- Home
- Exchange
- Exchange Team Blog
- Why Exchange Server updates matter
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
We have now published most of the information from this blog post as a part of our official documentation, You can find it here: Exchange Server update FAQ.
It is very important to keep updating your Exchange Servers to a supported Cumulative Update (CU). Simply put, your on-premises environments should always be ready to take an emergency security update (this applies to Exchange, Windows, and other Microsoft products you use on-premises). One thing we learned during the March 2021 release of Exchange Server security updates is that many of our customers were not ready to install security updates because they were not on supported cumulative update versions. With the threat landscape rapidly evolving, the importance of keeping your environment current should not be underestimated.
Please keep your Exchange Servers up to date. We want to continue helping you keep your environment secure, and this means your Exchange servers need to be up to date. This is a continuous process.
Once your Exchange servers are running a supported CU, ensure that the latest available Security Update (SU) is also installed. This will help address any vulnerabilities found since the release of the supported CU. To find recently released Exchange Server SUs, go to the Security Update Guide (filter on Exchange Server under Product Family). Exchange Server security updates are cumulative (an update released in April will also contain security fixes released in March, for example). We also announce all major updates on our blog.
We have prepared a set of questions and answers that cover what we hear most often about Exchange updates. If you are running into a different set of challenges keeping your environment up to date, please let us know in comments below!
Q&A
I updated my Exchange Servers a few months ago! How come they are ‘not supported’ today?
For versions of Exchange that are within mainstream support (see product lifecycle), Microsoft supports (releases relevant security fixes for) the two latest CUs. Sometimes the latest two CUs are referred to as “N and N-1”. As a current example, if the latest released CU is CU12 (‘N’), and the server version is Exchange Server 2019, then Microsoft at this time supports two Exchange Server 2019 CUs, N and N-1 (CU12 and CU11). When CU13 is released, the “supported CU window” will slide toward the newly released CU13 (and what used to be the N-1 supported CU, CU11, will become unsupported).
Why does Microsoft release updates so often?
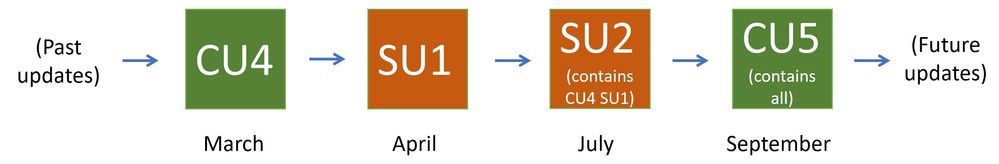
It is good that updates are released when issues are found. Microsoft (and other software vendors) release updates only when they are needed. CUs typically contain resolutions to feature problems that were reported to us by our customers (and can contain security updates from previous SUs) and are released twice a year (in H1 and H2). SUs are released only when actual security issues are found and fixed, and are typically released on a ‘patch Tuesday’. Let’s take an example of how a typical release flow for two CUs and two SUs we might release would look like:
- On a particular month (let’s say March), we might release CU4; CU4 is cumulative and will include fixes and updates from before.
- A month later we release CU4 SU1, a security update for CU4.
- In July we then release CU4 SU2, an additional security update for CU4. CU4 SU2 will include updates released in CU4 SU1 also.
- In September we release CU5, which will contain all updates released up to that point.
My Exchange Servers are working as expected, so why update them?
While we appreciate the ‘don’t fix what is not broken’ thinking, the reality is that keeping Exchange Server current allows you to ensure that it will keep working without major interruptions to functionality. Investing some time into Exchange Server maintenance (on your planned schedule) will give you a long-term benefit of well running system, with code as protected from vulnerabilities as you can get it.
Updating Exchange Server seems complicated; what exactly do I do?
Think of updating Exchange server in several stages:
- Take inventory: use the Exchange Server Health Checker script on GitHub to see if you are behind on your on-premises Exchange Server updates.
- Install updates: visit https://aka.ms/ExchangeUpdateWizard and choose your currently running CU and your target CU. Then click the “Tell me the steps” button, to get a list of steps to follow.
- Troubleshoot (if needed): follow the ExchangeUpdateWizard instructions and best practices for installation of updates carefully, including when to use an elevated command prompt. If you encounter errors during or after installation, see Repair failed installations of Exchange Cumulative and Security updates.
Why did Microsoft suddenly start releasing Exchange Server security updates?
Releasing security updates for Exchange Server is not new. Microsoft has been releasing Exchange Server updates on ‘patch Tuesday’ for years (when issues are found). Keeping up with these updates is a best practice.
How can I update Exchange Server when (insert 3rd party application name here) does not support either of the latest supported Exchange Server CUs?
Work with your 3rd party vendor to bring their software current in a timely manner. Consider that your Exchange environment contains a lot of valuable company directory and messaging information. Your priority should be to keep your environment as secure as possible.
