Update - 4/2/18: Hybrid modern authentication for Outlook mobile with Exchange on-premises mailboxes is now generally available. For more information see the A new architecture for Exchange hybrid customers enables Outlook mobile and security.
As announced at Ignite 2017, Outlook for iOS & Android will soon be fully powered by the Microsoft Cloud for hybrid Exchange on-premises customers. These updates will also provide support for management via Microsoft Intune, included in Enterprise Mobility + Security (EMS). This article outlines what the changes will provide for customers and how to apply to participate in the Technology Adoption Program (TAP) for this new architecture.
Overview of the new Microsoft Cloud architecture for Exchange Server customers
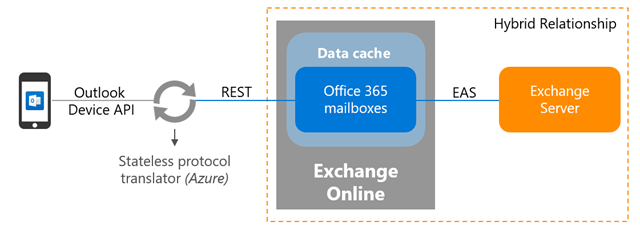
For Exchange Server mailboxes, Outlook mobile’s new architecture will be similar in design to our legacy architecture. However, as the service is now built directly into the Microsoft Cloud (using Office 365 and Azure) customers receive the additional benefits of security, privacy, built-in compliance and transparent operations that Microsoft commits to in the Office 365 Trust Center and Azure Trust Center.
Data passing from Exchange Online to the Outlook app is passed via a TLS-secured connection. The protocol translator running on Azure serves to route data, commands and notifications, but has no ability to read the data itself.
The Exchange ActiveSync connection between Exchange Online and the on-premises environment enables synchronization of the user's on-premises data and includes 4 weeks of email, all calendar data, all contact data, and out of office status into your Exchange Online tenant. This data will be removed automatically from Exchange Online after 30 days of inactivity.
Data synchronization between the on-premises environment and Exchange Online happens independent of user behavior. This ensures that we can send new messages to the devices very quickly.
Benefits of the new Microsoft Cloud-based architecture
In order to deliver the best possible experience for our customers, we built Outlook for iOS & Android as a cloud-backed application. This means your experience consists of a locally installed app powered by a secure and scalable service running in the Microsoft Cloud.
Processing information in the Microsoft Cloud enables advanced features and capabilities, such as the categorization of email for the Focused Inbox, customized experience for travel and calendar, improved search speed and more. It enhances Outlook’s performance and stability, relying on the cloud for intensive processing and minimizing the resources required from users' devices. Lastly, it allows Outlook to build features that work across all email accounts, regardless of the technological capabilities of the underlying servers (e.g. different versions of Exchange, Office 365, etc.).
Specifically, this new architecture has the following improvements:
EMS Support: Customers can take advantage of Microsoft Enterprise Mobility + Security (EMS) including Microsoft Intune and Azure Active Directory Premium to enable Conditional Access and Intune App Protection policies to control and secure corporate messaging data on the mobile device.Fully powered by Microsoft Cloud: The mailbox cache is moved off AWS, and is now built natively in Exchange Online. It provides the benefits of security, privacy, compliance and transparent operations that Microsoft commits to in theOffice 365 Trust Center.OAuth protects user’s passwords: Outlook will leverage OAuth to protect user’s credentials. OAuth provides Outlook with a secure mechanism to access the Exchange data without ever touching or storing a user’s credentials. At sign in, the user authenticates directly against an identity platform (either Azure AD or an on-premises identity provider like ADFS) and receives an access token in return, which grants Outlook access to the user’s mailbox or files. At no time does the service have access to the user’s password in any form.Provides Unique Device IDs: Each Outlook connection will be uniquely registered in Microsoft Intune and be able to be managed as a unique connection.Unlocks new features on iOS & Android: This update will enable the Outlook app to take advantage of native Office 365 features that are not supported in Exchange on-premises today, such as leveraging full Exchange Online search and Focused Inbox. These features will only be available when using the Outlook apps for iOS & Android.
Note: Device management through the Exchange Admin Center will not be possible; Intune is required to manage mobile devices.
Other notes about Outlook mobile, Exchange Server & EMS
Managing mobile devices: Microsoft Intune is the only way to manage the devices and perform wipe operations. Individual device IDs will not be manageable in the on-premises Exchange environment.Support for Exchange Server 2007: Users with an Exchange Server 2007 mailbox will be unable to access their email and calendar in Outlook for iOS & Android as Exchange Server 2007 is not in mainstream support.Support for Exchange Server 2010: Exchange Server 2010 SP3 is out of mainstream support and will not work with Intune-managed Outlook mobile. In this architecture, Outlook mobile utilizes OAuth as the authentication mechanism. One of the on-premises configuration changes performed enables the OAuth endpoint to the Microsoft Cloud as the default authorization endpoint. When this change is made, clients can start negotiating the use of OAuth. As this is an organization-wide change, Exchange 2010 mailboxes fronted by either Exchange 2013 or 2016 will incorrectly think they can perform OAuth and will end up in a disconnected state as Exchange 2010 does not support OAuth as an authentication mechanism.
