- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 09 2023 03:42 AM
Can I configure something like SPF exception for particular incoming SMTP domains? I mean- if I receive emails from domains with not properly configured or without SPF records I don't want to have this emails in junk or quarantine. I think allow list is not good solution because I also don't know to bypass this emails without any kind of scanning. Can I achieve this functionality in EOP? I have this option in Forti Mail for example...
- Labels:
-
Exchange Online
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 09 2023 03:21 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 09 2023 04:10 PM
When an email is sent from a domain with no SPF published and DKIM not enabled, the emails fails authentication and may be delivered to Junk or Quarantine.
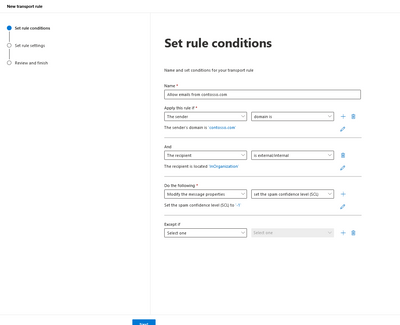
You can create a transport rule to set the SCL (spam confidence level) of emails sent from the domain to -1 but this is not recommended as all emails from the domain will not be filtered in this case. The screenshot below shows the configuration of the rule.
If the email will be coming from a specific static IP address, I will recommend you add the IP address to the allow list of the connection filter policy as only emails from the IP will be delivered and this will help should in case the domain get spoofed.
If I have answered your question, please mark your post as Solved
If you like my response, please give it a Like ![]()
Appreciate your Kudos! Proud to contribute!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 09 2023 04:24 PM
Solution- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 12 2023 05:10 PM - last edited on Feb 13 2023 11:26 AM by Eric Starker
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 12 2023 05:10 PM - last edited on Feb 13 2023 11:26 AM by Eric Starker
Hi Robert,
Yes, it is possible to configure SPF exceptions for specific incoming SMTP domains in Microsoft Exchange Online Protection (EOP). To do this, you need to create a custom connection filter that bypasses SPF checks for emails coming from specific domains. Here's how to create a custom connection filter:
-
Log in to the Microsoft 365 admin center.
-
Go to the Security & Compliance Center.
-
Go to Threat management > Policy > Connection filter.
-
Click the Add button to create a new connection filter.
-
Enter a name for the connection filter, and select the "Bypass SPF check" option.
-
In the "Apply this connection filter to" section, select the domains for which you want to bypass the SPF check.
-
Save the connection filter.
Once you have created the custom connection filter, EOP will bypass the SPF check for emails coming from the specified domains, and the emails will not be sent to the junk or quarantine folder.
Please note that bypassing the SPF check for specific domains can reduce the effectiveness of your spam and phishing protection, so it should only be used as a last resort if necessary. Additionally, make sure to regularly review and update your connection filters to ensure that they are effective in protecting your organization from unwanted email.
(external link removed by moderator)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 09 2023 04:24 PM
Solution