How can we stay current when we are a 24x7 business and have no time to take our servers down for maintenance?
Many customers require Exchange Server to work 24x7. In fact, our update process is designed for these high-demand businesses. You should use Database Availability Groups (DAGs) and put servers that you are updating in Maintenance mode to enable a graceful and non-disruptive update process for your users. See Performing maintenance on DAG members for more information.
If we are in Hybrid mode and don’t actively use our on-premises Exchange Server, do we still need to stay current?
Even if you are only using Exchange Server on-premises to manage Exchange-related objects, you need to keep the server current. Note that the Hybrid Configuration Wizard (HCW) does not need to be re-run after updates are installed.
I looked at recent security update releases and the Common Vulnerabilities and Exposures (CVE) severity was not very high; so why update?
Microsoft recommends that you apply all available security updates because it can be difficult to understand how even lower severity vulnerabilities disclosed in one month might interact with vulnerabilities disclosed and fixed a month later. An attack may trigger only specific low-impact functionality on a remote target machine and nothing else, causing the scoring for the CVE to be quite low one month. For example, in the following month an important issue with that functionality could be discovered, but it might be only triggered locally and require significant user interaction. That on its own might also not be scored highly. But if your software is behind in updates, these two issues could combine into an attack chain, thereby scoring at critical levels.
We applied mitigations for a recent security vulnerability. Why should we install (later released) updates for those same vulnerabilities?
Mitigations are a temporary form of protection that should be used until the actual code fix is released. Because mitigations do not address the actual vulnerability that is present in the code, they can (and sometimes do) get bypassed by threat actors attacking systems that are still vulnerable. Microsoft recommends to install the code fix for any vulnerability as soon as it is available. Mitigations should not be considered a long-term solution to vulnerable code.
We find it difficult to update because Active Directory (AD) schema extensions and Exchange installations require different teams to take action.
In cases where different teams need to perform separate actions to prepare for installation of Exchange Cumulative Updates (as those might require AD schema extension) – we recommend you request schema changes when we release new CUs that require them. Even if you do not need to update to the very latest CU (because last two CUs are supported for Exchange versions that are still within support lifetime) – the fact that Active Directory schema will be up to date means that if you do find that you need to install the latest CU, AD schema will already be updated. We release CUs twice a year and not all of them will require AD schema updates. You can track this here for Exchange 2016 and here for Exchange 2019.
We installed a previous CU on our server and then applied available SUs. We just updated our server to the latest CU available. Do we need to apply the SU for the latest CU too?
After a new CU is installed on the server, you always need to install the latest SUs available for that CU. Let us walk through a hypothetical Exchange Server 2019 scenario of this:
- In May, you installed CU9 (the latest available CU at the time) and all available SUs for CU9
- In June, we released CU10 for Exchange Server 2019
- In July, we released SUs that apply to both CU9 and CU10
- In July, you installed July SU to your Exchange 2019 CU9 server
- In August, you installed CU10 (the latest available CU in July)
- You now need to apply the latest SU that is available for Exchange Server 2019 CU10
We installed an SU for current CU last month. This month, a new SU is available for the same CU. Do we need to uninstall last month’s SU before installing a newer one for the same CU?
No, uninstallation of last month’s SU is not necessary. Simply install this month’s SU as it becomes available. Newer SU will contain last month’s SUs security fixes too.
When we release security updates for supported Exchange Server versions, we release them for the last two (supported) CUs. SUs are always CU specific. In other words – installing a later CU will require that any SU available for that CU be installed also, no matter if the SU for the latest and previous CU were released on the same day. If there are SUs for the CU your server is running, then you should install it. SUs will typically be ‘rolled into the CU’ at the next subsequent CU release (see Why does Microsoft release updates so often? question above).
Did Microsoft change how often Exchange CUs are released?
Yes, starting with 2022 H1 Cumulative Updates, we have moved to a release cadence of two CUs per year – releasing in H1 and H2 of each calendar year, with general target release dates of March and September. But our release dates are driven by quality, so we might release updates in April or October, or some other month, depending on what we’re delivering. With these service model changes, being current still means running the latest CU or the one immediately preceding it (N or N-1), but the ‘currency window’ is now extended from 6 months to 1 year.
Do we need to install SUs on all Exchange Servers within our organization? What about ‘Management Tools only’ machines?
Our recommendation is to install Security Updates on all Exchange Servers as well as servers or workstations running Exchange Management Tools only, which will ensure that there is no incompatibility between management tools clients and servers.
We installed current CU and SU releases and are fully up to date. Is there anything else that we should do?
Depending on the particular environment, addressing certain vulnerabilities might require additional actions to be performed by the Exchange administrator. To make sure that you have performed all of the actions necessary after relevant Security Updates were installed, please run the Exchange Server Health Checker script. Please also ensure that you update the Windows operating system that Exchange Server is running on, as vulnerabilities in the OS can be used as a part of attack chain too.
The Exchange Team
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.