Technical and licensing requirements
Our new architecture will have the following technical requirements:
Exchange on-premises setup:A minimum of cumulative update (CU) deployment on all Exchange servers of Exchange Server 2016 CU6 or Exchange Server 2013 CU17.All Exchange 2007 or Exchange 2010 servers must be removed from the environment.
Active Directory Synchronization: Active Directory synchronization with Azure Active Directory via Azure AD Connect. Ensure the followingattributesare synchronized:Office 365 ProPlusExchange OnlineExchange Hybrid writebackAzure RMSIntune
Exchange hybrid setup: Requires full hybrid relationship between Exchange on-premises with Exchange Online.Hybrid Office 365 tenant is required that is configured in full hybrid configuration mode and is setup as specific in thehybrid configuration guide.Requires an Office 365 Enterprise, Business or Education tenant.The mailbox data will be synchronized in the same datacenter region where that Office 365 tenant is setup. For more about where Office 365 data is located, visit the “Where is my data?”section Office 365 Trust Center.Use of Office 365 US Government Community and Defense, Office 365 Germany and Office 365 China operated by 21Vianet tenants will not be supported at launch.The external URL hostname for EAS must be published as a service principal to AAD through the Hybrid Configuration Wizard.Autodiscover and EAS namespaces must be accessible from the Internet and support anonymous connections.
EMS setup: Both cloud only and hybrid deployment of Intune is supported (MDM for Office 365 is not supported).Office 365 licensing*: One of the following Office 365 licenses for each user that includes the Office client applications required for Outlook for iOS & Android commercial use:Commercial: Enterprise E3, Enterprise E5, ProPlus or Business licensesGovernment: U.S. Government Community G3, U.S. Government Community G5Education: Office 365 Education E3, Office 365 Education E5
EMS licensing*: One of the following licenses for each user:Intune standalone + Azure Active Directory Premium standaloneEnterprise Mobility + Security E3, Enterprise Mobility + Security E5
*Microsoft Secure Productive Enterprise (SPE) includes all licenses necessary for Office 365 and EMS.
Data Security, Access, and Auditing Controls
Data within Exchange Online is protected via a variety of mechanisms. The Content Encryption whitepaper discusses how BitLocker is used for volume-level encryption. Service Encryption with Customer Key as discussed in the Content Encryption whitepaper will be supported in this architecture, but note that the user must have an Office 365 Enterprise E5 (or the corresponding versions of those plans for Government or Education) license to have an encryption policy assigned.
By default, Microsoft engineers have zero standing administrative privileges and zero standing access to customer content in Office 365. The Admin Access whitepaper discusses personnel screening, background checks, Lockbox and Customer Lockbox, and more.
ISO Audited Controls on Service Assurance documentation provides the status of audited controls from global information security standards and regulations that Office 365 has implemented.
Participating in the Technology Adoption Program (TAP)
Prior to rolling this updated architecture out to all customers, we are looking for customers to participate in the TAP. The TAP will allow Microsoft to work closely with customers to deploy the solution, and validate that it meets the needs and requirements of our customers.
What is in it for TAP customers:
Direct engagement and support from product engineeringDeployment assistance and supportEarly product trainingRegular conference callsOpportunity to provide input and feedback that will be integrated into the product
What do customers have to commit to in order to participate in the TAP:
Must sign a non-disclosure agreement with MicrosoftWilling to work closely with Microsoft during TAP program, share any issues, bugs and feedbackCode Deployment: Must deploy pre-production Exchange Server software in production.Wiling to deploy more than 25 devices utilized by real-world usersDeploy to production mailboxes that vary in size (medium, large, and very large)
To nominate yourself for the TAP, please work with your account team.
Additional technical requirements for participating in the TAP
In addition to the evergreen technical requirements outlined above, these additional requirements are necessary during the TAP program period:
Authentication support: OAuth is the only supported authentication mechanism.Exchange mobile device access policies (also known as ABQ policies): these are not supported. ABQ policies from Exchange Server on-premises will block syncs from cloud. ABQ policies setup in Office 365 will not be enforced.Exchange mobile device mailbox policies (also known as EAS policies): these will not be enforced by Outlook mobile. This means users must be managed by Intune to receive security policies.
If you have any questions, please let us know.
Ross Smith IV
Principal Program Manager
Office 365 Customer Experience