Locations to apply the policy. For this DLP policy, we will deselect everything except SharePoint Sites, OneDrive accounts, and Teams chat and channel messages.
- Under Included, leave the default of All.
- Under Excluded, leave the default of None.
- Click Next.
- Note – to block files being shared in a Teams chat, you need to enable your DLP policy for SharePoint and Teams. There is more on this in the documentation in the Appendix
- Define DLP rules settings
- Click Create or Customize advanced DLP rules and click Next.
- Now click Create Rule.
c. In the Customize advanced DLP rules, click Create Rule
d. Name your Rule and give it a description.
i. Example = Name – Teams Chat DLP Rule
ii. Example = Description – Teams Chat DLP Rule
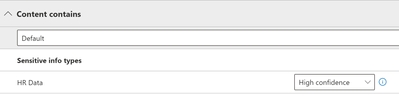
e. Under Conditions, click Add Condition and select Add -> Sensitive info types and select your SIT or Exact Data Match. I am selecting the SIT labeled “HR Data”. Let us place the confidence of this SIT to High Confidence.
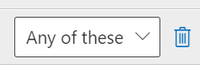
f. On the right-hand side you will see a drop down. Leave this at the default of Any of these.
g. Do not add a second Condition for this test, but you can add multiple Conditions for your own testing later-on.
h. Do not add an Exception. Again, you can do this for your own testing at a later time.
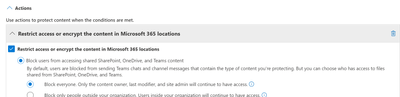
i. Under Actions, select Add an Action -> Restrict Access or Encrypt the content in Microsoft 365 location.
i. Select Block users and then select Block Everyone.
Note – If you have access to an external Exchange account for testing, feel free to select Block only people outside your organization.
j. Now go to User Notifications. Here you will set up the alerts to be sent to your administrator or compliance officer.
i. Select On.
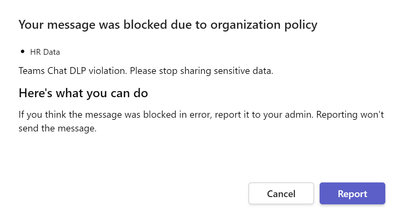
ii. Select Notify users in Office 365 service with a policy tip. This will alert the users that they have violated the DLP policy. Here is what I am placing in my policy tip – “Teams Chat DLP violation. Please stop sharing sensitive data.”
k. Leave the rest of the settings at their defaults. Click Save and then click Next.
- Now we arrive at the step to configure Test or turn on the policy. Let us enable Turn it on right away, and then click Next.
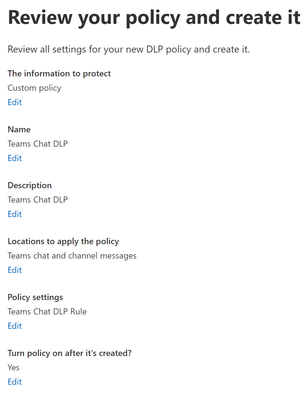
- Review your policy and create it. You will see a summary of what you have created. If everything looks correct, click Submit.
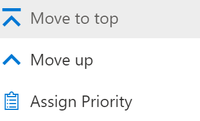
- In the Policies, click the 3 vertical dots next to your new policy.
- Select Move to top. This will place the policy in the 0 slot, which will give it priority over all DLP policies. From a testing perspective, this will force this policy to take effect before any other policies you might have created previously.
- Now wait between 15 minutes and 24 hours for your policy to be synchronized to your tenant. This can take up to 7 days depending on how your tenant replication is configured on the backend. You are now done with creating your Teams Chat DLP policy and are ready to move to the testing phase.
DLP Testing
- Open Microsoft Teams for your test user and create an with another test user. I am using Megan and Pradeep as my two test users. My test data belongs to user John Doe.
- Create a chat thread. This can be one directional (ex. Megan writing to Pradeep) or bi-directional (Megan and Pradeep writing back and forth). For my test, I create a bi-directional chat thread.
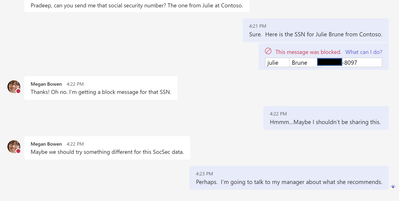
- Here is the Script of my text (Screenshot below)
- Megan – Pradeep, can you send me that social security number? The one from Julie at Contoso.
- Pradeep – Sure. Here is the SSN for Julie Brune from Contoso.
- Megan – Thanks! Oh no. I’m getting a block message for that SSN.
- Pradeep – Hmmm…Maybe I shouldn’t be sharing this.
- Megan – Maybe we should try something different for this SocSec data.
- Pradeep – Perhaps. I’m going to talk to my manager about what she recommends.
- Note – I am using this back-and-forth chat to not only prove that DLP works for Teams chats, but to leverage this Teams chat in future parts of this blog series.
- When you send the file with your sensitive information AND when you send the text with the information, you should receive a pop-up that looks something like that below.
- Pradeep will see this message
- When you click on the “what can I do” hyperlink in that pop-up, you will be brought to the notification we created earlier. You will notice for this test, we have just used the boilerplate information for “Here’s what you can do.” You can customize this in your own testing.
- Megan will see this message
You have now completed your testing of using DLP to block Teams Chats with sensitive data.
Appendix – Official Document Links
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.