- Home
- Exchange
- Exchange Conversations
- Exchange online Admin Console (EAC) not accessible (403) with Exchange Admin permission
Exchange online Admin Console (EAC) not accessible (403) with Exchange Admin permission
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 05 2020 08:28 AM
Hi Everyone,
We are currently reordering our permission structure and want to use security groups to manage our roles. So we created a few security groups in Azure and assigned the necessary roles to them. This works very well, but the issue is, many groups have the "Exchange administrator" role and the members got this role, but they have no permission to open the EAC. They are able to manage the attributes from M365 Admin center or PowerShell, even if they open this link manually they able to open the new EAC (https://admin.exchange.microsoft.com), but the "old" EAC from the M365 Admin center is not accessible for them. We tried many possibilities to handle this issue, but we didn't find a solution yet.
My question is, how can we give permissions for our admins to open the EAC based on Azure AD roles? It's important to use the Azure roles because we want to manage these roles by security groups and in the future via PIM as well.
Thank you for the answers in advance!
- Labels:
-
Admin
-
Exchange Online
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 06 2020 12:12 AM
Exchange doesnt recognize Azure security groups, which probably explains what you are seeing. Well it does, but it's a mixed bag, and I think the official answer is still "unsupported". Try using mail-enabled security groups instead.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 06 2020 04:31 AM
Hello @Vasil Michev,
Thank you for your answer.
Maybe I described wrong what we want to set. We are utilizing Azure security groups and assign the Azure roles to the groups, thus the members of the groups will get the Azure roles. I know that is a preview feature, but it's working. I've checked and the admins have the appropriate roles in Azure Active Directory that the group provides for them. The exchange does recognize the Azure roles, and we have set the Exchange administrator roles the affected admins and that's the problem because they have no permission to open the EAC with the Exchange administrator role.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 06 2020 08:20 AM
Or in other words EAC does not recognize the assignment via security groups :) You can open a support case to get an official answer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 06 2020 09:20 AM
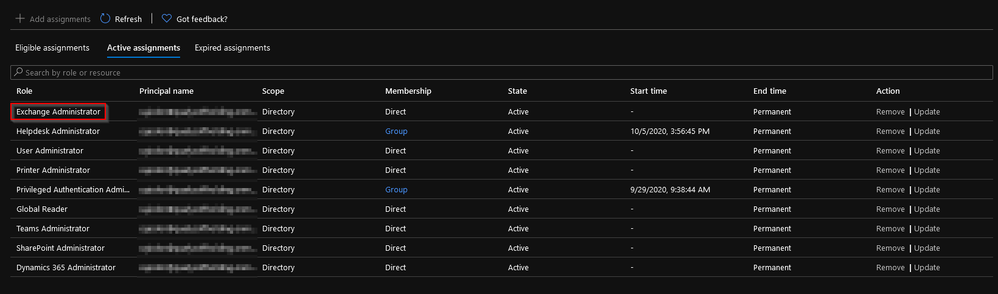
SolutionI think you still misunderstanding me. Yes, we are using sec groups to collect the people who are using more than one Azure ad role and we assign the Azure roles to the group, and then the members will inherit the roles. So, I know that the EAC do not recognize the sec groups memberships, it's a fact, but we are using roles, to give permission for the resource, not groups.
As you can see on the picture, the account has the Exchange administrator role, and this should recognize by the EAC. We are using this method to manage the roles.
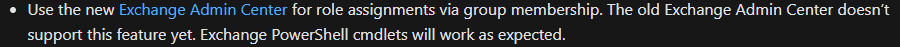
And now, I have to say thank you for your comments! :D Because I have read again the site that I put in this comment as link, and I found the solution in the "Known issues" section:
So, thank you for the help! :D
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 06 2020 09:20 AM
SolutionI think you still misunderstanding me. Yes, we are using sec groups to collect the people who are using more than one Azure ad role and we assign the Azure roles to the group, and then the members will inherit the roles. So, I know that the EAC do not recognize the sec groups memberships, it's a fact, but we are using roles, to give permission for the resource, not groups.
As you can see on the picture, the account has the Exchange administrator role, and this should recognize by the EAC. We are using this method to manage the roles.
And now, I have to say thank you for your comments! :D Because I have read again the site that I put in this comment as link, and I found the solution in the "Known issues" section:

So, thank you for the help! :D